Warning — Hackers Exploiting New Windows Installer Zero-Day Exploit in the Wild
EPSS
Percentile
71.8%
Attackers are actively making efforts to exploit a new variant of a recently disclosed privilege escalation vulnerability to potentially execute arbitrary code on fully-patched systems, once again demonstrating how adversaries move quickly to weaponize a publicly available exploit.
Cisco Talos disclosed that it “detected malware samples in the wild that are attempting to take advantage of this vulnerability.”
Tracked as CVE-2021-41379 and discovered by security researcher Abdelhamid Naceri, the elevation of privilege flaw affecting the Windows Installer software component was originally resolved as part of Microsoft’s Patch Tuesday updates for November 2021.
However, in what’s a case of an insufficient patch, Naceri found that it was not only possible to bypass the fix implemented by Microsoft but also achieve local privilege escalation via a newly discovered zero-day bug.
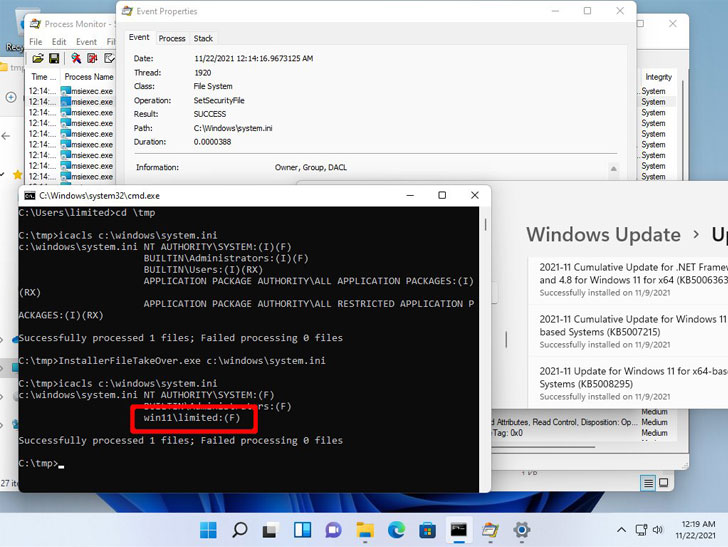
The proof-of-concept (PoC) exploit, dubbed “InstallerFileTakeOver,” works by overwriting the discretionary access control list (DACL) for Microsoft Edge Elevation Service to replace any executable file on the system with an MSI installer file, allowing an attacker to run code with SYSTEM privileges.
An attacker with admin privileges could then abuse the access to gain full control over the compromised system, including the ability to download additional software, and modify, delete, or exfiltrate sensitive information stored in the machine.
“Can confirm this works, local priv esc. Tested on Windows 10 20H2 and Windows 11. The prior patch MS issued didn’t fix the issue properly,” tweeted security researcher Kevin Beaumont, corroborating the findings.
Naceri noted that the latest variant of CVE-2021-41379 is “more powerful than the original one,” and that the best course of action would be to wait for Microsoft to release a security patch for the problem “due to the complexity of this vulnerability.”
“We are aware of the disclosure and will do what is necessary to keep our customers safe and protected,” a Microsoft spokesperson told The Hacker News via email. “An attacker using the methods described must already have access and the ability to run code on a target victim’s machine.”
Update: 0patch has issued a free micropatch to remediate the “InstallerFileTakeOver” zero-day flaw in Windows Installer component that could be abused by a local unprivileged user to overwrite an existing system executable and then arbitrarily change its contents to gain SYSTEM permissions.
“It doesn’t take a lot of imagination to see that taking over an executable file that is being used by a privileged process can get one’s code executed with such process’ privileges,” 0patch’s Mitja Kolsek said in a write-up published Thursday.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.