
New Options Profiles for Log4Shell Detection
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C
We have now added two new option profiles to our library for Log4Shell vulnerabilities. Option profiles define the settings you want to use for your scan. These new option profiles are tuned to quickly detect the Log4Shell vulnerability on assets in your environment.
The following two pre-configured option profiles are now available in the library to help you get started:
- Log4Shell - Authenticated Scan
- Log4Shell – Unauthenticated Scan
You can import these profiles into your account and use them as-is or edit them as needed.
Importing Option Profiles
To import our option profiles, go to Scans >Option Profiles>Newand selectImport from Library.
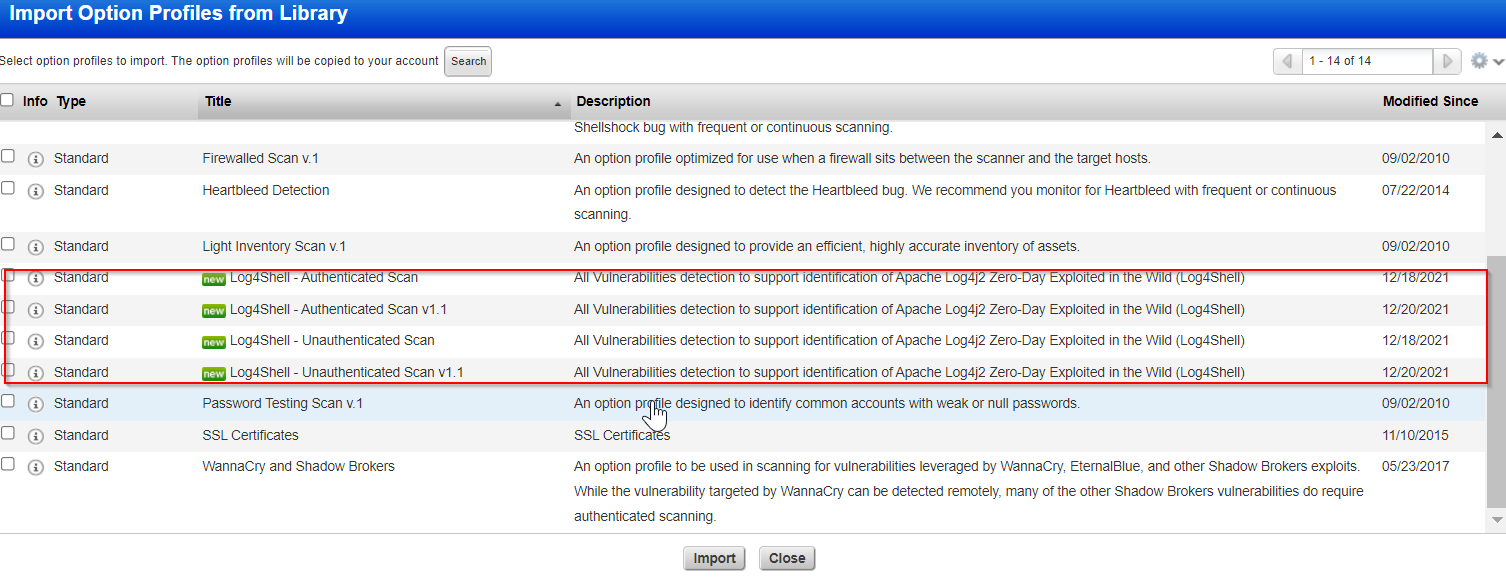
Choose from the Log4Shell -Authenticated ScanorLog4Shell–Unauthenticated Scanoptions and clickImport.
Note: Use the Log4Shell - Authenticated Scan option profile for authenticated scans andLog4Shell - Unauthenticated Scan option for unauthenticated scans. For information on authenticated and unauthenticated scans, refer to the Why Use Host Authentication? section of the Online Help.
We recommend making the option profile Global to make it available to all users in the subscription.
The Log4Shell option profiles come with pre-defined search lists that include Log4Shell QIDs. When you scan using these option profiles, the scanner first gathers information about the host and then scans for all QIDs listed with these option profiles. For information on QIDs listed with these option profiles, refer to the Search List section.
The Scan Settings tab in the Option Profile information provides you with an option to view the complete list of QIDs that are included/associated with the option profile.
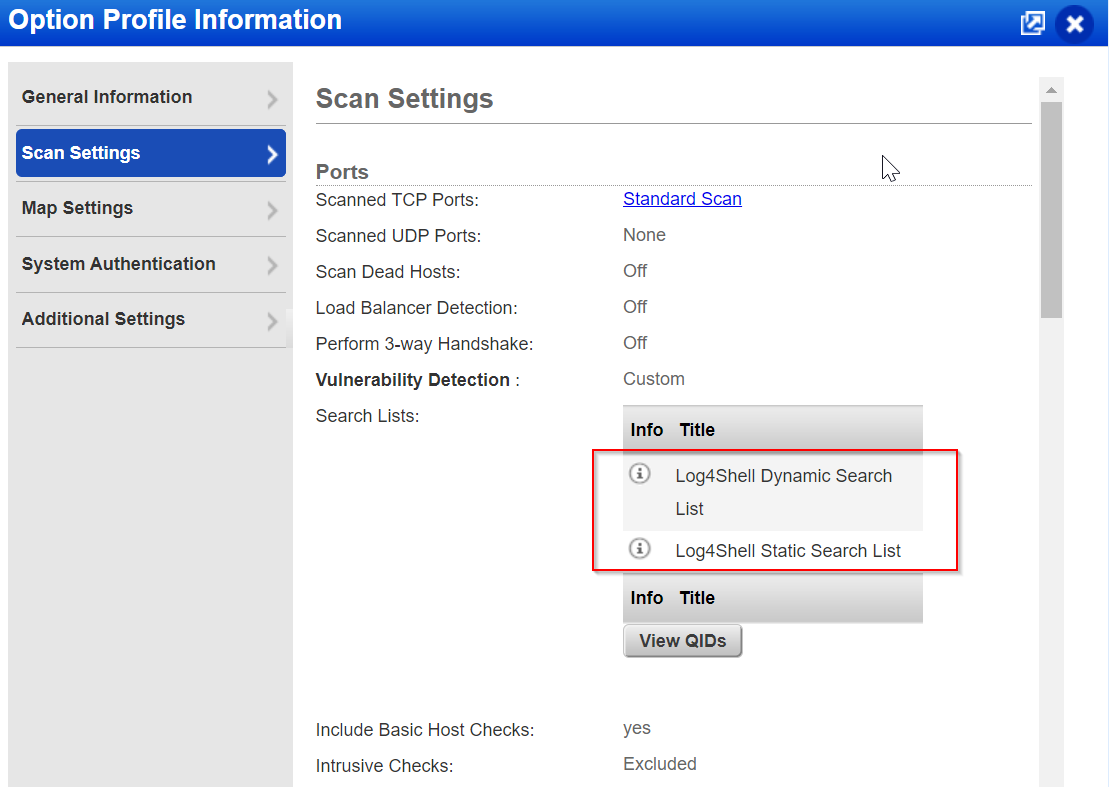
Review the other tabs of these option profiles to confirm it suits your requirement. Note that these option profiles set the performance of the scan as Normal. If you are concerned about the performance impact, Qualys recommends you change these settings to match your requirement.
When you are ready to scan your environment for Log4Shell vulnerabilities, run a scan and ensure to select these option profiles you just imported. You can associate the option profile when you trigger the scan. For more information on scans, refer to the Scan for Vulnerabilities topic in the Online Help.
Once the scan is completed, you can view the scan report to know the assets that have been affected by the vulnerabilities. Go to the reports list and check to be sure your report is finished - the status will show "Finished". For more information on scan reports, refer to the Reporting on your Vulnerabilities and Assets topic in the Online Help.
Search Lists
Qualys has released 2 search lists to cater to QIDs associated with Log4Shell:
- Log4Shell Dynamic Search List: This is a** dynamic search list** that searches for vulnerabilities related to Apache Log4j2 Zero-Day Exploited in the Wild (Log4Shell). This search list includes the following CVE IDs:
* CVE-2021-45046
* CVE-2021-44228
* CVE-2021-4104
* CVE-2021-45105 - Log4Shell Static Search List: This is a** static search list** that helps in the detection of Apache Log4j2 Zero-Day Exploited in the Wild (Log4Shell). This search list includes the following QIDs:
QID Number| QID Title
—|—
45006| Traceroute
45017| OS Detected
70000| NetBIOS name accessible
82023| OpenTCPServicesList
45039| Hostnamefound
6| DNSHostName
82044| NetBIOS
34011| Firewall detected
43007| Network adapter MAC address
45038| Host scan time
82062| NetBIOS Workgroup name detected
45141| Installed Packages on Unix and Linux Operating Systems
45179| Report Qualys Host ID Value
90235| Installed Applications Enumerated From Windows Installer
45456| Windows WMI Authentication Level status
34011| Firewall detected
45484| Correlation id service running
48143| Correlation id detected
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C