Critical RCE Vulnerability Reported in Linux Kernel's TIPC Module
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
Cybersecurity researchers have disclosed a security flaw in the Linux Kernel’s Transparent Inter Process Communication (TIPC) module that could potentially be leveraged both locally as well as remotely to execute arbitrary code within the kernel and take control of vulnerable machines.
Tracked as CVE-2021-43267 (CVSS score: 9.8), the heap overflow vulnerability “can be exploited locally or remotely within a network to gain kernel privileges, and would allow an attacker to compromise the entire system,” cybersecurity firm SentinelOne said in a report published today and shared with The Hacker News.
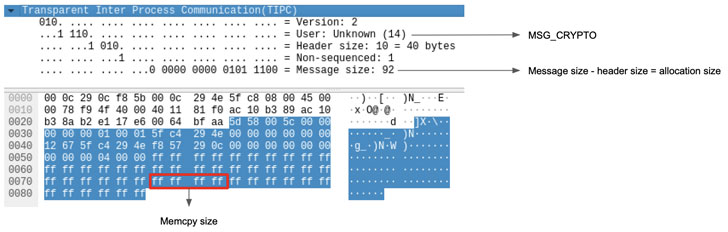
TIPC is a transport layer protocol designed for nodes running in dynamic cluster environments to reliably communicate with each other in a manner that’s more efficient and fault-tolerant than other protocols such as TCP. The vulnerability identified by SentinelOne has to do with insufficient validation of user-supplied sizes for a new message type called “MSG_CRYPTO” that was introduced in September 2020 and enables peer nodes in the cluster to send cryptographic keys.
While the protocol has checks in place to validate such messages after decryption to ensure that a packet’s actual payload size doesn’t exceed that of the maximum user message size and that the latter is greater than the message header size, no restrictions were found to be placed on the length of the key (aka ‘keylen’) itself, resulting in a scenario where “an attacker can create a packet with a small body size to allocate heap memory, and then use an arbitrary size in the ‘keylen’ attribute to write outside the bounds of this location.”
There is no evidence that the flaw has been abused in real-world attacks to date, and following responsible disclosure on October 19, the issue has been addressed in Linux Kernel version 5.15 released on October 31, 2021.
“The function tipc_crypto_key_rcv is used to parse MSG_CRYPTO messages to receive keys from other nodes in the cluster in order to decrypt any further messages from them,” Linux kernel maintainers said in a fix pushed late last month. “This patch verifies that any supplied sizes in the message body are valid for the received message.”
“While TIPC itself isn’t loaded automatically by the system but by end users, the ability to configure it from an unprivileged local perspective and the possibility of remote exploitation makes this a dangerous vulnerability for those that use it in their networks,” SentinelOne researcher Max Van Amerongen said.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P