
Microsoft & Adobe Patch Tuesday (December 2021) – Microsoft 83 Vulnerabilities with 7 Critical, 1 Actively Exploited. Adobe 60 Vulnerabilities, 28 critical.
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
Microsoft Patch Tuesday – December 2021
Microsoft patched 83 vulnerabilities in their December 2021 Patch Tuesday release, of which seven (7) are rated as critical severity. This month's release includes one (1) Zero Day known to be actively exploited.
Products impacted by Microsoft's December security update include Microsoft Office, Microsoft PowerShell, the Chromium-based Edge browser, the Windows Kernel, Print Spooler, and Remote Desktop Client.
Microsoft has fixed problems in software including Remote Code Execution (RCE) vulnerabilities, privilege escalation security flaws, spoofing bugs, and denial-of-service issues.
Microsoft Vulnerabilities to be Prioritized and Patched…Quickly.
CVE-2021-43890** | Windows AppX Installer Spoofing Vulnerability**
This vulnerability CVSS 7.1 is a Zero-Day known to be an actively exploited spoofing vulnerability in the AppX installer that affects Microsoft Windows. Microsoft is aware of attacks that attempt to exploit this vulnerability by using specially crafted packages that include the malware family known as Emotet/Trickbot/Bazaloader.
An attacker could craft a malicious attachment to be used in phishing campaigns. The attacker would then have to convince the user to open the specially crafted attachment. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
CVE-2021-43215** | iSNS Server Memory Corruption Vulnerability Can Lead to Remote Code Execution**
This is a Remote Code Execution (RCE) vulnerability targeting the Internet Storage Name Service (iSNS) protocol. iSNS is used for interaction between iSNS servers and iSNS clients. An attacker could send a specially crafted request to the Internet Storage Name Service (iSNS) server, which could result in remote code execution. At CVSS 9.8, this critical vulnerability should be prioritized and patched quickly.
CVE-2021-43217** | Windows Encrypting File System (EFS) Remote Code Execution Vulnerability**
This is a Remote Code Execution (RCE) vulnerability targeting Encrypting File System (EFS) where an attacker could cause a buffer overflow write leading to unauthenticated non-sandboxed code execution, and with a CVSS score of 8.1, its important to patch quickly.
Microsoft is addressing the vulnerability in a phased two-part rollout. These updates address the vulnerability by modifying how EFS makes connections from client to server.
For guidelines on how to manage the changes required for this vulnerability and more information on the phased rollout, see KB5009763: EFS security hardening changes in CVE-2021-43217.
When the second phase of Windows updates becomes available in Q1 2022, customers will be notified via a revision to this security vulnerability. If you wish to be notified when these updates are released, we recommend that you register for the security notifications mailer to be alerted of content changes to this advisory. See Microsoft Technical Security Notifications.
CVE-2021-43905** | Microsoft Office app Remote Code Execution Vulnerability**
This is an unauthenticated Remote Code Execution (RCE) vulnerability in the Microsoft Office app, important to patch quickly, as it has a high CVSS score of 9.6.
CVE-2021-41333** | Windows Print Spooler Elevation of Privilege Vulnerability**
This Windows Print Spooler Elevation of Privilege vulnerability has been made public and has low attack complexity, along with a CVSS score of 7.8, which necessitates patching quickly.
CVE-2021-43233** | Remote Desktop Client Remote Code Execution Vulnerability**
This is a critical Remote Code Execution (RCE) vulnerability included in the monthly rollup for Windows, with a CVSS score of 7.5, this too tops the list of vulnerabilities needing to be patched quickly.
Adobe Patch Tuesday – December 2021
Adobe released 11 product security updates that addressed 60 CVEs this Patch Tuesday, and 28 of the CVEs are rated as critical severity impacting Adobe After Effects, Dimension, Experience Manager, Media Encoder, Photoshop, Prelude, and Premiere Pro and Rush products.
Discover and Prioritize Patch Tuesday Vulnerabilities in VMDR
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledge Base (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability:(qid:91850 OR qid:91848 OR qid:91847 OR qid:91846 OR qid:91845 OR qid:91844 OR qid:91843 OR qid:376166 OR qid:376164 OR qid:376163 OR qid:376161 OR qid:110397 OR qid:110396) 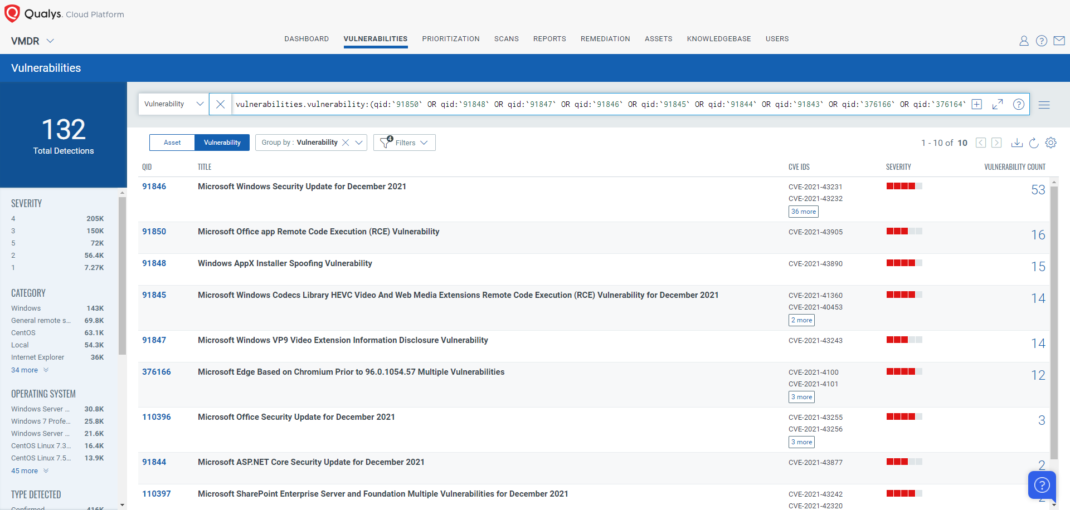
Respond by Patching
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches in one go.
The following QQL will return the missing patches pertaining to this Patch Tuesday.
(qid:91850 OR qid:91848 OR qid:91847 OR qid:91846 OR qid:91845 OR qid:91844 OR qid:91843 OR qid:376166 OR qid:376164 OR qid:376163 OR qid:376161 OR qid:110397 OR qid:110396) 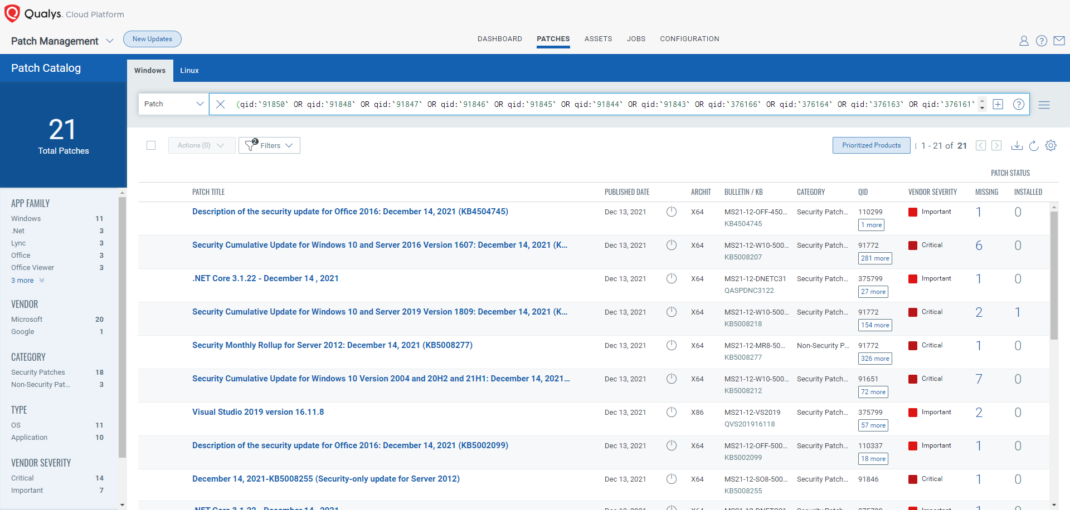
Patch Tuesday Dashboard
The current updated Patch Tuesday dashboards are available in Dashboard Toolbox: 2021 Patch Tuesday Dashboard.
Webinar Series: This Month in Vulnerabilities and Patches
To help customers leverage the seamless integration between Qualys VMDR and Patch Management and reduce the median time to remediate critical vulnerabilities, the Qualys Research team is hosting a monthly webinar series This Month in Vulnerabilities and Patches.
We discuss some of the key vulnerabilities disclosed in the past month and how to patch them:
- Microsoft Patch Tuesday, December 2021
- Adobe Patch Tuesday, December 2021
Join us live or watch on demand!
 Thursday, December 16, 2021 or later on demand
Thursday, December 16, 2021 or later on demand
About Patch Tuesday
Patch Tuesday QIDs are published at Security Alerts, typically late in the evening of Patch Tuesday, followed shortly after by PT dashboards.
Contributor
Bharat Jogi, Director, Vulnerability and Threat Research, Qualys
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P