
Windows RDP Remote Code Execution Vulnerability (BlueKeep) – How to Detect and Patch
0.975 High
EPSS
Percentile
100.0%
This month’s Microsoft Patch Tuesday included a very high-risk vulnerability (CVE-2019-0708, aka BlueKeep) in Remote Desktop that impacts Windows XP, Windows 7, Server 2003, Server 2008, and Server 2008 R2. This vulnerability allows an unauthenticated attacker (or malware) to execute code on the vulnerable system. It is very likely that PoC code will be published soon, and this may result in a WannaCry-style attack.
Microsoft has not only released patches for Windows 7, Server 2008 & R2, but also has taken the extra step to issue patches for Windows XP and Server 2003. Patch now!
UPDATE: Network Level Authentication (NLA) partially mitigates this vulnerability. QID 90788 (Microsoft Windows Network Level Authentication Disabled) can be used to find hosts that have NLA disabled. This forces the attacker to have valid credentials in order to perform RCE.
UPDATE: A new remote (unauthenticated) check was released under QID 91541. See below for details.
Detecting CVE-2019-0708
Qualys has issued a special QID (91534) for Qualys Vulnerability Management that covers only CVE-2019-0708 across all impacted Operating Systems, including Windows XP and Server 2003. This QID is included in signature version VULNSIGS-2.4.606-3, and requires authenticated scanning or the Qualys Cloud Agent. Cloud Agents will automatically receive this new QID as part of manifest version 2.4.606.3-2.
BlueKeep Unauthenticated check Update:
Qualys has also released a new unauthenticated check to address BlueKeep vulnerability:
QID 91541 : Microsoft Windows Remote Desktop Services Remote Code Execution Vulnerability (BlueKeep) (unauthenticated check)
This QID is included in vulnerability signature version VULNSIGS-2.4.620-x. A Scanner version update (11.2.35) is required to support this new QID. In certain edge cases involving CredSSP, for Windows 7 and above operating systems, this QID may not post as vulnerable, if service is not identified as RDP over port 3389. However, the authenticated check (QID 91534) will post the vulnerability for all affected Operating Systems.
You can search for all vulnerable systems in AssetView or within the VM Dashboard (Beta) by using the following QQL query:
> vulnerabilities.vulnerability.cveIds:CVE-2019-0708
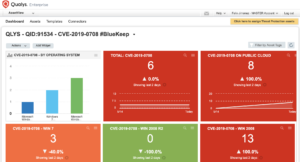
Tracking Impact and Remediation
Qualys is providing a downloadable AssetView Dashboard for tracking this vuln across your environment. Visit the Qualys Community to download it now for importing into your subscription.
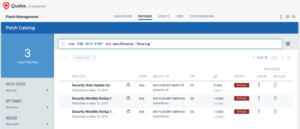
Remediating with Qualys Patch Management
Customers using Qualys Patch Management with Cloud Agent can search for cve:CVE-2019-0708 in the Patch Catalog, and click “Missing” in the side panel to locate and deploy patches to all affected Operating Systems, including Windows XP and Server 2003.
For emergency patching, you can create an On-demand Job and target it at the “Cloud Agent” tag to cover all hosts. For continuous patching, a Daily Job can be created with a 24-hour “Patch Window” to ensure all hosts will continue to receive the required patches. This patch does require a reboot.
Targeting specific operating systems is not necessary. The Qualys Cloud Agent already knows which patch is needed for each host.
Get Started Now
To start detecting and remediating this vulnerability now, get a Qualys Suite trial.