Project zero on the move, vulnerabilities in theWild and Nginx malware

Mostly an ordinary week with critical vulnerabilities in ZOOM, Zoho and Mazilla, but Google Project Zero on the move. Also, a couple of cool malware.
- Vulnerabilities: Mozilla NSS, ZOOM and Zoho vulnerability in the Wild;
- Tools: OffensiveRust, ZipExec and ShonyDanza;
- News: NginRAT and Yanluowang ransomware;
- Research: mostly Detection and Response.
Vulnerabilities

Vulnerability in the NSS library
Tavis Ormandy of Google Project Zero has posted details of a vulnerability in Mozilla's NSS cryptographic library. The vulnerability was identified as CVE-2021-43527. It can be used by an attacker to crash a vulnerable application and even execute arbitrary code. The vulnerability affects versions of NSS prior to 3.73 and relates to a heap overflow in digital signature verification. A fix for this vulnerability has already been released by Mozilla.

Researcher from Google Project Zero discovered vulnerabilities that affect the flagship client for online conferencing on almost all major platforms (Windows, macOS, Linux, iOS and Android) and can be exploited for RCE-related attacks:
- CVE-2021-34423: Buffer Overflow Vulnerability. Could potentially allow an attacker to cause a service or application to crash, or exploit this vulnerability to execute arbitrary code across a wide range of components and SDKs for the company's products.
- CVE-2021-34424: causes memory corruption and can detect process memory status in some Zoom products and components. The vulnerability could potentially extract information from arbitrary areas of the product's memory.
To improve the security of its customers, Zoom has added an automatic update mechanism to the desktop version of the product.

Zoho recommends patching as soon as possible: ManageEngine bug is already being exploited by hackers
Zoho developers urged their customers to urgently update Desktop Central and Desktop Central MSP to the latest version available. The fact is that the new critical vulnerability CVE-2021-44515 in ManageEngine is already under attack.
The vulnerability allows attackers to bypass authentication and then execute arbitrary code on unpatched installations of ManageEngine Desktop Central (Desktop Central Cloud is not affected by the issue).
Tools
OffensiveRust: Experiments in weaponizing Rust for implant development and general offensive operations.
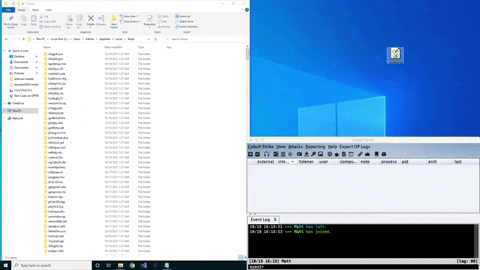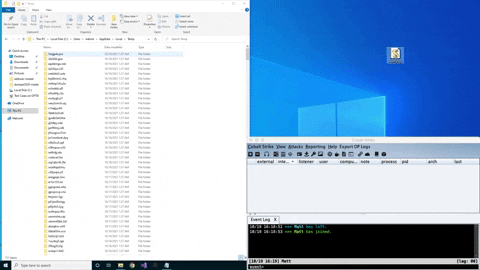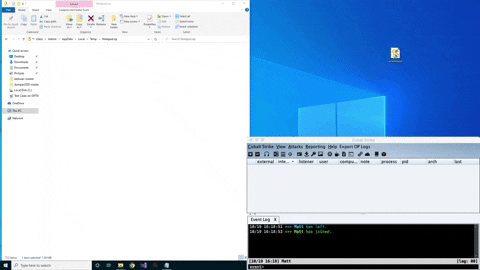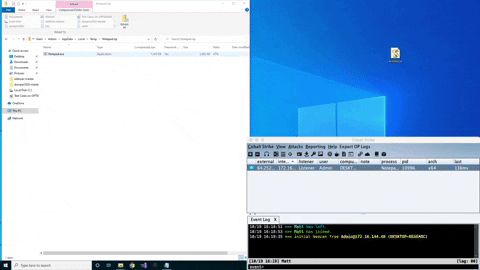
ZipExec is a tool to execute binary payloads stored in password-protected zip files without extracting them. ZipExec smuggles zip files on disk using Jscript & COM objects to create the zip file on disk and then execute them. Check it out
ShonyDanza: customizable, easy-to-navigate tool for researching, pen testing, and defending with the power of Shodan.
News
Researchers Sansec have published a report on the results of an analysis of a new NginRAT malware that was found on e-commerce servers infected with another CronRAT malware. The researchers note that NginRAT masquerades as legitimate Nginx web server processes. When a web server uses standard functions (for example, dlopen), the malware intercepts the request and injects itself into the body of a legitimate process. Since NginRAT is hidden as a normal Nginx process, and the code exists only in the server's memory, it is quite difficult to detect malware.

Symantec managed to track down some of the features of the Yanluowang ransomware. The ransomware has been used by an attacker who has been conducting targeted attacks against US corporations since at least August 2021. The financial sector is the main target of hackers, but they also work for industrial, IT, consulting and engineering companies.
As part of the attacks, the adversary uses PowerShell to download various payloads to the compromised machines, and the RDP protocol is enabled in the registry for remote access to the compromised machine. The ConnectWise remote access tool is also being deployed.
Research
XMGoat - An Open Source Pentesting Tool for Azure - XM Cyber: https://www.xmcyber.com/xmgoat-an-open-source-pentesting-tool-for-azure
Detection and Response for Linux Reflective Code Loading Malware— This is How: https://medium.com/confluera-engineering/detection-and-response-for-linux-reflective-code-loading-malware-this-is-how-21f9c7d8a014
Reflective Code Loading in Linux — A New Defense Evasion Technique in MITRE ATT&CK v10: https://medium.com/confluera-engineering/reflective-code-loading-in-linux-a-new-defense-evasion-technique-in-mitre-att-ck-v10-da7da34ed301
EPP, EDR, MDR & XDR: What’s the Difference? https://medium.com/technology-hits/epp-edr-mdr-xdr-whats-the-difference-f2d58db3985d
Feedback and Vulners docs
xdr-whats-the-difference-f2d58db3985d](https://medium.com/technology-hits/epp-edr-mdr-xdr-whats-the-difference-f2d58db3985d)
Feedback and Vulners docs
