
Microsoft released patch for actively exploited spoofing vulnerability
7.1 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
HIGH
Privileges Required
LOW
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:H/PR:L/UI:R/S:U/C:H/I:H/A:H
6 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
SINGLE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:S/C:P/I:P/A:P
THREAT LEVEL: Amber.
For a detailed advisory, download the pdf file here.
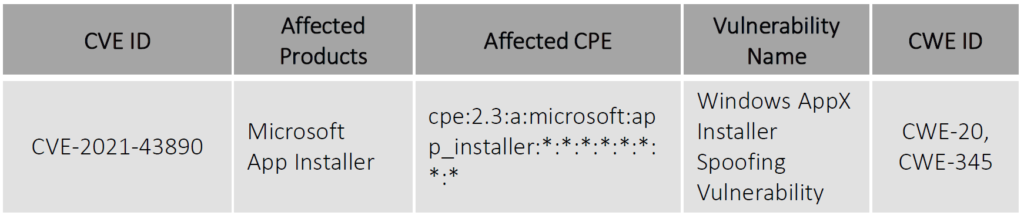
Microsoft AppX has a spoofing vulnerability that has been assigned CVE-2021-43890. Attackers are taking advantage of this critical vulnerability by deploying well-known malwares such as Emotet, Trickbot, and Bazaloader.
This vulnerability allows an attacker to create a malicious package file and modify it to look like a legitimate application and then convince the victim to open it, which will then execute code and allow to gain access to the victim’s machine.
The TTPs that might be used by an unknown attacker includes:
TA0001 - Initial Access
T1566 - Phishing
T1566.001 - Phishing: Spearphishing Attachment
T1189 - Drive-by Compromise
TA0002 - Execution
T1204 - User Execution
T1204.002 - User Execution: Malicious File
TA0005 - Defense Evasion
T1036 - Masquerading
T1036.005 - Masquerading: Match Legitimate Name or Location
T1574 - Hijack Execution Flow
TA0003 - Persistence
TA0004 - Privilege Escalation
Vulnerability Detail
Patch
<https://msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2021-43890>
References
<https://thehackernews.com/2021/12/microsoft-issues-windows-update-to.html>
7.1 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
HIGH
Privileges Required
LOW
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:H/PR:L/UI:R/S:U/C:H/I:H/A:H
6 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
SINGLE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:S/C:P/I:P/A:P