Several critical vulnerabilities, $$$ for hacker info and new attack vectors

There hasn't been much news over the past week, but we've collected the brightest. Several critical vulnerabilities and a couple of news. Noteworthy - updates of cool tools like impacket, APT-hunter and in the research section of the toolset APT groups.
- Vulnerabilities: GitHub exploit in the wild, Android patch and Linux kernel;
- Tools: APT-Hunter V2.0 release, PyRDP, HandleKat, LDAP Monitor;
- News: Trojan Source Attack and rewards for hackers info;
- Research: DFIR reports, tools and research.
Vulnerabilities

GitLab warned users about an increase in the activity of attackers associated with the exploitation of the critical vulnerability CVE-2021-22205, which allows remotely without authentication to execute code on a server on which the GitLab collaborative development platform is used.

November Android patches fix 0-day vulnerability used for APT
The 0-day vulnerability CVE-2021-1048 was exploited in the wild. The bug lies in the kernel of the operating system, which can be used for local privilege escalation. There are no technical details yet about this vulnerability and its exploitation in attacks, as OEMs are still working to integrate the patch into their builds and most Android users are still vulnerable.
Other important November patch vulnerabilities:
- CVE-2021-0918 and CVE-2021-0930 allow attackers to execute arbitrary code in the context of a privileged process by simply sending a specially prepared payload to the victim's device;
- CVE-2021-1924 and CVE-2021-1975 affect closed source Qualcomm components;
- CVE-2021-0889 on Android TV allows an attacker in close proximity to the victim to invisibly connect to a device and execute arbitrary code without any user interaction.
Google has rolled out patches for 38 flaws.

CVE-2021-43267 in Linux kernel
In the Linux kernel of the implementation of the TIPC (Transparent Inter-process Communication) network protocol, a critical vulnerability CVE-2021-43267 has been identified, which allows you to remotely execute your code with kernel privileges by sending a specially designed network packet. The danger of the problem is mitigated by the fact that the attack requires explicitly enabling TIPC support in the system (loading and configuring the tipc.ko kernel module), which is not done by default in non-specialized Linux distributions.
Tools

APT-Hunter V2.0 release. Major changes that will provide an easier way to analyze and detect suspicious activity with support for more than 200 use cases and new features to help you in your next DFIR case.
PyRDP: a Python Remote Desktop Protocol (RDP) Monster-in-the-Middle (MITM) tool and library.
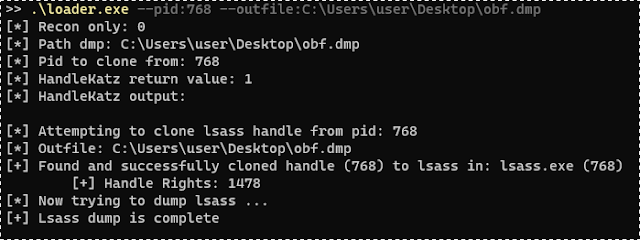
HandleKat: demonstrates the usage of cloned handles to Lsass in order to create an obfuscated memory dump of the same.
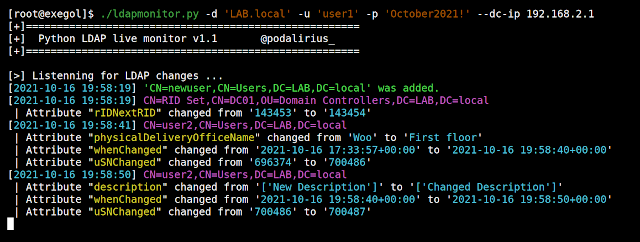
LDAP Monitor: Monitor creation, deletion and changes to LDAP objects live during your pentest or system administration
News

Trojan Source Attack
Scientists at the University of Cambridge in the United Kingdom have uncovered a Trojan Source attack vector discovered on July 25, which allows vulnerabilities to be injected into software source code so that reviewers cannot find them, which poses a threat to popular software and supply chains.
Trojan Source uses a simple technique that does not require any compiler modification or other tweaks, affecting C, C ++, C #, JavaScript, Java, Rust, Go, and Python. The point is to use Unicode control characters to reorder tokens in the source code at the encoding level.
Trojan Source is implemented according to two scenarios: CVE-2021-42574 (or bi-directional attack) and CVE-2021-42694 (homoglyphic attack).

U.S. authorities are willing to pay $10 million for information on the leaders of the cybercrime group DarkSide.
DarkSide is a group of Russian-speaking hackers, has this year carried out a cyberattack on Colonial Pipeline, the largest U.S. supplier of gas and oil products. The State Department is also offering a reward of up to $5 million for information that would help arrest in any country those who temporarily joined the hackers or assisted in any criminal act by DarkSide.
Research
See what's in your Docker https://contains.dev
Impacket v0.9.24 Released https://www.secureauth.com/blog/impacket-v0-9-24-released
New awesome report on theDFIRreport: From Zero to Domain Admin
Trojan Source: Invisible Vulnerabilities https://www.trojansource.codes/trojan-source.pdf
BlackMatter: New Data Exfiltration Tool Used in Attacks: https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/blackmatter-data-exfiltration
Advanced IP Scanner: the preferred scanner in the A(P)T toolbox: https://www.huntandhackett.com/blog/advanced-ip-scanner-the-preferred-scanner-in-the-apt-toolbox
Feedback and Vulners docs
eferred-scanner-in-the-apt-toolbox](https://www.huntandhackett.com/blog/advanced-ip-scanner-the-preferred-scanner-in-the-apt-toolbox)
Feedback and Vulners docs
