Lucky month for law enforcement, patching vulnerabilities and fighting malware

There is a lot of news this month about large-scale investigations by law enforcement agencies and other good guys. The release of decryptors undermines the ransomware business and is an effective way to combat them. Also, as usual, there were packs of updates/fixes from major vendors.
Did you check out the new search in the Vulners database? Feedback is welcome!
- Vulnerabilities: Cisco, Apple, AUVESY (so fast), Chrome updates and OptinMonster WordPress plugin;
- Tools: BlackByteDecryptor, LazyCSRF, GitOops, SpoolSploit, karma_v2;
- News: couple about Europol operations, couple for Avast, NPM hacked;
- Research: articles for Defenders guys.
Vulnerabilities

Cisco SD-WAN is a cloud-based WAN overlay architecture that enables digital and cloud integration for enterprises, and connects disparate offices through the cloud.
CVE-2021-1529 is related to insufficient validation of input by the system CLI. An attacker could exploit this vulnerability by authenticating to the vulnerable device and submitting the generated input to the system command line interface. A successful exploit could allow an attacker to execute commands on the operating system with root privileges.
Update now!

AUVESY fixed pack with critical vulnerabilities
Claroty has added 17 that were found in the Versiondog software developed by the German company AUVESY. AUVESY specializes in data management developments for industrial automation. Versiondog implements the functions of automatic data backup, control and storage of versions of various software, integrating into a wide range of industrial systems. To date, it is actively used in such large companies as Nestle, Coca Cola, Kraft Foods, Merck, etc.
The identified vulnerabilities in the OS Server API, Scheduler, and WebInstaller components can be exploited by remote attackers to bypass authentication, escalate privileges, obtain hardcoded crypto keys, execute arbitrary code, manipulate files and data, and invoke denial of service. Six vulnerabilities were rated critical severity and nine vulnerabilities were rated high severity.
AUVESY not only released fixes for vulnerabilities (version 8.1), but also fixed the root causes of their occurrence. Note that the German manufacturer was really quick to release the necessary updates.

Apple newI
Apple has released the final version of iOS 15.1 for all of its devices. The build number is 19B74.
In the new version of the OS, it became possible to add vaccination certificates to Wallet, a macro mode switch for the iPhone 13 appeared, and the SharePlay function for sharing music and watching movies was launched.
Given the size of the update, security holes have also been fixed (not disclosed) and overall stability has been improved.
Apple released iOS 14.8.1, iPadOS 14.8.1, watchOS 8.1 and tvOS 15.1, patching 24 CVEs in total.

Google has released an update for the Chrome 95 browser that fixes two actively exploited vulnerabilities in Chrome, as well as a number of bugs discovered during the Chinese Tianfu Cup.
- CVE-2021-38000: Invalid input validation in Intents function;
- CVE-2021-38003: a problem in the implementation of JavaScript V8 and WebAssembly engines Vulnerabilities allow attackers to remotely execute code or take control of the target system. The latest Chrome 95 update includes 8 security fixes, 7 of which are critical.
More than a dozen Chrome vulnerabilities discovered this year have been actively exploited by attackers, according to Google Project Zero.

OptinMonster relies on API endpoints that provide seamless integration and a streamlined design process. However, the implementation of these endpoints is not always secure, such as with the /wp-json/omapp/v1/support endpoint, which can expose data such as the full path to the site on the server, API keys used for site requests, and much more.
An attacker with an API key could alter OptinMonster accounts or even post malicious JavaScript snippets on the site. The site will execute this code every time the OptinMonster item is activated.
Owners of sites with OptinMonster are advised to upgrade to version 2.6.5 or later as soon as possible.
Tools
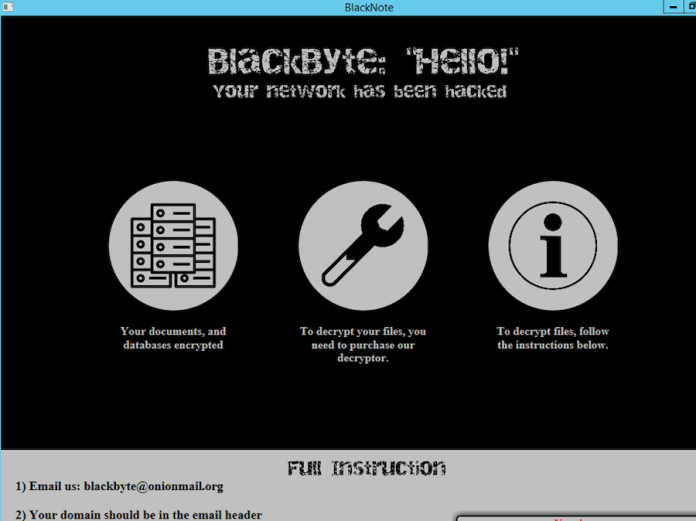
Victims of BlackByte ransomware can use to decrypt and recover their files without paying the ransom.
https://github.com/SpiderLabs/BlackByteDecryptor
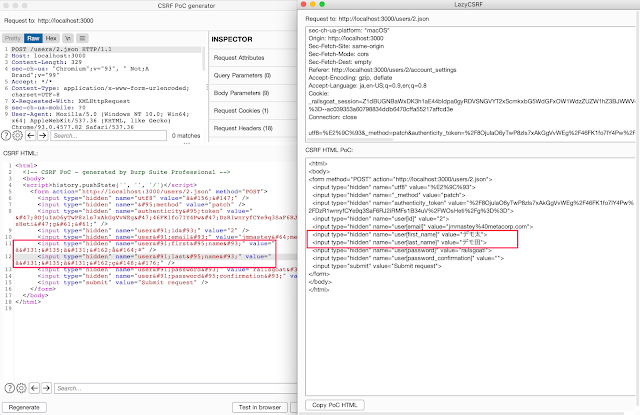
LazyCSRF is a more useful CSRF PoC generator that runs on Burp Suite.
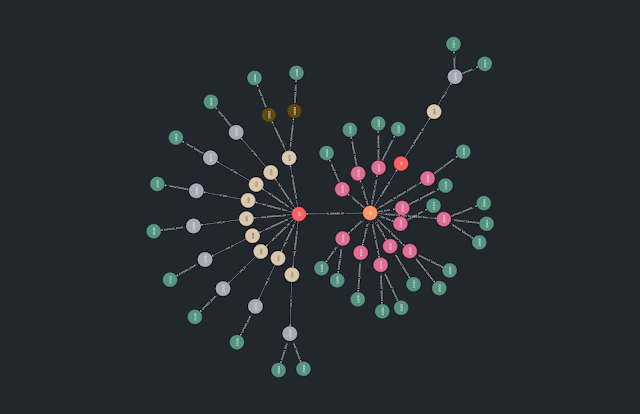
GitOops is a tool to help attackers and defenders identify lateral movement and privilege escalation paths in GitHub organizations by abusing CI/CD pipelines and GitHub access controls.
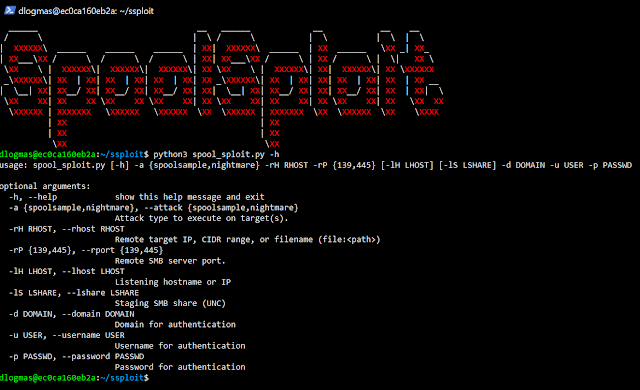
SpoolSploit: A collection of Windows print spooler exploits containerized with other utilities for practical exploitation.

Karma_v2: Passive Open Source Intelligence (OSINT) Automated Reconnaissance (framework)
News

Europol continues to investigate the ransomware gangs behind the attack on Norsk Hydro
The attackers used LockerGoga, MegaCortex, and Dharma strains, as well as Trickbot malware and Cobalt Strike post-exploitation tools. LockerGoga first appeared in January 2019 when it hit the French company Altran Technologies, part of the Capgemini group. Most resonant was the attack on the Norwegian aluminum giant Norsk Hydro, which caused operational disruptions and the company had to pay a ransom of 800 million Norwegian kroner.
European law enforcement has arrested 12 people believed to have been linked to ransomware attacks that have targeted more than 1,800 companies in 71 countries. Arrests took place in Ukraine and Switzerland on October 26, 2021, and as a result of simultaneous raids, police seized five luxury cars, electronic devices and $ 52,000 in cash.
The operation involved more than 50 investigators from seven European police departments, six Europol specialists, as well as the FBI and the US Secret Service.

Europol conducted a special operation called Dark HunTOR in eight countries in Europe and the United States. A total of 150 suspects were arrested, more than €26 million were confiscated, 234 kg of drugs and 45 firearms were seized.
The mass arrests were made possible by the operation of the intelligence services, which managed to gain access to the infrastructure of the world's largest darknet market of illegal services after the arrest of DarkMarket admins and its closure in January of this year.
Avast decryptor
Avast has released a free decryptor that helps recover data after being infected with AtomSilo and LockFile malware. LockFile ransomware was first discovered in July 2021 and attacked its victims using vulnerabilities in Microsoft Exchange. The AtomSilo malware was discovered relatively recently and exploits vulnerabilities in Confluence Server and Data Center for its attacks.

Millions of Android Users Affected by a Scam Campaign
Researchers from Avast have discovered a massive malware campaign (UltimaSMS) that has targeted Android users around the world. The campaign included about 80 related apps that experts found on Google Play. Google representatives promptly removed all malicious applications, but the attackers managed to complete transactions worth several million dollars.
Attackers attacked the NPM package manager
As a result of the cyber attack, the UA-Parser-JS library was hacked, which can be used to load malicious samples on Linux and Windows devices. The UA-Parser-JS library is used to parse the browser user agent to identify the browser, engine, OS, CPU, and visitor device type / model. This library is used in such popular projects as: Facebook, Microsoft, Amazon, Instagram, Google, Slack, Mozilla, etc.
I was surprised by the hacker selectivity of its targets, since the malicious script checked IP addresses in the freegeoip.app service and did not launch the malicious application for users from Russia, Ukraine, Belarus and Kazakhstan.
Sinclair Broadcast Group is one of the largest media empires in the US, controlling 294 TV channels in 89 US markets. Dozens of Sinclair stations from Washington to Maryland and from Illinois to Texas went offline. The incident occurred early in the morning and disabled Sinclair's internal corporate network, mail servers, telephone services and local TV broadcasting systems. As a result of the attack, a huge number of channels were unable to broadcast morning shows, news, including the planned NFL games.
Research
Microsoft Digital Defense Report shares new insights on nation-state attacks: https://www.microsoft.com/security/blog/2021/10/25/microsoft-digital-defense-report-shares-new-insights-on-nation-state-attacks
Create a proxy DLL with artifact kit - Cobalt Strike Research and Development: https://blog.cobaltstrike.com/2021/10/29/create-a-proxy-dll-with-artifact-kit
Threat matrix for CI/CD Pipelines: https://github.com/rung/threat-matrix-cicd
Detecting EDR Bypass: Malicious Drivers(Kernel Callbacks): https://posts.bluraven.io/detecting-edr-bypass-malicious-drivers-kernel-callbacks-f5e6bf8f7481
Announcing Microsoft live response for macOS and Linux: https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/announcing-live-response-for-macos-and-linux/ba-p/2864397
Feedback and Vulners docs
ttps://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/announcing-live-response-for-macos-and-linux/ba-p/2864397)
Feedback and Vulners docs
