Continuous patching Microsoft, tons of zero-days for one month and other "mistakes"

Month of non-stop Microsoft fixes and even if you install everything, you still remain vulnerable (PrintNightmare is a real nightmare). There were also many zero-days that everyone was so used to and did not have time to patch. Be sure to check the Research part of the review for a lot of useful stuff.
- Vulnerabilities: Miscrorosft, Exchange servers, OpenVpn, Citrix, VMware and Sitecore (CMS);
- Tools: MultiPotato (yes, more potatoes), DetectionLabELK, PyRDP and Abaddon;
- News: New malware and GoDaddy data leaks;
- Research: different investigations, tips and tricks, new tools and others lovely things
Vulnerabilities

CVE-2021-41379 zero-day
The researcher Abdelhamid Naseri has published an exploit for the Windows 0-day vulnerability CVE-2021-41379, which was patched by Microsoft as part of Patch Tuesday. The researcher was able to bypass the hotfix and identify a more critical vector of exploitation that allows obtaining administrator rights on all supported versions of Windows, including Windows 10, Windows 11 and Windows Server 2022. The vulnerability works even if the ability to perform an MS Installer operation for unprivileged users.
You can make sure that the exploit actually works on the video (the test was carried out on a completely updated Windows 10 21H1 build 19043.1348)

PoC has been reported for high severity vulnerability CVE-2021-42321 affecting on-premises Exchange Server 2016 and Exchange Server 2019 (including those used by clients in Exchange hybrid mode). The vulnerability was patched after the release of Patch Tuesday.
Successful exploitation of RCE enables Exchange-authorized attackers to remotely execute code on vulnerable servers.
It's recommended to check the state of Exchange and analyze events in the Windows log to identify attempts to exploit CVE-2021-42321, and then roll up all the patches suggested by the developer.

Claroty warned that products built on OpenVPN are at risk of five serious arbitrary code execution vulnerabilities that can be achieved if a victim visits a malicious page. In particular, the bugs affected the solutions of such companies as HMS Industrial Networks, MB connect line, PerFact and Siemens.
During the analysis of solutions based on OpenVPN, Claroty discovered critical code execution vulnerabilities:
- CVE-2020-14498: eCatcher HMS Industrial Networks AB;
- CVE-2021-27406: OpenVPN client PerFact;
- CVE-2021-31338: SINEMA RC client from Siemens), as well as CVE-2021-33526;
- CVE-2021-33527: MB connect line GmbH mbConnect Dialup.
VPN solutions are designed to provide users with a means of encrypting traffic between their devices and a specific network to ensure that potentially sensitive data is transmitted securely, and OpenVPN is the most common VPN implementation.

VMware Releases New Update Patch Addressing Two Security Bugs in vCenter Server and Cloud Foundation
The most critical vulnerability CVE-2021-21980 relates to random file reading in the vSphere web client. Anyone with network access to port 443 on vCenter Server can exploit this vulnerability to gain access to sensitive information.
CVE-2021-22049 is less dangerous than the previous one and affects the vSphere web client. The SSRF (Server-Side Request Forgery) vulnerability allows an attacker to read or modify internal resources to which the target server has access by sending specially crafted HTTP requests, which, in fact, leads to unauthorized disclosure of information.

The popular enterprise-grade content management system with data analytics (CMS) Sitecore XP has an actively exploited vulnerability CVE-2021-42237. The product is used by well-known companies such as American Express, IKEA, Carnival Cruise Lines, L'Oréal and Volvo.
The remote code execution vulnerability fixed on October 13 affects the Sitecore Experience Platform (Sitecore XP) in versions 7.5 (with Update-2), 8.0 (with Update-7), 8.1 (with Update-3), 8.2 (with Update-7).
The point is that a detailed technical review RCE released Assetnote, which allowed hackers to reproduce necessary exploits and start actively exploiting vulnerable websites.
It is recommended that platform users upgrade to a secure version as soon as possible, ideally Sitecore XP 9.0 or higher. Or alternatively delete the Report.ashx file from /sitecore/shell/ClientBin/Reporting/ on all server instances.

Citrix has released fixes for several vulnerabilities affecting Citrix ADC, Gateway, and SD-WAN, including a critical denial of service (DoS) bug.
The first is the critical vulnerability CVE-2021-22955, which can lead to a DoS condition on devices configured as a VPN virtual server (gateway) or AAA. The flaw was found in Citrix Application Delivery Controller (ADC, formerly NetScaler ADC) and Gateway (formerly NetScaler Gateway).
The second bug CVE-2021-22956 can temporarily break the interaction with the GUI, Nitro API and RPC. It affects the ADC and Gateway as well as SD-WAN WANOP models 4000-WO 4100-WO, 5000-WO, and 5100-WO.
Citrix has fixed both vulnerabilities. Citrix customers are encouraged to install the available hotfixes as soon as possible.
Tools
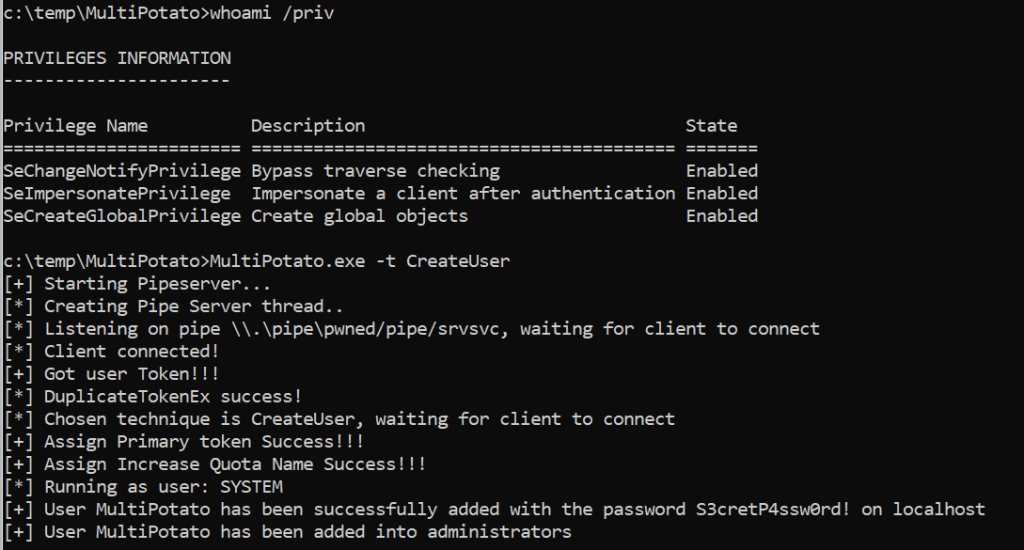
MultiPotato: It is just another Potato to get SYSTEM via SeImpersonate privileges
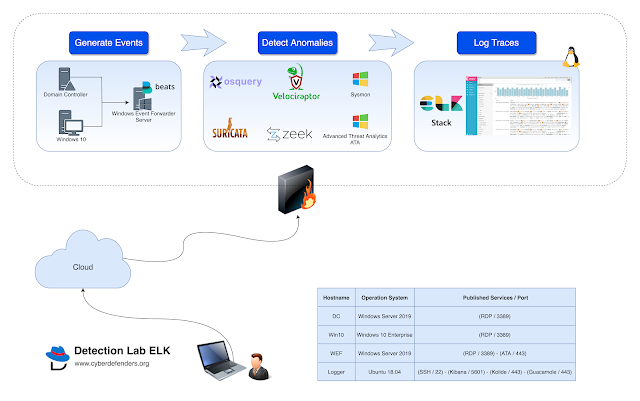
DetectionLabELK: Fork from Chris Long’s DetectionLab with ELK stack instead of Splunk.
PyRDP: Python Remote Desktop Protocol (RDP) Monster-in-the-Middle (MITM) tool and library.
PyRDP on Autopilot – Unattended Credential Harvesting and Client-Side File Stealing

Red Team's operations require a lot of monitoring, consolidation, and caution. Abaddon: Red Team Wavestone's operations management software, was designed to make the Red Team's work faster and easier, including additional tools and multiple reporting capabilities.
News
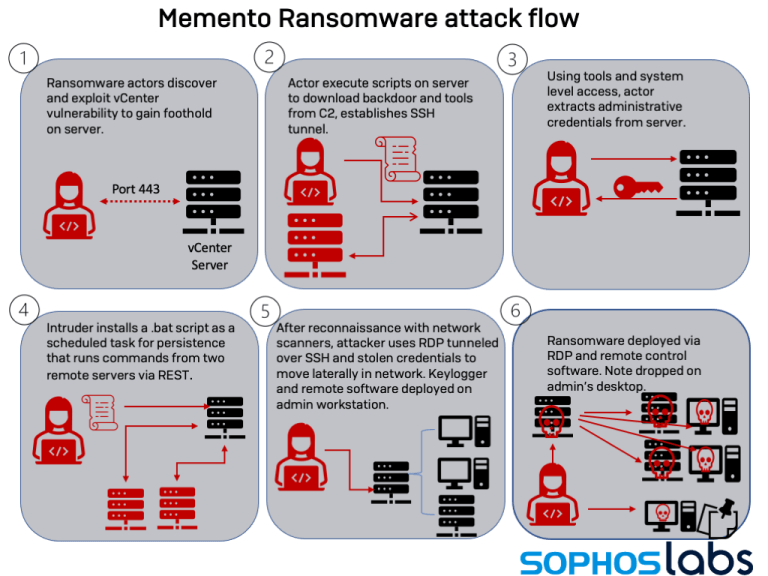
Memento Team ransomware moves data to archive with password instead of file encryption
Sophos MTR's Rapid Response Team reported the ransomware used by the Memento Team does not encrypt files - instead, it copies them into an archive that protects them with an encrypted password, and finally deletes all original files. This technique allows Memento Team to bypass the antiviruses installed on the computers of the victims. The ransomware itself is a Python 3.9 script compiled with PyInstaller.

Domain name registrar GoDaddy reports about data leak
The largest domain name registrar GoDaddy reported that the data of about 1.2 million of its customers were compromised by third parties. The incident was discovered on November 17th. However, according to preliminary data, the attackers had access to the GoDaddy network since September 6, 2021. Cybercriminals managed to compromise the provisioning system password in a legacy Managed WordPress codebase.
- WordPress admin password set at the time of installation;
- SFTP, database users & passwords;
- SSL private keys.

Malware from the AppGallery catalog penetrated at least 9.3 million Android devices
Doctor Web researchers have detected the Cynos Trojan in the official app store for Huawei devices, AppGallery. This malware collects information about users' mobile numbers and other data about devices. In total, applications infected with Cynos have been installed more than 9.3 million times.
Research
GoSecure Investigates Abusing Windows Server Update Services (WSUS) to Enable NTLM Relaying Attacks https://www.gosecure.net/blog/2021/11/22/gosecure-investigates-abusing-windows-server-update-services-wsus-to-enable-ntlm-relaying-attacks
Hunting for Persistence in Linux (Part 1): Auditd, Sysmon, Osquery, and Webshells: https://pberba.github.io/security/2021/11/22/linux-threat-hunting-for-persistence-sysmon-auditd-webshell
Hunting for Persistence in Linux (Part 2): Account Creation and Manipulation: https://pberba.github.io/security/2021/11/23/linux-threat-hunting-for-persistence-account-creation-manipulation
THM is an online platform for learning Cybersecurity. Deploy machines and follow guides to enhance your security skills. https://tryhackme.com
Android Penetration Testing. https://github.com/Ignitetechnologies/Android-Penetration-Testing
If you rename procdump.exe to dump64.exe and place it in the "C:\Program Files (x86)\Microsoft Visual Studio\*" folder, you can bypass Defender and dump LSASS.
DNS Over HTTPS for Cobalt Strike: https://www.blackhillsinfosec.com/dns-over-https-for-cobalt-strike
DLL Hollowing - This variant of memory allocation removes the prerequisite of having write access to the target DLL (in contrast to Phantom DLL Hollowing) and is stealthier than “classic” Dll Hollowing (which uses the LoadlLibrary API) as we keep the benefits of storing the payload in a legit DLL. https://www.secforce.com/blog/dll-hollowing-a-deep-dive-into-a-stealthier-memory-allocation-variant
No Logs? No Problem! Incident Response without Windows Event Logs: https://labs.jumpsec.com/no-logs-no-problem-incident-response-without-windows-event-logs
Infect If Needed | A Deeper Dive Into Targeted Backdoor macOS.Macma https://www.sentinelone.com/labs/infect-if-needed-a-deeper-dive-into-targeted-backdoor-macos-macma
Investigating Unauthorized Access: Huntress QA Environment Incident https://www.huntress.com/blog/investigating-unauthorized-access-huntress-qa-environment-incident
New great DFIR report: https://thedfirreport.com/2021/11/29/continuing-the-bazar-ransomware-story
Feedback and Vulners docs
om/2021/11/29/continuing-the-bazar-ransomware-story](https://thedfirreport.com/2021/11/29/continuing-the-bazar-ransomware-story)
Feedback and Vulners docs
