
Mitigating the Risk of Zero-Day Vulnerabilities by using Compensating Controls
EPSS
Percentile
100.0%
Zero-day vulnerability attacks have emerged as a major cybersecurity threat in the last few years. Organizations most often targeted include large enterprises and government/Federal agencies. However, any organization, regardless of its size, business, or industry, is a potential target for zero-day threats.
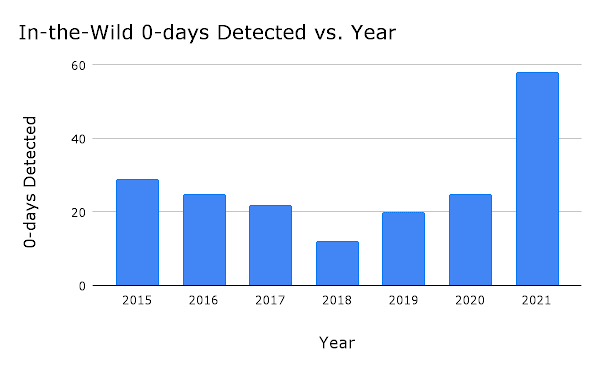
Most notably, already publicly disclosed. This means that one out of every fourzero-day exploits detected could potentially have been avoided if a more thorough investigation and patching effort had been pursued. In 2021, around 58 zero-day vulnerabilities were reported, more than double the total for the previous year. This is a definite cause for alarm. As of June 2022, Google’s project had identified 18 zero-day vulnerabilities so far this year.
Here are some well-known examples of zero-day attacks:
- Most recently, the Follina zero-day vulnerability
- Log4j (2021)
- Chrome (2021)
- Zoom (2020)
- Apple iOS (2020)
- Microsoft Windows, Eastern Europe (2019)
Why Are Zero-Day Attacks/Exploits so Dangerous?****
The biggest challenge in cybersecurity remains to secure what can’t be seen.
Zero-day attacks occur without warning, which makes them difficult to protect against. They take advantage of previously unknown vulnerabilities that have yet to be patched. In some cases, the software vendor is not even aware that the weakness exists.
The time between initial disclosure of a new vulnerability and its exploitation is shrinking. Yet the time to fix a vulnerability is not shrinking at the same rate. This gives attackers ample time to run rampant and launch zero-day attacks on defenseless targets. Unfortunately, it can still take days, weeks, or even months for fixes to be released. An enterprise may be forced to use the vulnerable/compromised software that entire time, exposing both its mission critical machines and sensitive data.
Even worse, once a zero-day patch is released, not all organizations are quick to implement it.
How Qualys Policy Compliance Helps Combat Zero-Day Threats
Qualys Policy Compliance is a next-generation solution for continuous cyber risk reduction and effective compliance with internal policies, industry mandates, and government regulations. It helps enterprises of any size to respond to zero-day threats. Here’s how:
Detecting New Vulnerabilities ****
The Qualys Research Team analyzes zero-day vulnerabilities published from various sources (e.g. Microsoft Patch Tuesday), including vendor advisories that help accurately detect these vulnerabilities. They identify workarounds and create compensatory controls accordingly which help to detect these vulnerabilities in the IT environment.
Mitigating Risk with Compensating Controls ****
Qualys Policy Compliance (PC) has a rich library of security controls that can be used to compensate for various zero-day vulnerabilities across different technologies and platforms. Qualys continuously releases new compensatory controls for new zero-day vulnerabilities as soon as a vulnerability is disclosed where no patch is yet available.
While no organization can completely protect themselves from a zero-day attack, organizations are able to detect new zero-day vulnerabilities and mitigate the risk associated with them with Qualys PC compensatory controls.
Here is a current list of current zero-day vulnerabilities for which Qualys PC has compensatory controls.
Zero-day Vulnerabilities, 2020-2022
Here is a listing of zero-day threats disclosed over the past three years, with links to Qualys blogs analyzing the CVEs (where applicable).
| CVE ID | Vulnerability name | Control ID | Control Title |
|---|---|---|---|
| CVE-2022-30190 | Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability (CVE-2022-30190) AKA “Follina” | 24074 | Status of the 'Microsoft Support Diagnostic Tool (MSDT)' service |
| CVE-2022-20695 | Cisco Wireless LAN Controller Management Interface Authentication Bypass Vulnerability | 23670 | Status of mac filter compatibility mode |
| CVE-2022-22965 | Spring framework RCE | 23425 | List of Java versions and processes present on the host |
| CVE-2021-4034 | PwnKit: Local Privilege Escalation Vulnerability | 22844 | Status of the SUID bit for /usr/bin/pkexec |
| CVE-2021-4104 | |||
| CVE-2021-44228 | |||
| CVE-2021-45046 | |||
| CVE-2021-45105 | Log4j Remote Code Execution (RCE) | 22639 | Detection of the Apache Log4j Remote Code Execution (RCE) vulnerability (Log4Shell) (Linux) |
| CVE-2021-4104 | |||
| CVE-2021-44228 | |||
| CVE-2021-45046 | |||
| CVE-2021-45105 | Log4j Remote Code Execution (RCE) | 22638 | Detection of the Apache Log4j Remote Code Execution (RCE) vulnerability (Log4Shell) (Windows) |
| CVE-2021-34527 | Windows Print Spooler Remote Code Execution Vulnerability | 21711 | Status of the 'Allow Print Spooler to accept client connections' group policy setting |
| CVE-2021-34527 | 19071 | Status of the 'Point and Print Restrictions: When updating drivers for an existing connection' setting | |
| CVE-2021-34527 | 19070 | Status of the 'Point and Print Restrictions: When installing drivers for a new connection' setting | |
| CVE-2021-34527 | 1368 | Status of the 'Print Spooler' service | |
| CVE-2020-10148 | SolarWinds Orion API Authentication Bypass Vulnerability | 20645 | Status of 'match-url' for rewrite rule 'PassValidSkipi18nRequest' where 'type' is None (Site-Level) |
| CVE-2020-10148 | 20644 | Status of 'match-url' for rewrite rule 'PassValidi18nRequest' where 'type' is None (Site-Level) | |
| CVE-2020-10148 | 20643 | Status of 'match-url' parameter for rewrite rule 'BLockOtherSkipi18nRequest' where 'statuscode' is 403 (Site-Level) | |
| CVE-2020-10148 | 20642 | Status of 'match-url' parameter for rewrite rule 'BLockOtheri18nRequest' where 'statuscode' is 403 (Site-Level) | |
| CVE-2020-10148 | 20641 | Status of 'match-url' parameter for rewrite rule 'BLockInvalidAxdRequest' where 'statuscode' is 403 (Site-Level) | |
| CVE-2020-11993 | Apache HTTPD Server HTTP/2 module memory crash | 19188 | The Status of the 'LogLevel' directive in the Apache configuration file (Server Level) |
| CVE-2020-9490 | Apache HTTPD Server HTTP/2 push crash | 19187 | Status of the 'H2Push' directive in the apache configuration file (Server Level) |
| CVE-2020-16898 | Windows TCP/IP Remote Code Execution Vulnerability | 19571 | Status of the 'RA Based DNS Config (RFC 6106)' parameter of network interface (Qualys Agent only) |
| CVE-2020-1350 | KB4569509: DNS Server Vulnerability | 18935 | Status of the 'TcpReceivePacketSize' parameter within the 'HKLM\System\CurrentControlSet\Services\DNS\Parameters' registry key |
Identifying Compensatory Controls ****
Using Qualys Policy Compliance’s new user interface, users will be able to verify the compliance posture of these controls by just looking at the CVEID/vulnerability unique identifier. As demonstrated below, It will be easy to search it by using the QQL token control.vulnerabiity.cveId: and then to create a dashboard from the results (see below).
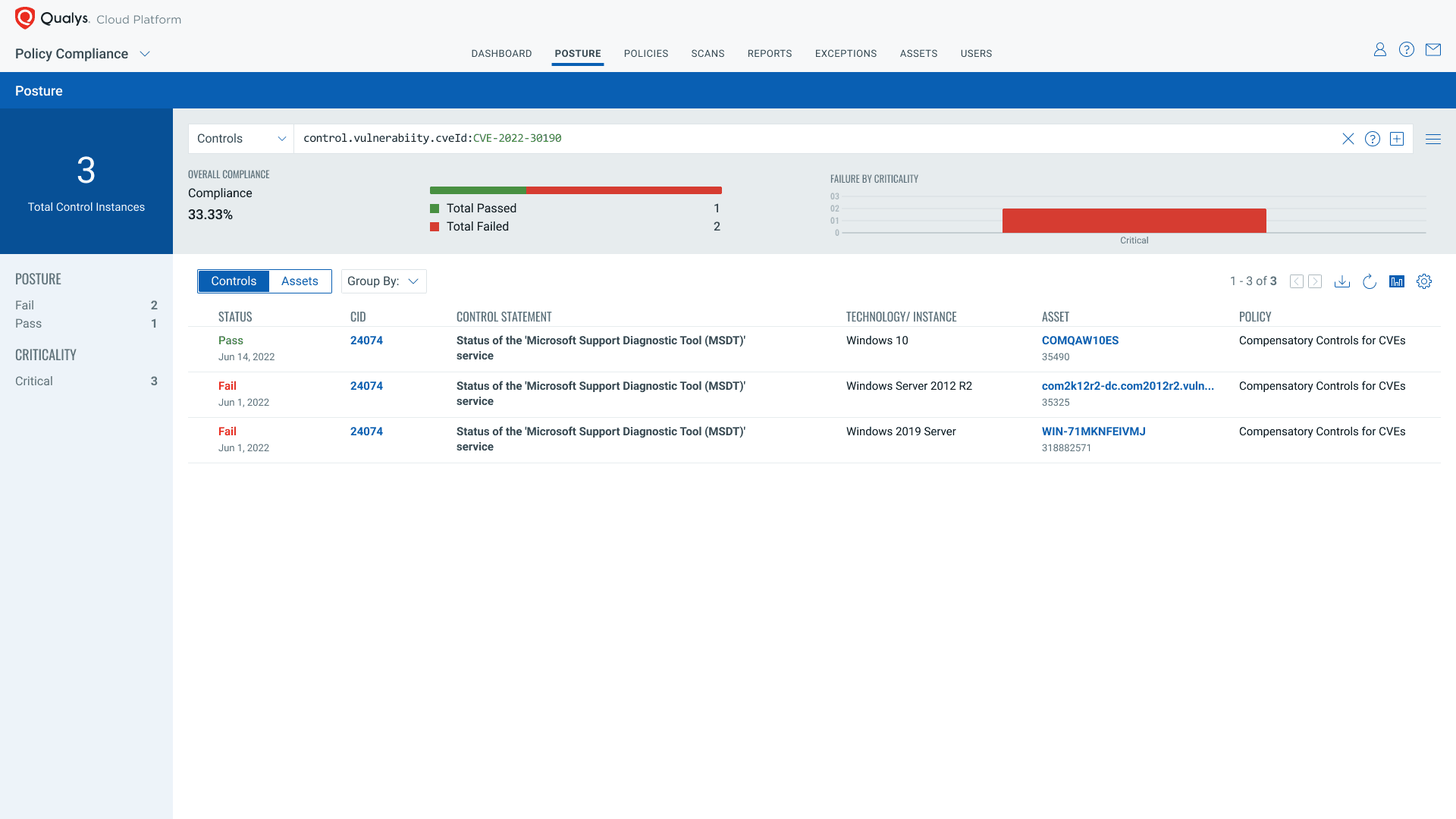 Identifying the compensatory controls using the CVE ID
Identifying the compensatory controls using the CVE ID
Benefit of Qualys Policy Compliance for Zero-Day Threats****
The main benefit of Qualys Policy Compliance is “Defense in Depth”.
Enterprises can make their security architecture stronger by assessing and fixing any misconfigurations, and then deploy patches easily once they are available, to reduce the organization’s overall cyber risk.
The initial assessment gives Cybersecurity teams insights into their current security posture. It plays an important role in mitigating the risk posed by zero-day vulnerabilities while the IT environment is vulnerable and until a vendor patch is released. However, organizations can add one more layer of security to their environment by leveraging Qualys PC controls to identify misconfigurations and provide the solution to mitigate them. Qualys researchers work around the clock analyzing zero-day vulnerabilities and release configuration assessment controls to detect and mitigate publicly known zero-day vulnerabilities.
Remediate Misconfigurations using Qualys Policy Compliance AutoRemediation ****
Qualys Policy Compliance doesn’t just detect misconfigurations associated with zero-day vulnerabilities, but also remediates them at scale using its AutoRemediation feature. After fixing the misconfiguration with AutoRemediation, users have reduced the overall risk posed by any particular vulnerability.
Let’s examine a specific example, using the recently disclosed zero-day vulnerability commonly known as Follina.
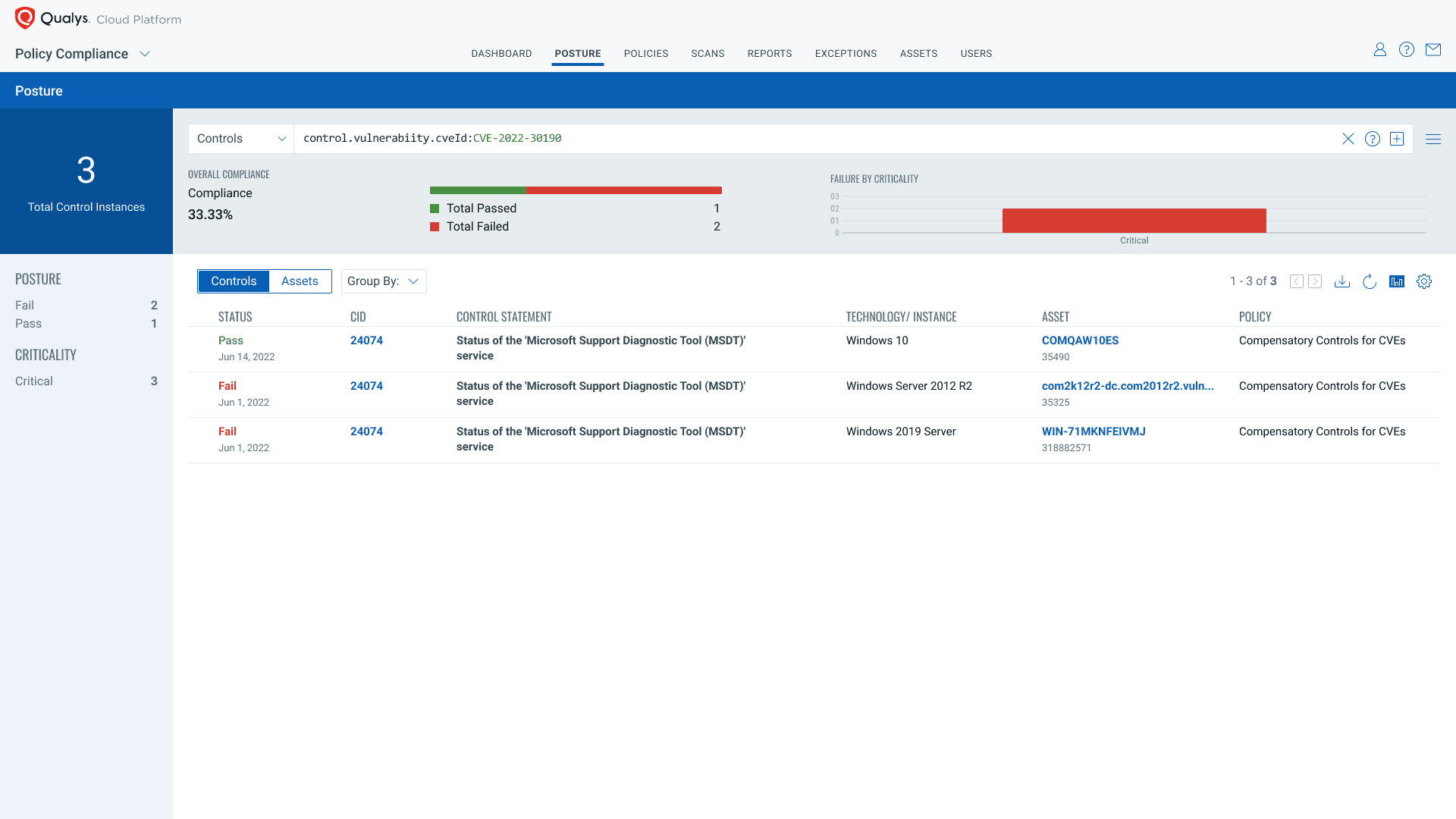 Security posture of compensating controls for Follina vulnerability
Security posture of compensating controls for Follina vulnerability
With misconfigurations associated with Follina, the risk is high:
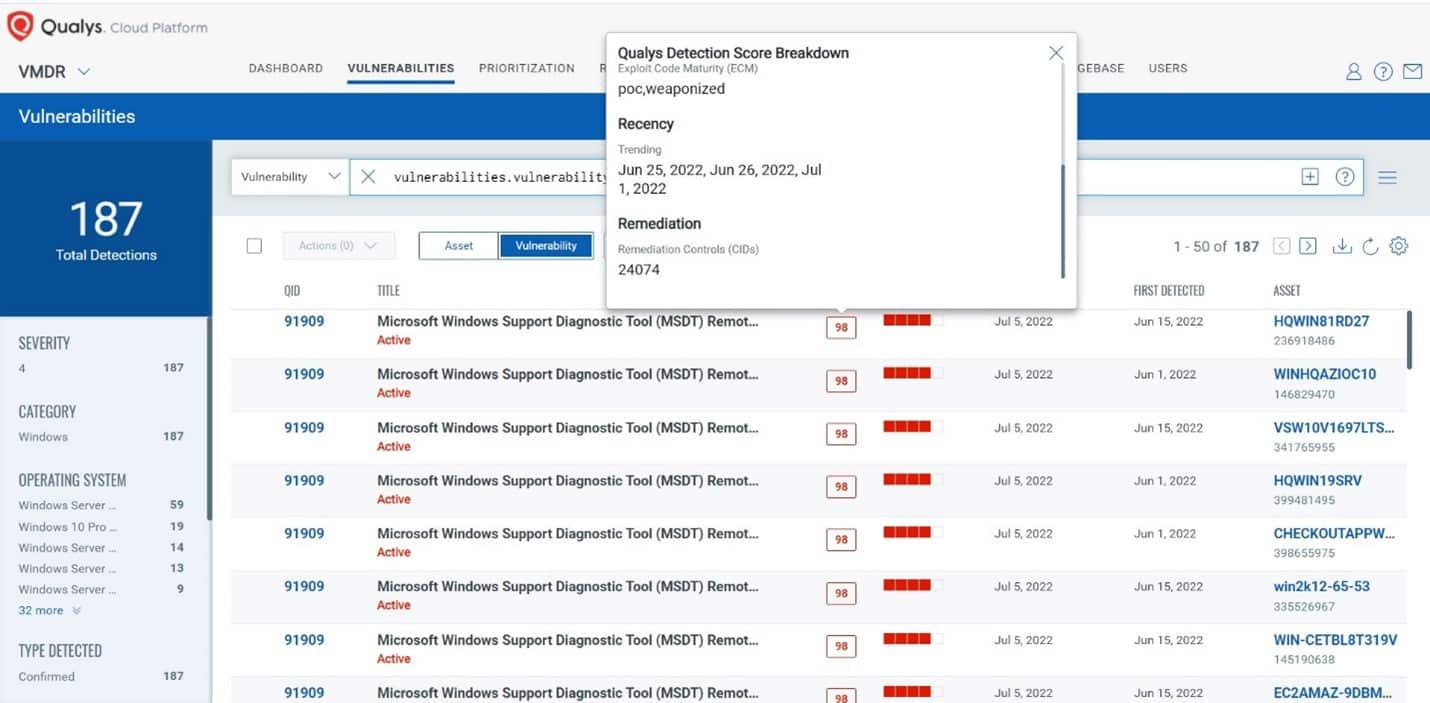 Cyber risk from Follina is high… without a fix
Cyber risk from Follina is high… without a fix
The control has failed. The following series of screenshots show how users can remediate the control using Qualys PC Auto-Remediation:
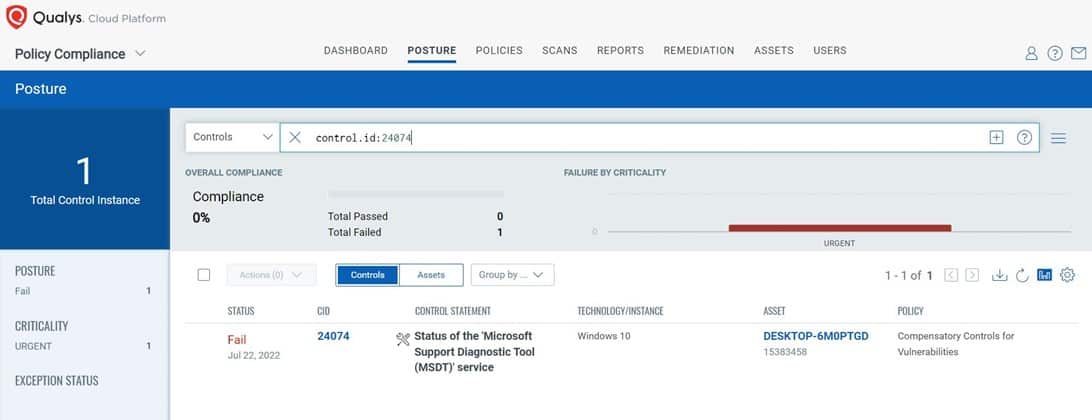 Step 1: Assess the misconfigured control
Step 1: Assess the misconfigured control 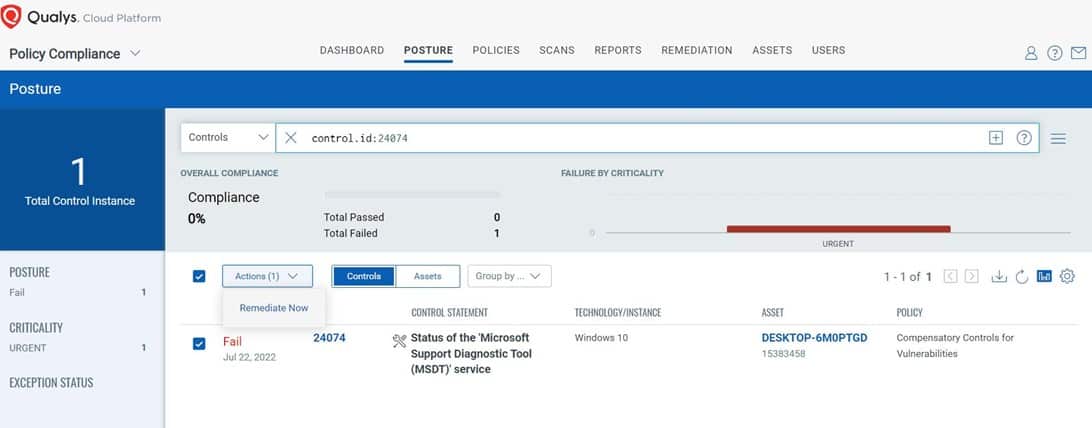 Step 2: Choose to remediate the failure
Step 2: Choose to remediate the failure 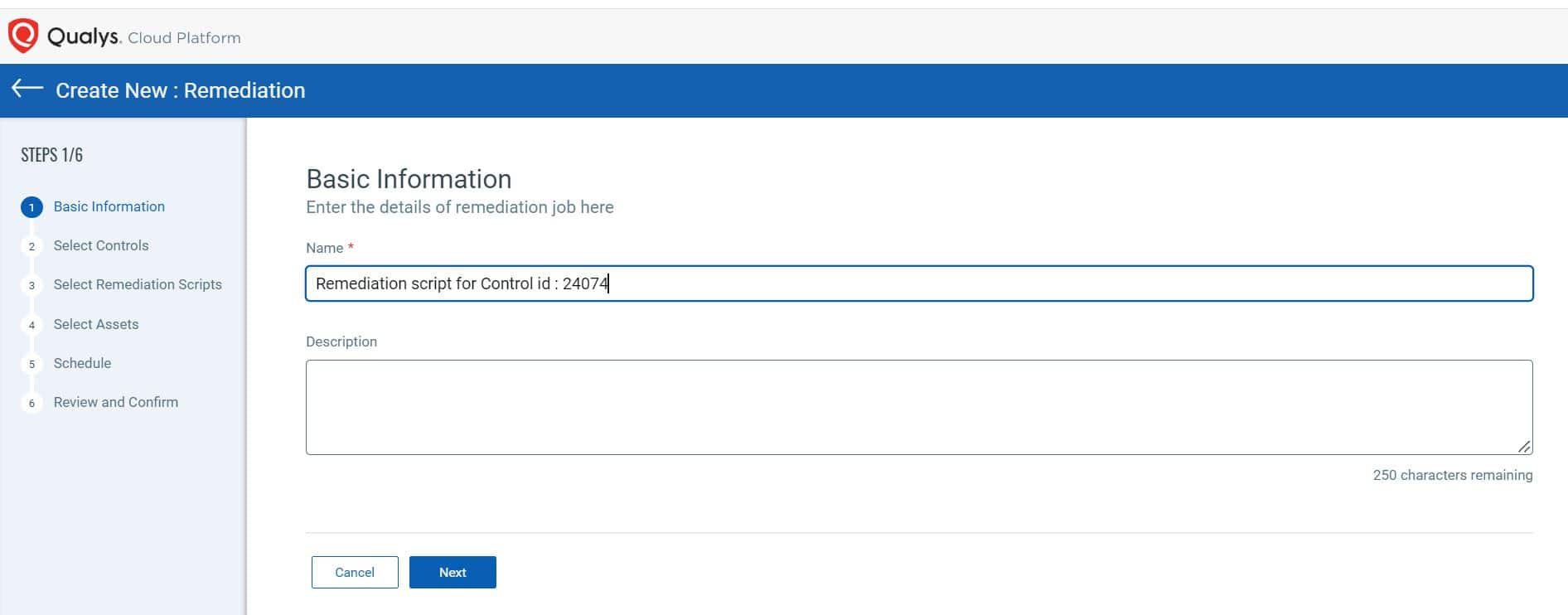 Step 3: Name the remediation Job
Step 3: Name the remediation Job 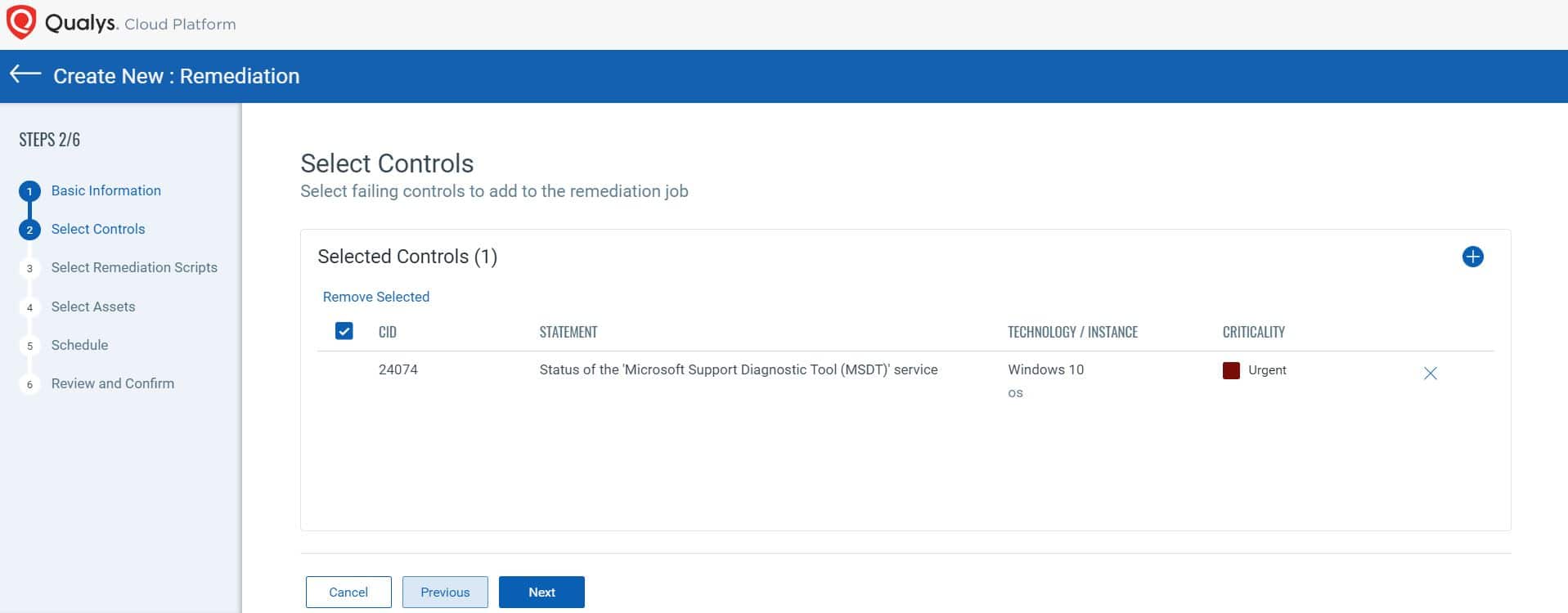 Step 4: Select the control
Step 4: Select the control 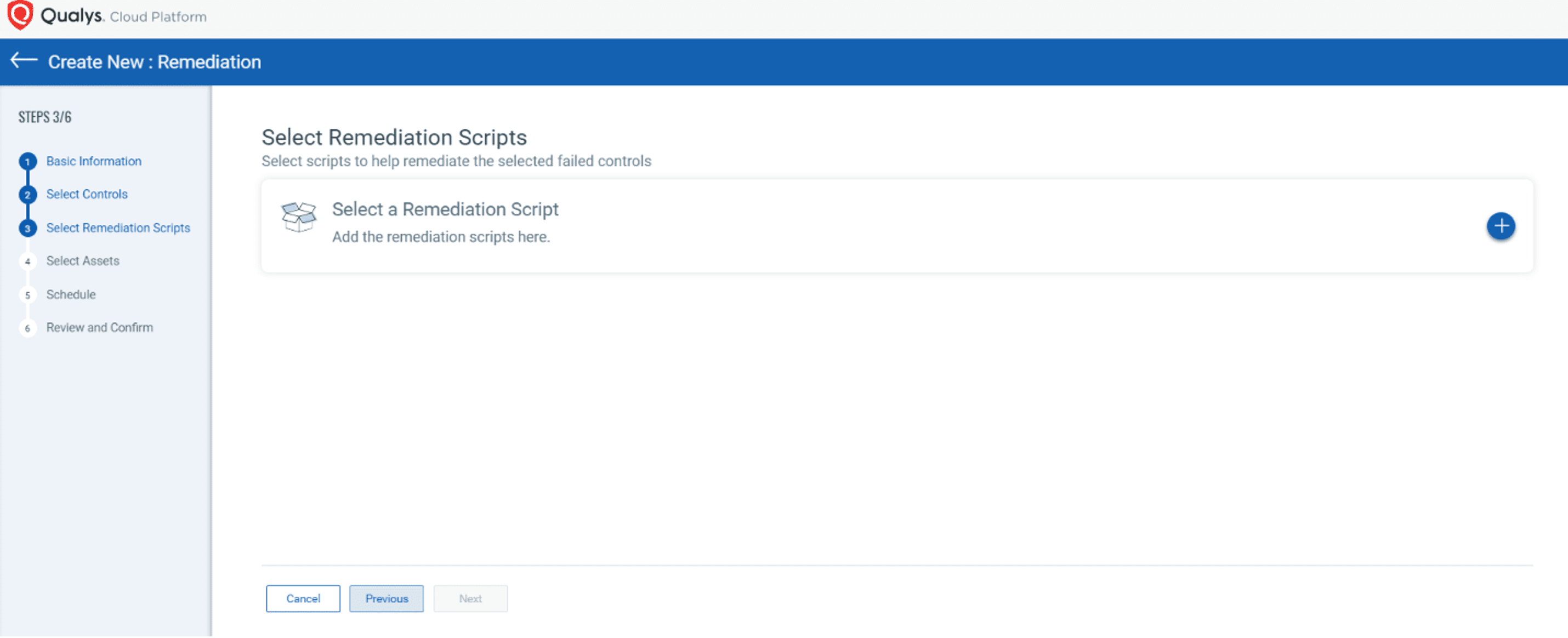 Step 5: Go to the script library
Step 5: Go to the script library
Next, users can select a remediation script:
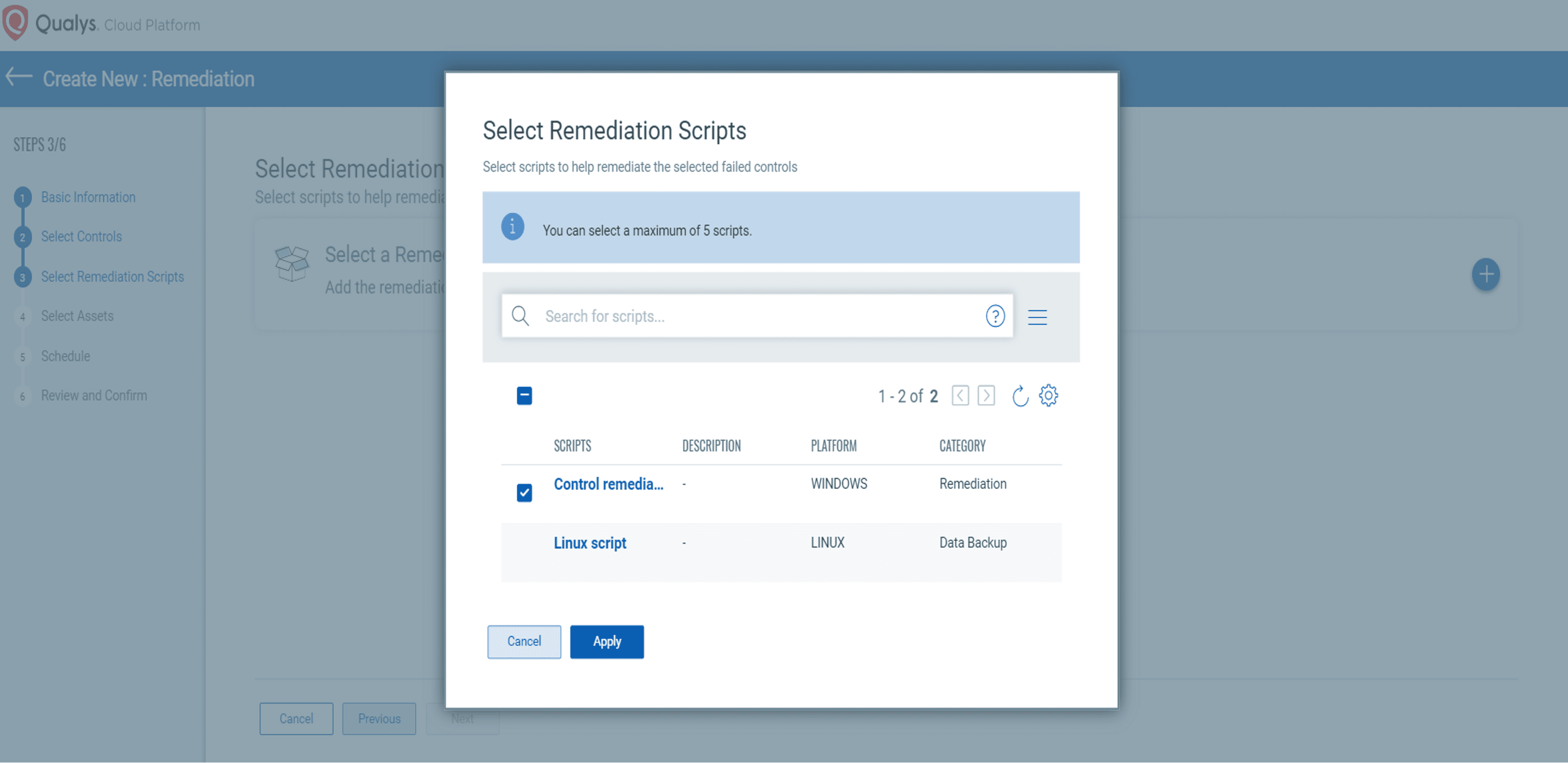 Step 6: Select the remediation script from the library
Step 6: Select the remediation script from the library
Then they select the asset for remediation:
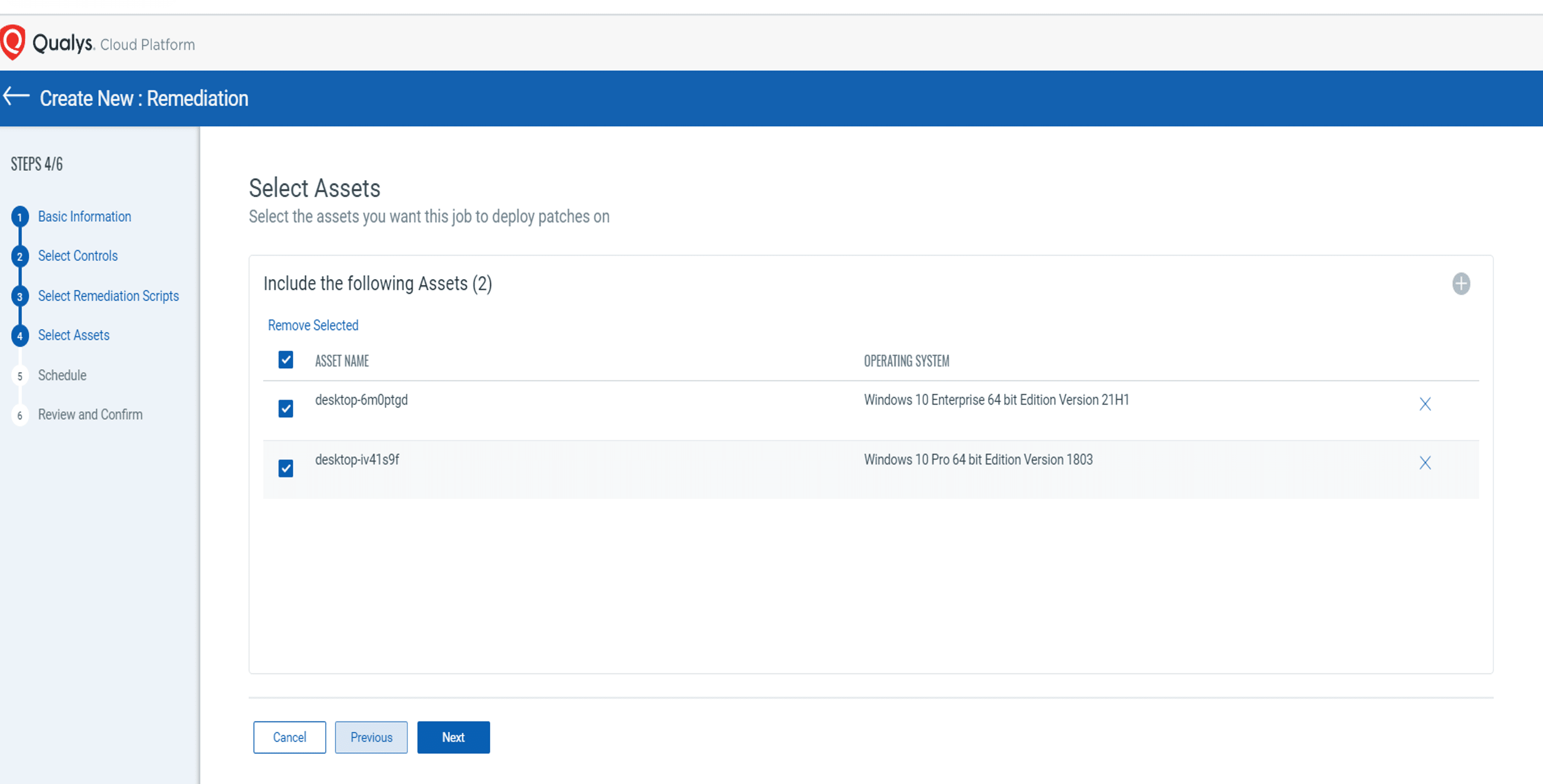 Step 7: Select assets to remediate
Step 7: Select assets to remediate 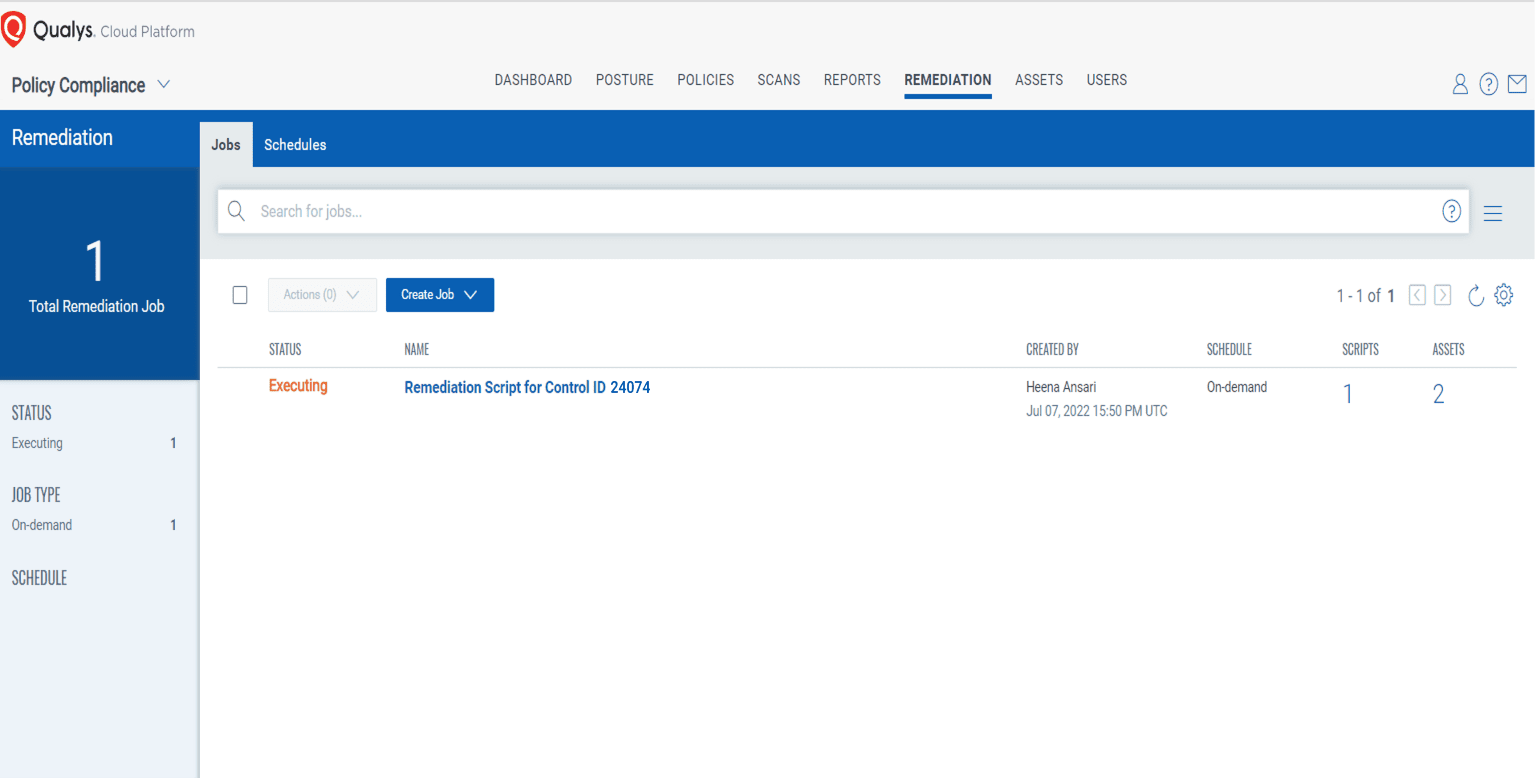 Step 8: Track status of the remediation job
Step 8: Track status of the remediation job
After successful execution of the remediation script, the control is remediated, and security posture is changed from Fail to Pass.
Cyber risk has been reduced after fixing the misconfiguration.
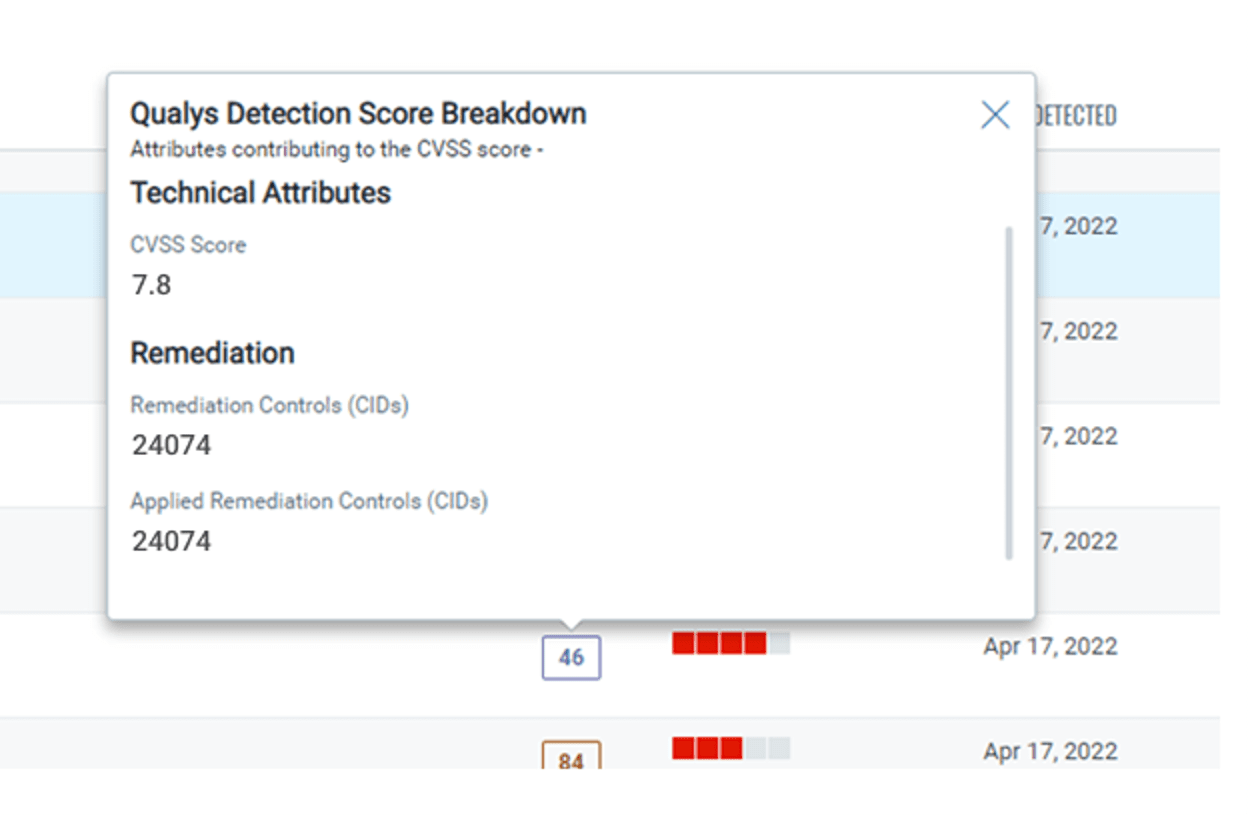 Remediation reduces Applied Risk Score
Remediation reduces Applied Risk Score
Executing Workarounds using Qualys Custom Assessment and Remediation****
Qualys Custom Assessment and Remediation allows security practitioners to quickly create and execute custom scripts and controls, and then to take immediate action to directly remediate problems and apply mitigations. From Qualys PC, users can perform the provided mitigation steps by creating a PowerShell script and executing it on the vulnerable assets.
Watch this short looping video demonstrating how easy it is to execute remediation jobs in Qualys.
 Applying workaround for Follina vulnerability using Qualys Custom Assessment & Remediation
Applying workaround for Follina vulnerability using Qualys Custom Assessment & Remediation
Summary****
Qualys Policy Compliance is not only a leading provider of security recommendations across CIS and DISA standards, but also provides out-of-the-box recommendations and compensating controls. This combination secures enterprise IT infrastructure from known zero-day vulnerabilities when no patch is available, thereby reducing the overall cyber risk associated with any zero-day vulnerability.
Getting Started
Ready to get started? Learn more about how Qualys Policy Compliance provides different configuration assessment controls. Sign up for a free trial today.
contributors
- Mukesh Choudhary, Compliance Research Analyst, Qualys
- Mohd Anas Khan, Compliance Research Analyst, Qualys
- Vikas Gothwal, Senior Compliance Research Analyst, Qualys