What is Malware: Definition, Examples and How to Prevent

Malware or malicious software, refers to any program code that is designed to run on target system with illegitimate goals. Modern malware can infect not only user computers but also IOT (Internet of things) devices such as routers, printers, TVs and even cars! Endpoints can be infected in many ways and take various forms.
Let's find out what malware is, how it works, what it can do, and how you can protect yourself from it!
- What is malware?
- Why do criminals use malware?
- How does malware spread?
- Types of malware attacks
- How does malware affect businesses?
- Types of malware
- How to protect yourself from malware?
- How to detect and respond to malware?
- How to remove malware?
- Conclusion
- FAQ
What is malware?
On the Internet you can find many malware definitions, but there is no one single correct one. For example, there are 20 different definitions of the concept in the Nist dictionary.
Malware is a software or firmware developed to perform any adverse impact on the confidentiality, integrity, or availability of an information system. It can infect or damage user’s computers, steal sensitive data and destroy whole computer systems. Common malware examples include viruses, worms, Trojans, spyware, ransomware and other.
Why do criminals use malware?
If you're wondering why someone would need to put so much effort into attack your computer or device, let's take a moment to consider the type of people who become malware creators and what benefits do they get from this.
Most often, the main end goal is to make a profit. Also, there is a category of vandals, or those who create malware for interest and break something. Modern malware that can cause damage and make a significant impact is created by professional groups of people and is often similar to the development of some kind of legal software.
How does malware spread?
Malware can spread in many ways, the most popular of them: email attachments, malicious pop-up advertisements, exploitation of vulnerabilities, fake software, infected flash devices, malicious websites etc.
Types of malware attacks
The most basic types of malware attacks are collected here:
- Email: Phishing emails (spam) still remains the most popular way of hacking and obtaining initial access to target host. Very often, the templates of such letters are very well-thought-out and look like a legitimate letter (for example, from a bank). This is why you should not open emails from unknown senders.
- Messaging: SMS from unknown numbers and messages in such popular messengers as WhatsApp can also deliver malware. Malicious software can spread by hijacking messaging apps, new vulnerabilities are regularly identified and sometimes reading a message from an unknown number is enough to infect your device.
- Exploits: Exploits are program code or a sequence of commands used to exploit a security vulnerability or weakness in software or hardware. In fact, an exploit is the automation of the use of vulnerabilities and the malware uses them in its actions.
- Drive-by downloads: Drive-by download occurs when a malicious website automatically downloads malware to your device. This happens as soon as you load the page — no clicks are required. Adversaries use DNS hijacking to automate redirect you to malicious resources.
- Pop-up scams: Scareware tricks uses with fake security alerts or pop-up advertisement. It makes you download fake security software, which in some cases may be additional malware.
- Physical media: Hackers can upload malware to USB flash drives and wait for unsuspecting victims to plug them into their computers. This technique is often used in corporate espionage.
How does malware affect businesses?
The most basic and profitable goal for malware developers is to shut down a business, for example by encrypting a computer network and then demanding money to restore operations.
In May 2021, the world's largest beef producer JBS was attacked by the REvil ransomware. After that, the head of the company confirmed that JBS paid the attackers a ransom of $11,000,000.
In an interview with the Wall Street Journal, Colonial Pipeline CEO Joseph Blount said the company was forced to pay ransom to extortionists to recover as quickly as possible from a ransomware attack that impacted critical energy infrastructure.
Also, a popular goal is to steal customer data. For example, Equifax experienced one of the most famous customer data breaches in 2017. Hackers gained access to the personal data of 147 million people.
The most modern goal is mining, especially when large organizations are infected. For example, LemonDuck. This is a malware that, using various vulnerabilities, penetrates the network, scans available hosts and begins spreading. The main interesting feature is that LemonDuck scans the infected host for competing miners and removes them.
So why is it bad when a miner infects a host? The answer is simple: attackers use your equipment (GPU card prices!!!111) and resources for mining cryptocurrencies.
Types of malware
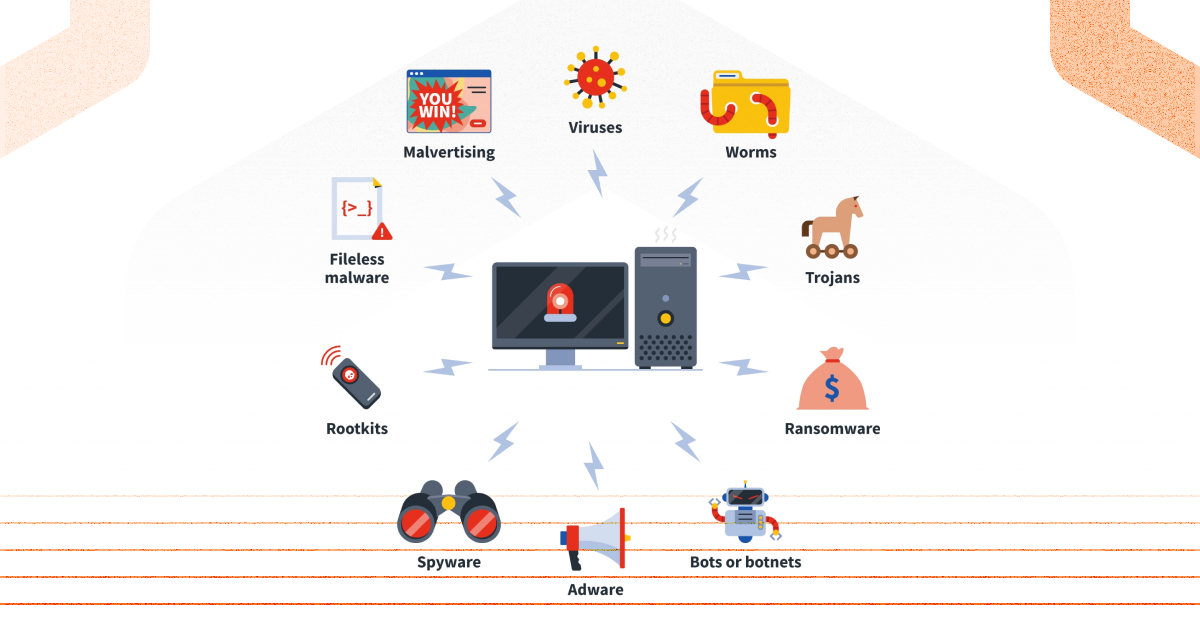
There are many malware threats out there. If you understand the common types of malware, you will have one of additional ways to protect your data and devices:
Viruses:
This is malicious software that is most often attached to a regular document or files, which supports macros to execute its malicious code and distribute from host to host. Viruses are created to disrupt the operating system. As a result, viruses can cause serious problems in operation and data loss.
Worms:
Worms are malicious software that can reproduce themselves on computers or through computer networks. At the same time, the user does not suspect about computer infection. Due to the fact that each subsequent copy of a virus or computer worm is also capable of self-replication, the infection spreads quickly. There are many types of computer viruses and computer worms, most of which are highly destructive.
Trojans
Created for the implementation of unauthorized actions by the user aimed at destroying, blocking, modifying or copying information, disrupting the operation of computers or computer networks. Unlike viruses and worms, representatives of this category do not have the ability to create their own copies and replicate.
Adware
Or advertisement software. Adware is not always malicious software, because it does try to destroy your system, mostly we can say that it’s “aggressive advertising”. The adware sends unwanted ads to users and usually displays ads or pop-ups when you perform a certain action. Adware is often installed in exchange for another service, such as using another soft without paying for it.
Spyware
It is generally defined as malicious software designed to place inside your device, collect data about you and transfer it to third parties without your consent. Spyware can also refer to legitimate software that tracks or collects your data for commercial purposes, such as advertising. However, malicious spyware is clearly being used to profit from stolen data.
Rootkits
The name "rootkit" comes from the Unix and Linux operating systems, where the most privileged account admin usually calls as "root". Rootkit is a class of malicious programs that operate secretly on an infected system and operate with special tools for defense evasion. Such malware is divided into user-level rootkits and kernel-level rootkits. The former have the same rights as most applications, the latter have full access rights to all components of the operating system. They can be used to steal personal and banking data, be part of a botnet, and can also be used as a backdoor.
Botnets
A number of infected (zombified) computers running malicious programs remotely controlled by cybercriminals using bots. Since the process takes place without the consent of users, botnets are sometimes called zombie networks.
Ransomware
This type of ransomware malware encrypts user files and demands a ransom for their decryption. Advanced ransomware uses sophisticated cryptographic algorithms so that files cannot be decrypted without a unique key. Targeted attacks often occur through this type of malware. Information security vendors are trying to study them and track specific groups.
Fileless malware
It is malware that does not store its body directly onto a disk. In the most cases it lives in the running memory. Sometimes this type is used in targeted attacks. It does not rely on files and leaves no footprint, making it more difficult to detect and remove.
How to protect yourself from malware?
Of course, to protect against malware, it is enough to observe digital hygiene. It is impossible to protect against all digital threats, but we can minimize the risks and avoid many of them. Let's look at the main points:
- Don’t trust online. Don’t trust strange emails, links, profiles in social medias and other. If you don’t know exactly what something is, don’t click or open it!
- Keep your operations system and software up to date: Updating you computer system regularly helps to prevent malware infections. When any update releases, make sure you benefit from the latest security patches. It makes it harder for adversaries to exploit vulnerabilities. The Vulners team creates a large database with information about released vulnerabilities. With the Vulners database, you can build your own vulnerability management process and not worry that your software has an outdated version.
- Use AD blocker. Malvertising hackers inject malicious code into legitimate advertising networks. Some infected advertisements can load malware immediately after they appear on the screen without even having to click on them.
- Never use unknown USB. Don’t unknow USB sticks or other storage device to your computer if you don’t know where it comes from.
- Use Antivirus Software. Even if you follow all advises, your PC might be infected by malware. Anti-malware security programs is also not a guarantee of 100% protection, but such software combines the expertise of many experts and the most relevant technologies to protect against most threats. Combine good online habits and malware protection.
- Strong passwords. Try to use strong different passwords with any Password manager. You can find any free or paid one.
- Multifactor authentication (MFA): One of the best ways to improve the security of your accounts. If this features is enabled, no one will be able to log in your account unless they use your pass and a one-time security code sent to your mobile device or generated in your authenticator app (Google, Microsoft, etc.) .
How to detect and respond to malware?
Malware inevitably infects your computer or even your corporate network. To detect and respond to malware, you must be able to quickly identify the attackers. For a home network, it is enough to use antivirus software and maintain digital hygiene. Enterprise networks require a comprehensive approach and antivirus tools are not enough. Additional measures needed:
- Continuous monitoring of infrastructure. Monitoring includes collecting information from all possible sources.
- Alerts for any suspicious activity. Set up detection logic that trigger alerts when suspicious or malicious activity is detected in your corporate network. It allows you to initiate an appropriate response for malicious activity.
How to remove malware?
If you think or have already found traces of a virus or malware on your computer, act quickly before the infection spreads. Follow these few simple steps to remove malware from your device:
- Download and install an anti-malware program. You can find many free antivirus programs online, but be careful not to fall for scammers. It is best to use paid antivirus programs from trusted vendors. Such programs have high-quality support, their antivirus databases are regularly updated, and they contain the most modern detection technologies.
- Antivirus scanning. This is one of the best ways to remove malware from your computer. Use a reliable malware removal tool to scan your device in advanced mode, find malware on it and remove the infection. After that, restart your device and rescan it again to make sure that the infection is completely removed and there are no residual artefacts.
- Password reset. If you discover that your account has been compromised, reset your account password as soon as possible and enable additional security features such as multifactor authentication (MFA).
Conclusion
There are plenty of malware out there that haven't been reviewed in this room, so don't be afraid to explore. In this article, we have tried to cover most of the points on the topic of malware.
We made sure to skip the giant ones like "wannacry" or "ILoveYou" as they are well known, but if you don't know, find out! They are definitely worth it.
It is often said that we need to learn from the mistakes of others. Often, malware attack succeeds because the user was inattentive or the software used was an old version. Vulners can fix The last thing, for example, you can subscribe to vulnerabilities for the software you use.
FAQ
What is malware in simple words?
Malicious program code or software that has been delivered to the PC in any way, then infects the PC and performs destructive actions.
How malware attacks your computer?
Malware can attack in many ways, which depend on malware trends. The most common ones are malicious emails (phishing), infected AD, data encryption and exploitation of vulnerabilities.
Can malware steal passwords?
Yes, of course, but not always. Sometimes malware has other goals: steal other data, turning the target into a botnet, stealing other user data, money, etc.
What is the difference between malware and spyware?
These are two different families of malware. Malware can have more targets than spyware. Spyware is most often spyware and can run on your PC for a long time in stealth mode to steal as much user data as possible.
Can you get malware just by visiting a website?
Yes, you can infect your computer by visiting a malicious website. That is why it is recommended not to visit untrusted sites and not fall for fakes.
Can opening an email infect your computer?
Phishing is the most popular way to infect users and a popular entry point for an attacker. Sometimes, just one click is enough for your credentials to be compromised.
