Intel CPUs Vulnerable to New 'SGAxe' and 'CrossTalk' Side-Channel Attacks
EPSS
Percentile
19.4%
Cybersecurity researchers have discovered two distinct attacks that could be exploited against modern Intel processors to leak sensitive information from the CPU’s trusted execution environments (TEE).
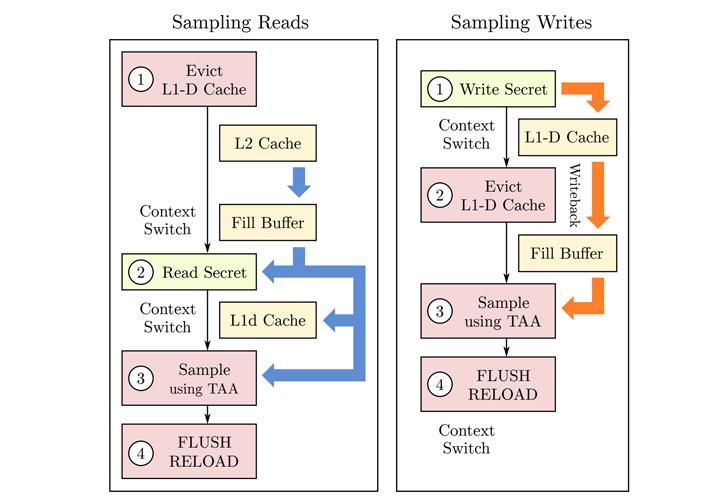
Called SGAxe, the first of the flaws is an evolution of the previously uncovered CacheOut attack (CVE-2020-0549) earlier this year that allows an attacker to retrieve the contents from the CPU’s L1 Cache.
“By using the extended attack against the Intel-provided and signed architectural SGX enclaves, we retrieve the secret attestation key used for cryptographically proving the genuinity of enclaves over the network, allowing us to pass fake enclaves as genuine,” a group of academics from the University of Michigan said.
The second line of attack, dubbed CrossTalk by researchers from the VU University Amsterdam, enables attacker-controlled code executing on one CPU core to target SGX enclaves running on a completely different core, and determine the enclave’s private keys.
A TEE, like Intel’s Software Guard Extensions (SGX), refers to a secure enclave, an area within a processor that ensures confidentiality and integrity of code and data. It offers safeguards against the modification of sensitive software and data by malicious actors that may have broken into the target (virtual) machine.
SGAxe Attack: Extracting Sensitive Data From SGX Enclaves
SGAxe builds on the CacheOut speculative execution attack to steal SGX data. According to the researchers, while Intel took steps to address side-channel attacks against SGX via several microcode updates and new architectures, the mitigations have proven ineffective.
That exploit, as a result, results in a transient execution attack that can recover SGX cryptographic keys from a fully updated Intel machine, which is trusted by Intel’s attestation server.
Attestation is a mechanism offered as part of SGX that lets enclaves prove to third parties that they have been correctly initialized on a genuine Intel processor. The idea is to ensure that the software running inside the CPU hasn’t tampered with and to have increased confidence that the software is running inside the enclave.
“In a nutshell, we use CacheOut to recover the sealing keys from within the address space of Intel’s production quoting enclave,” the researchers stated. “Finally, we use the recovered sealing keys in order to decrypt the long term storage of the quoting enclave, obtaining the machines EPID attestation keys.”
By breaking this trust, SGAxe makes it easy for an attacker to create a rogue enclave that passes Intel’s attestation mechanism, resulting in loss of security guarantees.
“With the machine’s production attestation keys compromised, any secrets provided by [the] server are immediately readable by the client’s untrusted host application, while all outputs allegedly produced by enclaves running on the client cannot be trusted for correctness,” the researchers said. “This effectively renders SGX-based DRM applications useless, as any provisioned secret can be trivially recovered.”
Although Intel issued fixes for CacheOut back in January via a microcode update to OEM vendors and subsequently via BIOS updates to end-users, mitigations for SGAxe will require patching the root cause behind CacheOut (aka L1D Eviction Sampling).
“It is important to note that SGAxe relies on CVE-2020-0549 which has been mitigated in microcode (confirmed by the researchers in their updated CacheOut paper) and distributed out to the ecosystem,” Intel said in a security advisory.
The chipmaker will also perform a Trusted Compute Base (TCB) recovery to invalidate all previously signed attestation keys.
“This process will ensure that your system is in a secure state such that your system is able to use remote attestation again,” the researchers stated.
CrossTalk Attack: Leaking Information Across CPU cores
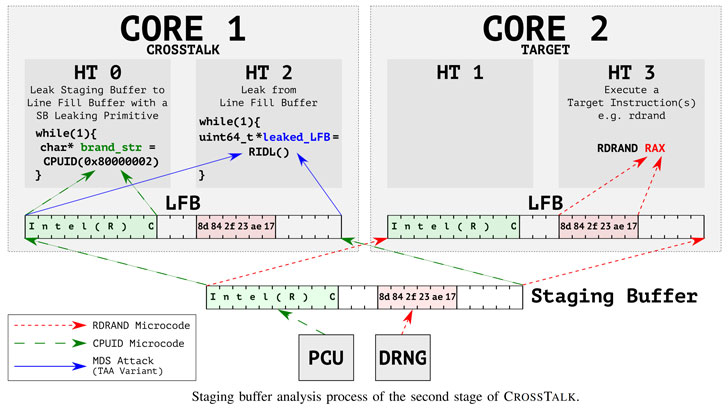
CrossTalk (CVE-2020-0543), the second SGX exploit, is what the VU University calls an MDS (Microarchitectural Data Sampling) attack. It takes advantage of a “staging” buffer that’s readable across all CPU cores to mount transient execution attacks across the cores and extract the entire ECDSA private key of a secure enclave running on a separate CPU core.
“The staging buffer retains the results of previously executed offcore-instructions across all CPU cores,” the researchers observed. “For instance, it contains the random numbers returned by the offcore hardware DRNG, bootguard status hashes, and other sensitive data.”
Put differently, CrossTalk works by reading the staging buffer during transient execution in order to leak sensitive data accessed by previously executed victim instructions.
The fact that the buffer retains output from RDRAND and RDSEED instructions makes it possible for an unauthorized party to track the random numbers generated, and therefore compromise the cryptographic operations that underpin the SGX enclave, including the aforementioned remote attestation process.
With Intel CPUs released from 2015 to 2019, counting Xeon E3 and E CPUs, susceptible to the attacks, VU University researchers said it shared with Intel a proof-of-concept demonstrating the leakage of staging buffer content in September 2018, followed by a PoC implementing cross-core RDRAND/RDSEED leakage in July 2019.
“Mitigations against existing transient execution attacks are largely ineffective,” the team summarized. “The majority of current mitigations rely on spatial isolation on boundaries which are no longer applicable due to the cross-core nature of these attacks. New microcode updates which lock the entire memory bus for these instructions can mitigate these attacks—but only if there are no similar problems which have yet to be found.”
In response to the findings, Intel addressed the flaw in a microcode update distributed to software vendors yesterday after a prolonged 21-month disclosure period due to the difficulty in implementing a fix.
The company has recommended users of affected processors update to the latest version of the firmware provided by system manufacturers to address the issue.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.