WhatsApp-based wormable Android malware spotted on the Google Play Store
Cybersecurity researchers have discovered yet another piece of wormable Android malware—but this time downloadable directly from the official Google Play Store—that’s capable of propagating via WhatsApp messages.
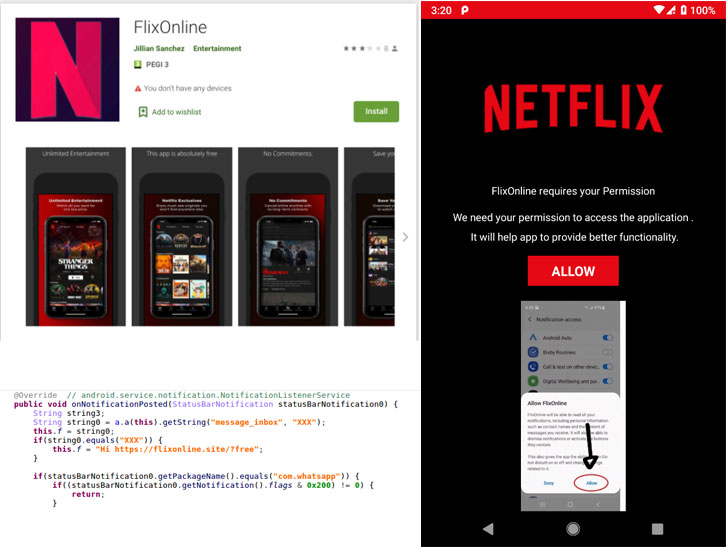
Disguised as a rogue Netflix app under the name of “FlixOnline,” the malware comes with features that allow it to automatically reply to a victim’s incoming WhatsApp messages with a payload received from a command-and-control (C&C) server.
“The application is actually designed to monitor the user’s WhatsApp notifications, and to send automatic replies to the user’s incoming messages using content that it receives from a remote C&C server,” Check Point researchers said in an analysis published today.
Besides masquerading as a Netflix app, the malicious “FlixOnline” app also requests intrusive permissions that allow it to create fake Login screens for other apps, with the goal of stealing credentials and gain access to all notifications received on the device, using it to hide WhatsApp notifications from the user and automatically reply with a specially-crafted payload received from the C&C server.
“The malware’s technique is fairly new and innovative,” said Aviran Hazum, manager of mobile intelligence at Check Point. “The technique here is to hijack the connection to WhatsApp by capturing notifications, along with the ability to take predefined actions, like ‘dismiss’ or ‘reply’ via the Notification Manager.”
A successful infection could allow the malware to spread further via malicious links, steal data from users’ WhatsApp accounts, propagate malicious messages to users’ WhatsApp contacts and groups, and even extort users by threatening to leak sensitive WhatsApp data or conversations.
The app has since been purged from the Play Store, but not before attracting a total of 500 downloads over the course of two months.
FlixOnline also marks the second time a malicious app has been caught using WhatsApp to spread the malware. In January 2021, ESET researcher Lukas Stefanko disclosed a fake Huawei Mobile app that employed the same modus operandi to perform the wormable attack.
What’s more, the message displayed to users upon opening the apps is the same — “We need your permission to access the application. It will help app (sic) to provide better functionality” — suggesting the two apps could either be the work of the same attacker or that the authors of FlixOnline drew inspiration from the Huawei Mobile app.
“The fact that the malware was able to be disguised so easily and ultimately bypass Play Store’s protections raises some serious red flags,” Hazum said. “Although we stopped one campaign of the malware, the malware family is likely here to stay. The malware may return hidden in a different app.”
“Users should be wary of download links or attachments that they receive via WhatsApp or other messaging apps, even when they appear to come from trusted contacts or messaging groups,” Hazum added.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.