New Version of Vulners CVE Search API

Problem Statement
In 2024, almost 32,800 Common Vulnerabilities and Exposures (CVE) were published in the National Vulnerability Database (NVD). Given the scale of this data, any vulnerability management strategy requires automated searches for vulnerabilities affecting installed software.
Previously, the NVD served as the primary resource for CVE information, including critical metrics such as Common Weakness Enumeration (CWE) and CVSS. However, its primary function was facilitating automated CVE searches for specific software by verifying, expanding, and normalizing the configuration of affected versions.
The NVD stopped fulfilling this function on February 12, 2024, as the number of CVE processed decreased compared to the number of newly published CVE. Since then, the NVD has issued several communications regarding service improvements, but these have yet to be implemented. Consequently, the backlog of unprocessed CVE continues to grow daily.
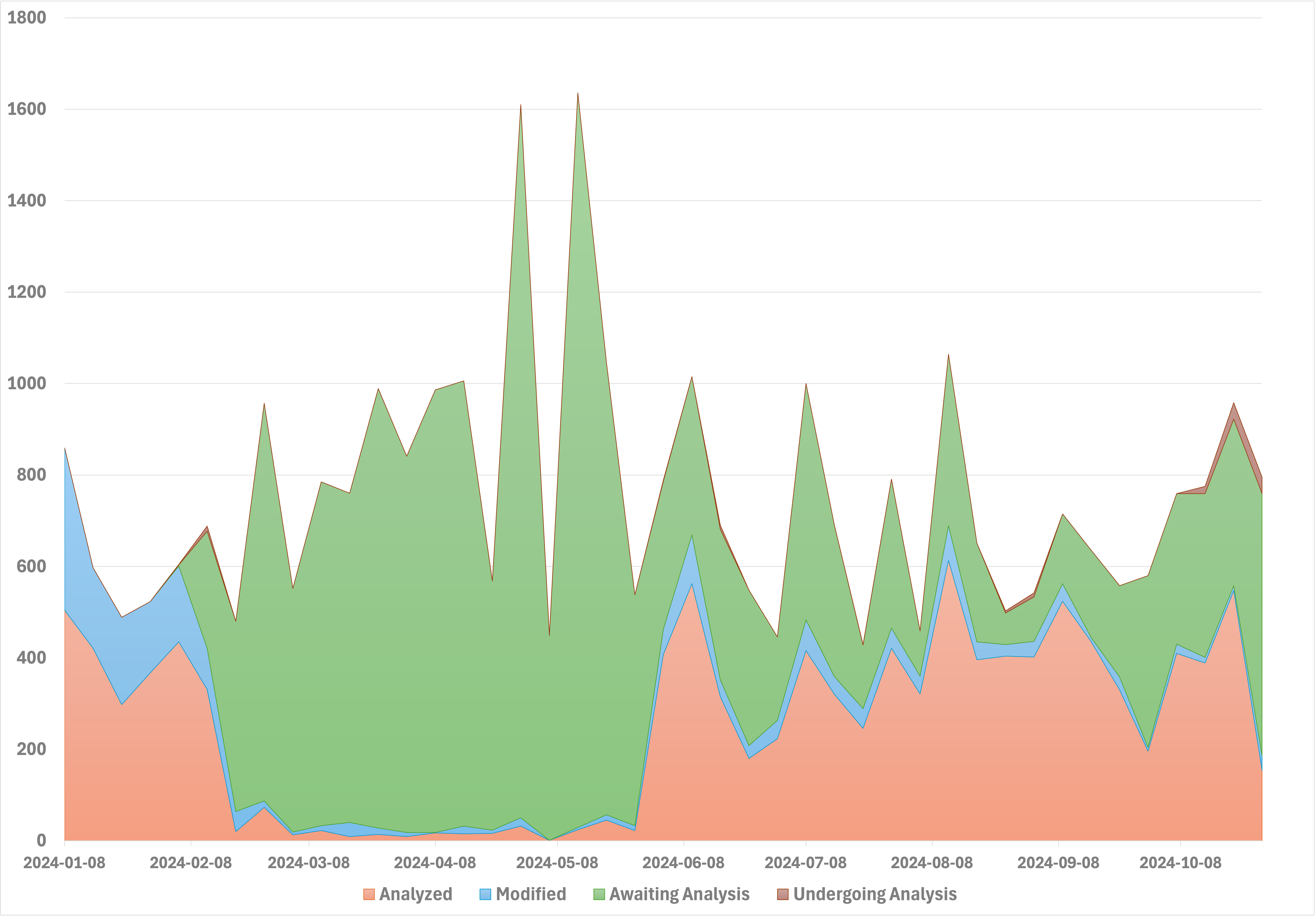
CVE Published in 2024 by Status
This chart illustrates the current status of CVE published in 2024 on a weekly basis. It demonstrates the increasing backlog of unprocessed CVE.
Vulners has been actively working to address this issue. We have developed a new version of the Vulners API to enable accurate search functionality utilizing all available vulnerability data.
Where the Vulnerabilities Affected Version Information Comes From
In this section, we provide a brief overview of primary sources that contain information about software versions that are vulnerable. These sources include CVE Program partners known as CVE Numbering Authorities (CNA), NVD, and the Cybersecurity and Infrastructure Security Agency (CISA) initiative Vulnrichment.
Typically, affected versions information is also included in vendor security advisories. However, it is often aggregated into the aforementioned sources.
CNA
The CVE identifier is assigned by the CNA, which are typically vendors or researchers. The CNA obtain the original bug through the coordinated disclosure process and add it to the CVE List, primarily when a patch is available.
Only three fields are required for CVE submission: CVE ID, a free-form description, and at least one reference to external information about the vulnerability. Affected version information is also required, although unfortunately, it can be bypassed with the “n/a” string. The CVE Program has consistently expressed its preference for ease of publication over stricter rules for CVE submission.
While most CNA provide extensive details about (with MITRE being a notable exception), this information comes in various formats without proper normalization, as it is produced by over 400 independent organizations.
| CVE Count | CNA Count | Product | Vendor | Version | CPE | Package Name | Repo |
|---|---|---|---|---|---|---|---|
| 4378 | 1 | ||||||
| 15733 | 258 | Y | Y | Y | |||
| 3889 | 38 | Y | Y | Y | Y | ||
| 2943 | 24 | Y | Y | Y | Y | ||
| 1269 | 9 | Y | Y | Y | Y | ||
| 511 | 6 | Y | Y | ||||
| 185 | 2 | Y | Y | Y | Y | Y | |
| 157 | 27 | Y | Y | Y | Y | Y | |
| 110 | 2 | Y | Y | Y | Y | Y | |
| 41 | 4 | Y | Y | ||||
| 34 | 2 | Y | Y | Y | |||
| 20 | 3 | Y | Y | ||||
| 19 | 1 | Y | Y | Y | |||
| 3 | 1 | Y | Y | Y | Y | Y | Y |
| 2 | 2 | Y | Y | Y | |||
| 1 | 1 | Y | Y | Y | Y |
Breakdown of number of CVE published with affected configuration blocks by CNA
For the CVE published in 2024, the table above illustrates the presence of key affected software identifications.
Developing robust searches that account for data irregularities necessitates specialized handlers, which Vulners has been actively developing.
To date, our solution has made searchable CVE from the 25+ top CNA.
NVD
The National Vulnerability Database (NVD) is a downstream repository of the CVE Program and, for many years, could have been considered the primary source of information about CVE.
Despite the current service performance and reliability issues, NVD remains a substantial source of affected version configurations for both new and historical CVE.
The enhanced data processing capabilities enabled by new partnerships will likely make NVD the sole source of structured data about CVE published by organizations such as MITRE. As MITRE’s sole approach to rendering their data machine-readable is through manual processing, NVD will become the primary repository for this data.
Vulnrichment
The CISA Vulnrichment project serves as the public repository of CISA’s enrichment of public CVE records through CISA’s ADP (Authorized Data Publisher) container. During this phase of the project, CISA evaluates novel and recently discovered CVE and incorporates pertinent SSVC decision points. Subsequently, certain higher-risk CVE will also receive enrichment of CWE, CVSS, and CPE data points, where feasible.
Although affected configurations in Vulnrichment records may introduce nuances that are not present in corresponding CNA and/or NVD configurations, they generally adhere to the CNA affected configuration format. Consequently, we still require the development of specialized handlers to address the specificities of these formats in order to facilitate their searchability.
Putting it all Together
At the time of writing, out of the almost 32,800 CVE published so far in 2024, approximately CVE 27,600 have meaningful machine-readable affected version information. The Vulners API supports searching for more than 25,800 of those searchable CVE, and more will be supported as we add new CNA handlers.
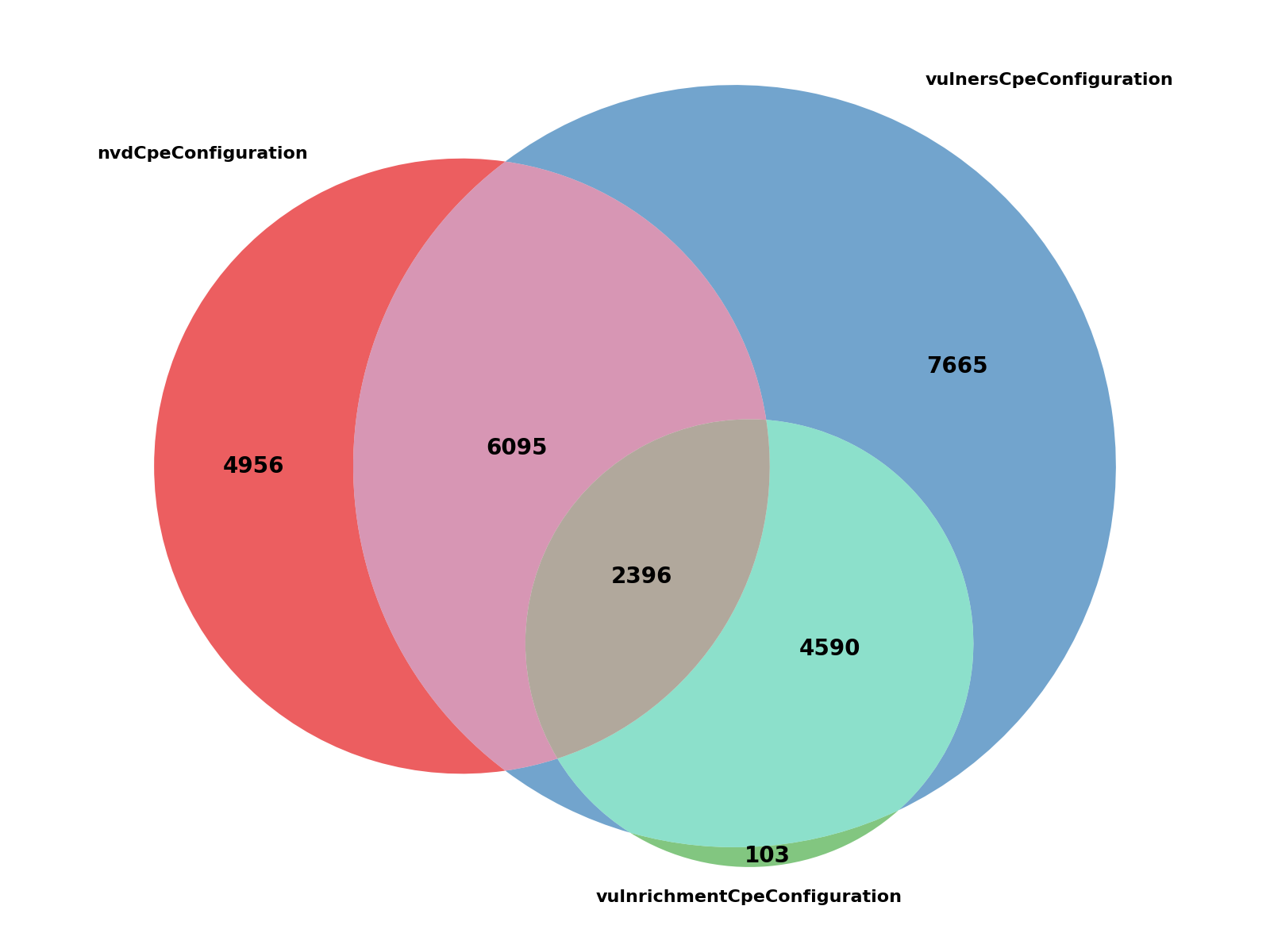
CVE published in 2024 by searchable affected configurations.
Let us now go deeper into the capabilities of the newly released Vulners search API, which enables you to conduct comprehensive searches for vulnerabilities that impact software, specifically by combining vendor, product, and version information.
New Vulners Search API
The latest version of the Vulners API is not merely a theoretical enhancement; it is a practical powerhouse.
With the integration and normalization of data from the National Vulnerability Database (NVD), Vulnrichment, and selected CVE Numbering Authorities (CNA), it now provides a new level of precision. Envision this: simply provide the API with the software name and version, and in milliseconds, receive a comprehensive list of relevant CVE.
You can now audit your systems for vulnerabilities almost instantaneously, whether conducting individual software checks or on large-scale batches. The logic is straightforward—rapid, accurate, and seamless.
The best feature of this new version is its complete backward compatibility, ensuring immediate improvements, even when utilizing our renowned NMAP integration.
Curious to learn more about how to leverage this? Check out the next section for detailed API calls, parameters, and documentation for all you need to get started.
Search vulnerabilities by software name and version
This call facilitates the identification of CVE by utilizing the software name and version as the primary parameters.
The software name may not be an exact match, for instance. "ivanti connect secure", "connect secure", "connect_secure"Please refer to the following illustration for an example of how to use the various software names:
params1 = {
"software": "ivanti connect secure",
"version": "22.3"
}
params2 = {
"software": "connect_secure",
"version": "22.3"
}
The outcomes are indistinguishable for both sets of parameters.
| ## | params1 | params2 | Vulners URL |
|---|---|---|---|
| 1 | CVE-2023-38551 | CVE-2023-38551 | https://vulners.com/cve/CVE-2023-38551 |
| 2 | CVE-2023-39340 | CVE-2023-39340 | https://vulners.com/cve/CVE-2023-39340 |
| 3 | CVE-2023-41719 | CVE-2023-41719 | https://vulners.com/cve/CVE-2023-41719 |
| 4 | CVE-2023-41720 | CVE-2023-41720 | https://vulners.com/cve/CVE-2023-41720 |
| 5 | CVE-2023-46805 | CVE-2023-46805 | https://vulners.com/cve/CVE-2023-46805 |
| 6 | CVE-2024-21887 | CVE-2024-21887 | https://vulners.com/cve/CVE-2024-21887 |
| 7 | CVE-2024-21888 | CVE-2024-21888 | https://vulners.com/cve/CVE-2024-21888 |
| 8 | CVE-2024-21893 | CVE-2024-21893 | https://vulners.com/cve/CVE-2024-21893 |
| 9 | CVE-2024-21894 | CVE-2024-21894 | https://vulners.com/cve/CVE-2024-21894 |
| 10 | CVE-2024-22023 | CVE-2024-22023 | https://vulners.com/cve/CVE-2024-22023 |
| 11 | CVE-2024-22052 | CVE-2024-22052 | https://vulners.com/cve/CVE-2024-22052 |
| 12 | CVE-2024-22053 | CVE-2024-22053 | https://vulners.com/cve/CVE-2024-22053 |
| 13 | CVE-2024-29205 | CVE-2024-29205 | https://vulners.com/cve/CVE-2024-29205 |
The version parameter is checked against the affected versions range for each CVE if specified. The respect_major_version parameter enables limiting the search to only the major version specified in the request. It is set to false by default.
params1 = {
"software": "haxx curl",
"version": "7.85.0",
"respect_major_version": "false",
}
params2 = {
"software": "curl",
"vendor": "haxx",
"version": "7.85.0",
"respect_major_version": "true",
}
The outcomes of these two calls differ. Please refer to the vulnerabilities’ information on the linked pages to comprehend the reasons behind this disparity.
Search vulnerabilities by CPE
This call enables you to search CVE using CPE as the primary parameter. The NVD CPE dictionary, which was previously the canonical source of CPE used in CVE for affected versions configuration, has not been maintained properly for several months. Consequently, CPE may offer greater flexibility, provided that it adheres to the CPE format.
params1 = {
"software": "cpe:2.3:a:microsoft:office:16.0.5456.1001"
}
params2 = {
"software": "cpe:2.3:a:microsoft:office:2016",
"version": "16.0.5456.1001"
}
The outputs of these two calls are identical.
Filtering for Target Operating System
Despite its appeal, the previous sample yielded numerous erroneous positive results. This arises from Microsoft’s distinct methodologies employed in versioning Office for Windows and macOS.
The Windows version of Microsoft Office looks like this 16.0.5456.1001. It is within the vulnerable interval of the Office for macOS that looks like this 16.0.0 – 16.76.23081101 if the target operating system is not specified. So, for example CVE-2023-36896 will be included in the search results, but it is a false positive.
To address this issue, you need to specify the target_sw parameter as follows:
params1 = {
"software": "cpe:2.3:a:microsoft:office:16.0.5456.1001”
}
params2 = {
"software": "cpe:2.3:a:microsoft:office:16.0.5456.1001”,
"target_sw": "windows"
}
This action results in a reduction of the number of outcomes from 55 to only 2.
| ## | params1 | params2 | Vulners URL |
|---|---|---|---|
| 1 | CVE-2021-31940 | https://vulners.com/cve/CVE-2021-31940 | |
| 2 | CVE-2021-31941 | https://vulners.com/cve/CVE-2021-31941 | |
| 3 | CVE-2021-34501 | https://vulners.com/cve/CVE-2021-34501 | |
| 4 | CVE-2021-36941 | https://vulners.com/cve/CVE-2021-36941 | |
| 5 | CVE-2021-38650 | https://vulners.com/cve/CVE-2021-38650 | |
| 6 | CVE-2021-38655 | https://vulners.com/cve/CVE-2021-38655 | |
| ... | |||
| 19 | CVE-2022-26901 | https://vulners.com/cve/CVE-2022-26901 | |
| 20 | CVE-2022-26934 | https://vulners.com/cve/CVE-2022-26934 | |
| 21 | CVE-2022-34717 | CVE-2022-34717 | https://vulners.com/cve/CVE-2022-34717 |
| 22 | CVE-2022-37962 | https://vulners.com/cve/CVE-2022-37962 | |
| 23 | CVE-2022-38048 | https://vulners.com/cve/CVE-2022-38048 | |
| 24 | CVE-2022-41031 | https://vulners.com/cve/CVE-2022-41031 | |
| ... | |||
| 52 | CVE-2023-36767 | https://vulners.com/cve/CVE-2023-36767 | |
| 53 | CVE-2023-36895 | https://vulners.com/cve/CVE-2023-36895 | |
| 54 | CVE-2023-36896 | https://vulners.com/cve/CVE-2023-36896 | |
| 55 | CVE-2024-38200 | CVE-2024-38200 | https://vulners.com/cve/CVE-2024-38200 |
Filtering for Target Hardware Platform
Similarly, Vulnerabilities API enables filtering results by target hardware platform. For instance, refer to CVE-2024-38254 as an example. In this CVE affected configuration for CPE cpe:2.3:o:microsoft:windows_10_22h2:*:*:*:*:*:*:x86:* the NVD likely erroneously included the following affected configuration: Up to (including) 10.0.19045.4894.
For cpe:2.3:o:microsoft:windows_10_22h2:*:*:*:*:*:*:x64:* the affected configuration is Up to (excluding) 10.0.19045.4894. In any case, for 64-bit operating systems, this CVE is not applicable.
With Vulners API, you can use the target_hw parameter to narrow search results for the architecture you actually use, as shown below.
params1 = {
"software": "cpe:2.3:o:microsoft:windows_10_22h2:10.0.19045.4894"
}
params2 = {
"software": "cpe:2.3:o:microsoft:windows_10_22h2:10.0.19045.4894",
"target_hw": "x64"
}
In the results, you can see that there is no CVE for the first configuration.
| ## | params1 | params2 | Vulners URL |
|---|---|---|---|
| 1 | CVE-2024-38254 | https://vulners.com/cve/CVE-2024-38254 |
Also, when you use this parameter, NVD “Running on” conditions are analyzed and applied.
Try it out!
This great new version of Vulners search API is already in production. We are continue working hard to make it even better by adding more handlers to support CVE published by more CNA.
And we really want you to try it out — all you need to do is create an account on the Vulners website and start a free trial. This trial comes with no strings attached and provides you with access to the Vulners API on the Pro subscription for 30 days.
