
ZyXEL NBG-418N, PMG5318-B20A and P-660HW-T1 routers contain multiple vulnerabilities
10 High
CVSS2
Attack Vector
NETWORK
Attack Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
0.019 Low
EPSS
Percentile
88.6%
Overview
Several models of ZyXEL routers are vulnerable to multiple issues, including weak default passwords, command injections due to improper input validation, and cross-site scripting.
Description
CWE-255**: Credentials Management -**CVE-2015-6016
According to the reporter, the following models contain the weak default password of “1234” for the admin account:
* the ZyXEL P-660HW-T1 v2 with ZyNOS firmware version: V3.40(AXH.0) (dated 3/30/2007)
* the ZyXEL PMG5318-B20A, firmware version V100AANC0b5
* the ZyXEL NBG-418N
Many more models have been reported to share this same password.
CWE-80: Improper Neutralization of Script-Related HTML Tags in a Web Page (Basic XSS) - CVE-2015-6017
According to the reporter, a reflected cross site scripting vulnerability exists in the LoginPassword and hiddenPassword parameters of the /Forms/rpAuth_1 page on the ZyXEL P-660HW-T1 v2 with ZyNOS firmware version: V3.40(AXH.0) (dated 3/30/2007).
CWE-20: Improper Input Validation - CVE-2015-6018
According to the reporter, the diagnostic ping function’s PingIPAddr parameter in the ZyXEL PMG5318-B20A, firmware version V100AANC0b5, does not properly validate user input. An attacker may be able to execute arbitrary commands as root.
CWE-613: Insufficient Session Expiration - CVE-2015-6019
According to the reporter, the ZyXEL PMG5318-B20A, firmware version V100AANC0b5 does not properly expire the session when a user logs out of the management portal. The reporter has confirmed the session remains active for at least 1 hour after log off. An attacker may be able to utilize session information to gain access to the device even after the user has logged off.
CWE-285: Improper Authorization - CVE-2015-6020
According to the reporter, the regular user account on the ZyXEL PMG5318-B20A, firmware version V100AANC0b5 has full administrative access, rather than restricted access.
Impact
A remote unauthenticated attacker may be able to modify system configuration.
Solution
Apply updates and other changes
ZyXEL has previously addressed some issues, and will address the remaining issues in October 2015.
ZyXEL has provided the following summary of responses to these issues:
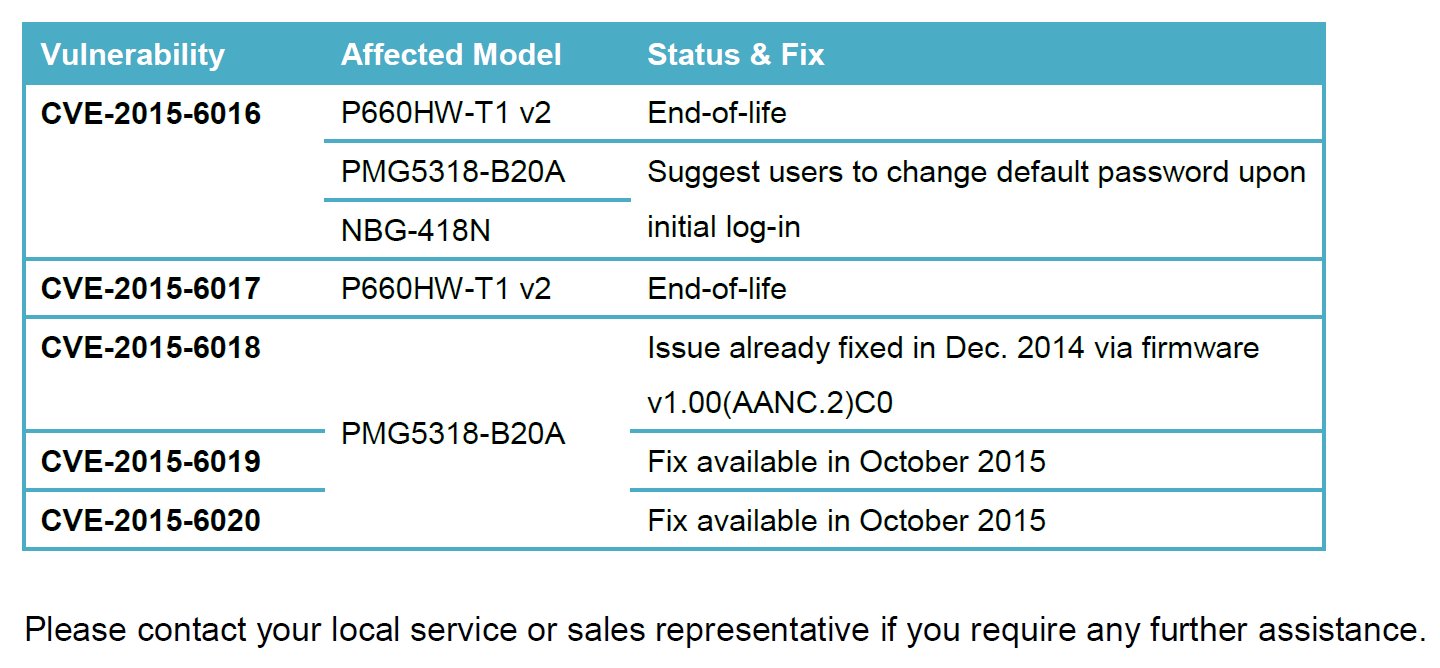
ZyXEL has also provided the following responses:
For CVE-2015-6016:
“ZyXEL suggests users of all products change the default password upon initial log-in. This is critical to protecting your network by keeping any unauthorized users from gaining access via the default password. ZyXEL has included reminders for this practice on a majority of products. Changing the default password upon initial log-in is mandatory for the ZyXEL USG/ZyWALL, UAG, and LTE Series.”
For CVE-2015-6017:
"Model P660HW-T1 v2 (ZyNOS v3.40) was designated “end-of-life” on May 14, 2010. ZyXEL assigns a product an “end-of-life” status when there is a clear indication that the market has transitioned to its replacement. This replacement generally offers advanced technology and/or better economics.
ZyXEL recommends users replace P660HW-T1 v2 with newer generations of DSL CPEs that better suit the network environment today. Or alternatively, as a good general security practice, ZyXEL suggests that users avoid visiting untrusted sites or clicking on unsolicited links. It is also recommended that users keep their browser, computer operating system, and security software current with the latest patches and updates."
For CVE-2015-6018:
“This issue was patched via a firmware update in December 2014 (version v1.00(AANC.2)C0), which included feature enhancements, as well as bug and security fixes. ZyXEL recommends that users go to the support site to obtain the latest update.”
For CVE-2015-6019 and CVE-2015-6020:
ZyXEL has released firmware version V1.00(AANC.3)b1 to address these issues in PMG5318-20A.
Vendor Information
870744
Filter by status: All Affected Not Affected Unknown
Filter by content: __ Additional information available
__ Sort by: Status Alphabetical
Expand all
Javascript is disabled. Click here to view vendors.
ZyXEL __ Affected
Notified: August 25, 2015 Updated: October 13, 2015
Status
Affected
Vendor Statement
ZyXEL has also provided the following responses:
For CVE-2015-6016:
“ZyXEL suggests users of all products change the default password upon initial log-in. This is critical to protecting your network by keeping any unauthorized users from gaining access via the default password. ZyXEL has included reminders for this practice on a majority of products. Changing the default password upon initial log-in is mandatory for the ZyXEL USG/ZyWALL, UAG, and LTE Series.”
For CVE-2015-6017:
"Model P660HW-T1 v2 (ZyNOS v3.40) was designated “end-of-life” on May 14, 2010. ZyXEL assigns a product an “end-of-life” status when there is a clear indication that the market has transitioned to its replacement. This replacement generally offers advanced technology and/or better economics.
ZyXEL recommends users replace P660HW-T1 v2 with newer generations of DSL CPEs that better suit the network environment today. Or alternatively, as a good general security practice, ZyXEL suggests that users avoid visiting untrusted sites or clicking on unsolicited links. It is also recommended that users keep their browser, computer operating system, and security software current with the latest patches and updates."
For CVE-2015-6018:
“This issue was patched via a firmware update in December 2014 (version v1.00(AANC.2)C0), which included feature enhancements, as well as bug and security fixes. ZyXEL recommends that users go to the support site to obtain the latest update.”
For CVE-2015-6019 and CVE-2015-6020:
“ZyXEL has identified the root causes and will release a patch for PMG5318-20A in October 2015 to solve the session expiration and authorization issues.”
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
CVSS Metrics
| Group | Score | Vector |
|---|---|---|
| Base | 8.3 | AV:A/AC:L/Au:N/C:C/I:C/A:C |
| Temporal | 7.1 | E:POC/RL:U/RC:UR |
| Environmental | 5.3 | CDP:ND/TD:M/CR:ND/IR:ND/AR:ND |
References
<http://www.zyxel.com/support/support_landing.shtml>
Acknowledgements
Thanks to Joel Land for reporting the vulnerability in the NBG-418N. Thanks to Karn Ganeshen for reporting the remaining vulnerabilities to us.
This document was written by Garret Wassermann.
Other Information
| CVE IDs: | CVE-2015-6016, CVE-2015-6017, CVE-2015-6018, CVE-2015-6019, CVE-2015-6020 |
|---|---|
| Date Public: | 2015-10-13 Date First Published: |
10 High
CVSS2
Attack Vector
NETWORK
Attack Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
0.019 Low
EPSS
Percentile
88.6%