
Microsoft and Adobe Patch Tuesday, November 2023 Security Update Review
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
9.8 High
AI Score
Confidence
High
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
0.46 Medium
EPSS
Percentile
97.1%
Microsoft released its second last Patch Tuesday edition of the year. We invite you to join us to review and discuss the details of these security updates and patches.
Microsoft Patch Tuesday for November 2023
In this month's Patch Tuesday edition, Microsoft has addressed a total of 75 vulnerabilities, including fivevulnerabilities known to be exploited in the wild. This month's updates also include threeCritical and 62 Important severity vulnerabilities. Microsoft has also included14 Microsoft Edge (Chromium-based) vulnerabilities in the updates patched earlier this month.
Microsoft Patch Tuesday, November edition includes updates for vulnerabilities in Microsoft Office and Components, Open Management Infrastructure, Tablet Windows User Interface, Visual Studio Code, Windows Authentication Methods, Windows Cloud Files Mini Filter Driver, Windows Common Log File System Driver, and more.
Microsoft has fixed several flaws in multiple software, including Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Remote Code Execution (RCE), Security Feature Bypass, Cross-site Scripting Vulnerability, and Spoofing.
The November 2023 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
|---|---|---|
| Spoofing Vulnerability | 11 | Important: 11 |
| Denial of Service Vulnerability | 5 | Important: 5 |
| Elevation of Privilege Vulnerability | 18 | Critical: 1 |
| Important: 17 | ||
| Information Disclosure Vulnerability | 6 | Critical: 1 |
| Important: 5 | ||
| Security Feature Bypass Vulnerability | 6 | Important: 6 |
| Remote Code Execution Vulnerability | 19 | Critical: 1 |
| Important: 18 |
Adobe Patches for November 2023
Adobe has released 14 security advisories to address66vulnerabilities in Adobe ColdFusion, Adobe RoboHelp Server, Adobe Acrobat and Reader, Adobe InDesign, Adobe Photoshop, Adobe Bridge, Adobe FrameMaker Publishing Server, Adobe InCopy, Adobe Animate, Adobe Dimension, Adobe Media Encoder, Adobe Audition, Adobe Premiere Pro, and Adobe After Effects. This month’s security updates included34 critical severity vulnerabilities. Successful exploitation of the critical severity vulnerabilities may result in arbitrary code execution, memory, and security feature bypass.
Zero-day Vulnerabilities Patched in November Patch Tuesday Edition
CVE-2023-36413: Microsoft Office Security Feature Bypass Vulnerability
An attacker may exploit this vulnerability to bypass the Office Protected View and open in editing mode instead of protected mode. An attacker must send the user a malicious file and convince them to open it to exploit the vulnerability.
CVE-2023-36036: Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
A mini filter driver can filter IRP-based I/O activities along with the fast I/O and file system filter (FSFilter) callback actions. A mini filter driver can register a preoperation and postoperation callback routine, or both, for each I/O operation it wishes to filter.
Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
CISA has added the vulnerability to its Known Exploited Vulnerabilities Catalog and requested users to patch it before December 12, 2023.
CVE-2023-36038: ASP.NET Core Denial of Service Vulnerability
ASP.NET is a popular web-development framework for creating web applications on the.NET platform. The open-source ASP.NET Core is compatible with Windows, Linux, and macOS. ASP.NET Core redesigns previous ASP.NET versions exclusive to Windows.
An attacker may exploit the vulnerability when HTTP requests to .NET 8 RC 1 running on the IIS InProcess hosting model are canceled.
CVE-2023-36033: Windows DWM Core Library Elevation of Privilege Vulnerability
Desktop Window Manager (DWM) is a core system file in Microsoft Windows. It is responsible for producing each component visible on a laptop or PC. DWM covers visual effects such as system animations, wallpapers, themes, thumbnails, Windows Aero, Windows Flip, and Windows Flip3D, as well as transparent components.
Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
CISA has added the vulnerability to its Known Exploited Vulnerabilities Catalog and requested users to patch it before December 12, 2023.
CVE-2023-36025: Windows SmartScreen Security Feature Bypass Vulnerability
Windows SmartScreen is a security feature in Microsoft Windows operating systems that protects against malicious software and websites. SmartScreen is a background application that employs a cloud-based component to scan web pages you visit for security risks updated regularly.
To exploit the vulnerability, an attacker must convince a user to click on a specially crafted Internet Shortcut (.URL) or a hyperlink pointing to an Internet Shortcut file to be compromised by them. An attacker may bypass Windows Defender SmartScreen checks and associated prompts on successful exploitation.
CISA has added the vulnerability to its Known Exploited Vulnerabilities Catalog and requested users to patch it before December 12, 2023.
Other Critical Severity Vulnerabilities Patched in November Patch Tuesday Edition
CVE-2023-36052: Azure CLI REST Command Information Disclosure Vulnerability
The Azure CLI is a command-line tool that provides a native CLI interface required when working with Microsoft Azure resources. The Azure CLI can call the Azure REST API to perform actions that each Azure CLI (az) command supports.
Successful exploitation of the vulnerability may allow an unauthenticated attacker to retrieve plaintext passwords and usernames from log files stored in open-source repositories.
CVE-2023-36400: Windows HMAC Key Derivation Elevation of Privilege Vulnerability
The Hash-based Message Authentication Code (HMAC) detects if a message received via an insecure channel has been altered when the sender and receiver use secret keys. It's a cryptographic authentication technique that uses a cryptographic hash function and a shared secret key to encrypt information and protect it from unauthorized access.
An attacker must log on to the system and run a specially crafted application to exploit this vulnerability. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
CVE-2023-36397: Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability
Pragmatic General Multicast (PGM) is a multicast computer network transport protocol appropriate for multi-receiver file transfer applications. PGM provides a reliable sequence of packets to multiple recipients simultaneously.
An attacker may exploit this vulnerability to send a specially crafted file over the network when the Windows message queuing service runs in a PGM Server environment. Successful exploitation of the vulnerability may allow an attacker to perform remote code execution and attempt to trigger malicious code.
Other Microsoft Vulnerability Highlights
- CVE-2023-36424 is an elevation of privilege vulnerability in the Windows Common Log File System Driver. Successful exploitation of the vulnerability may allow an attacker to elevate privileges from a Medium Integrity Level to a High Integrity Level.
- CVE-2023-38177 is a remote code execution vulnerability in the Microsoft SharePoint server. An authenticated attacker may exploit the vulnerability to gain access to create a site and execute code remotely within the SharePoint Server.
- CVE-2023-36439 is a remote code execution vulnerability in the Microsoft Exchange server. An authenticated attacker can exploit the vulnerability as a valid exchange user with LAN access. On successful exploitation, an attacker may perform remote code execution on the server mailbox backend as NT AUTHORITY\SYSTEM.
- CVE-2023-36399 is an elevation of privilege vulnerability in Windows Storage. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
- CVE-2023-36394 is an elevation of privilege vulnerability in Windows Search Service. To exploit the vulnerability, an attacker must win a race condition. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
- CVE-2023-36035 and CVE-2023-36039 are spoofing vulnerabilities in Microsoft Exchange Server. To exploit the vulnerabilities, an attacker must be authenticated with LAN access and have credentials for a valid Exchange user. An attacker may exploit the vulnerability by using a PowerShell remoting session to the server. On successful exploitation, an attacker could access a user's Net-NTLMv2 hash as a basis of an NTLM Relay attack against another service to authenticate as the user.
- CVE-2023-36050 is a spoofing vulnerability in Microsoft Exchange Server. To exploit the vulnerability, an attacker must be authenticated with LAN access and have credentials for a valid Exchange user. An attacker could exploit the vulnerability by exploiting the known (Type 4) UnitySerializationHolder gadget through deserialization of untrusted data.
Microsoft Release Summary
This month's release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, .NET Framework, ASP.NET, Azure DevOps, Microsoft Bluetooth Driver, Microsoft Dynamics, Microsoft Dynamics 365 Sales, Microsoft Edge (Chromium-based), Microsoft Exchange Server, Microsoft Remote Registry Service, Microsoft WDAC OLE DB provider for SQL, Microsoft Windows Search Component, Microsoft Windows Speech, Windows Compressed Folder, Windows Defender, Windows Deployment Services, Windows DHCP Server, Windows Distributed File System (DFS), Windows DWM Core Library, Windows HMAC Key Derivation, Windows Hyper-V, Windows Installer, Windows Internet Connection Sharing (ICS), Windows Kernel, Windows NTFS, Windows Protected EAP (PEAP), Windows Scripting, Windows SmartScreen, and Windows Storage.
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
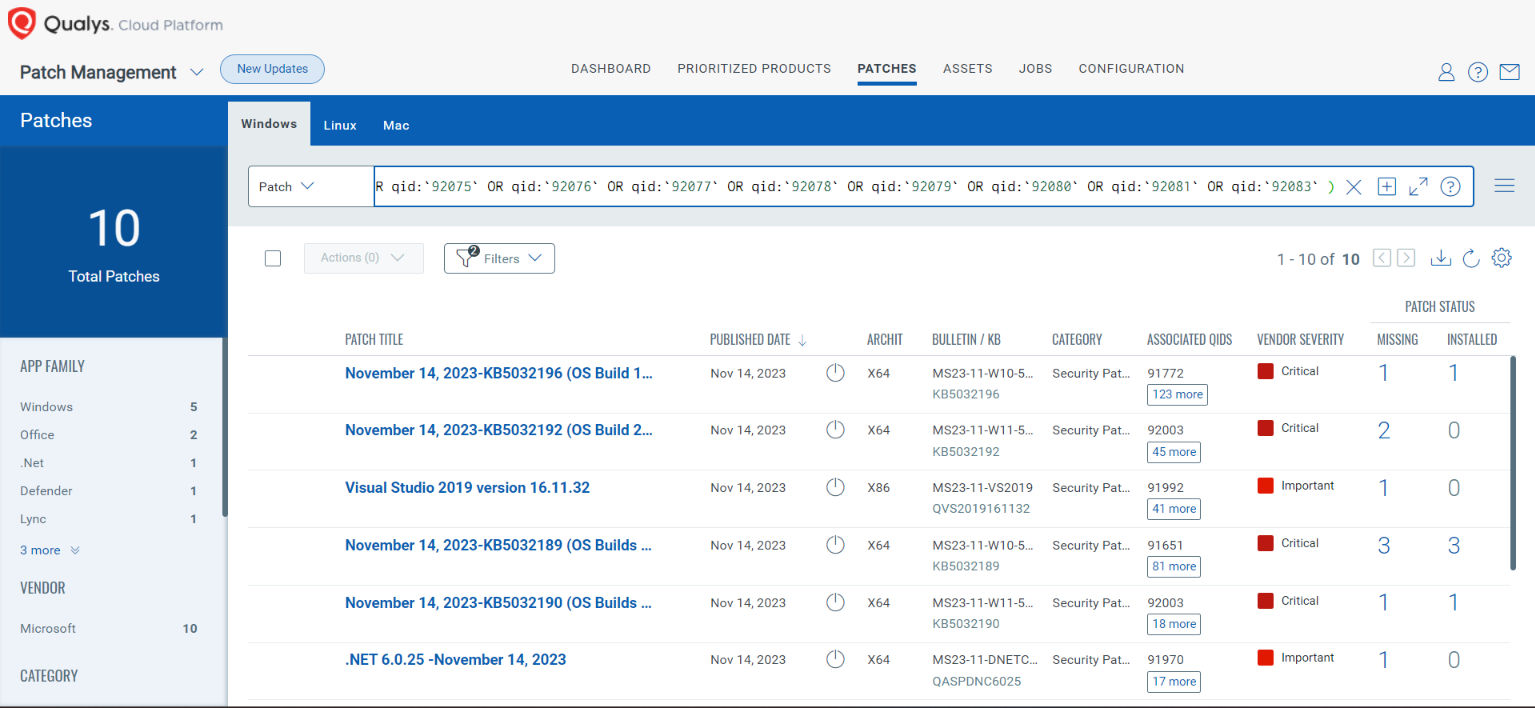
_vulnerabilities.vulnerability:( qid:`110451` OR qid:`379003` OR qid:`379005` OR qid:`50133` OR qid:`92075` OR qid:`92076` OR qid:`92077` OR qid:`92078` OR qid:`92079` OR qid:`92080` or qid:`92081` or qid: `92083` )_

Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid:110451 OR qid:110452 OR qid:379003 OR qid:379005 OR qid:50133 OR qid:92075 OR qid:92076 OR qid:92077 OR qid:92078 OR qid:92079 OR qid:92080 OR qid:92081 OR qid:92083 )
EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
Qualys Policy Compliance's Out-of-the-Box Mitigation or Compensatory Controls reduce the risk of a vulnerability being exploited because the remediation (fix/patch) cannot be done now; these security controls are not recommended by any industry standards such as CIS, DISA-STIG.
Qualys Policy Compliance team releases these exclusive controls based on vendor-suggested Mitigation/Workaround.
Mitigation refers to a setting, common configuration, or general best practice existing in a default state that could reduce the severity of the exploitation of a vulnerability.
A workaround is sometimes used temporarily for achieving a task or goal when the usual or planned method isn't working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned.
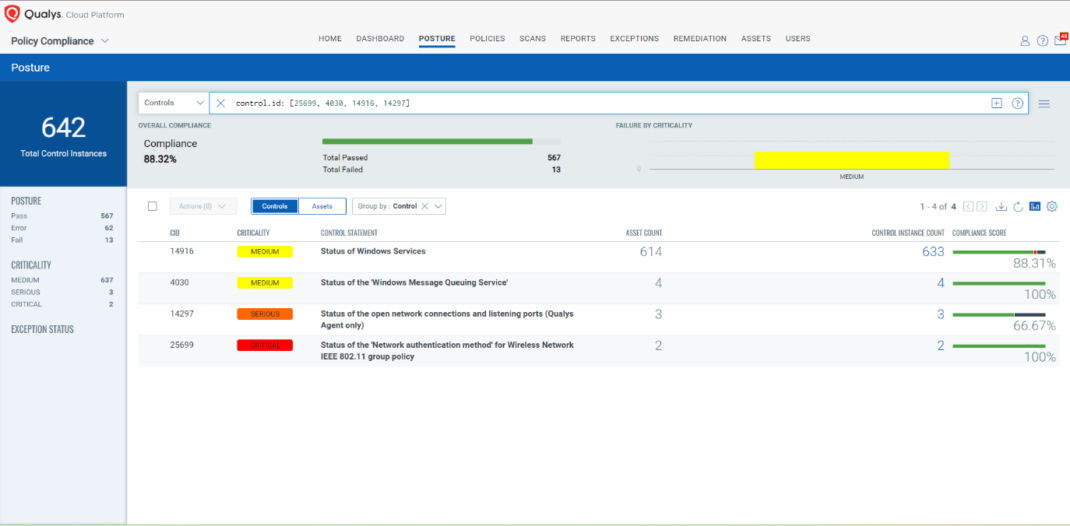
The following Qualys Policy Compliance Control IDs (CIDs) and System Defined Controls (SDC) have been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:
CVE-2023-36028: Microsoft Protected Extensible Authentication Protocol (PEAP) Remote Code Execution Vulnerability
This vulnerability has a CVSS:3.1 9.8 / 8.5
Policy Compliance Control IDs (CIDs):
- 25699 Status of the 'Network authentication method' for Wireless Network IEEE 802.11 group policy
CVE-2023-36397 - Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability
This vulnerability has a CVSS:3.1 9.8 / 8.5
Policy Compliance Control IDs (CIDs):
- 4030 Status of the 'Windows Message Queuing Service'
- 14916 Status of Windows Services
- 14297 Status of the open network connections and listening ports (Qualys Agent only)
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [25699, 4030, 14916, 14297]
EXECUTE Mitigation Using Qualys Custom Assessment and Remediation (CAR)
Qualys Custom Assessment and Remediation (CAR) can be leveraged to execute mitigation steps provided by MSRC on vulnerable assets.
The next Patch Tuesday falls on December 12, and we'll be back with details and patch analysis. Until next Patch Tuesday, stay safe and secure. Be sure to subscribe to the 'This Month in Vulnerabilities and Patch's webinar.'
Qualys Monthly Webinar Series

The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month's high-impact vulnerabilities, including those that are a part of this month's Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
Join the webinar
This Month in Vulnerabilities & Patches
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
9.8 High
AI Score
Confidence
High
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
0.46 Medium
EPSS
Percentile
97.1%