Open-source Twitter, weekly google patches and other fails

Twitter has become an open source project this week. Check out the cool research from ESET and Kaspersky teams. A typical week in information security. Vulners is helping thousands of users stay away from Twitter this week. Don't be like heroes from our news, install patches and keep an eye on security.
- Vulnerabilities: Apache, Honeywell Experion PKS and ACE controllers, Android and Google;
- Tools: Scrummage, GitOops and SpoolSploit;
- News: Twitter, ESET and Kaspersky reports;
- Research: Not as much as always.
Feedback and Vulners docs
Vulnerabilities

The Apache Software Foundation released version 2.4.50 of the HTTP web server to fix 2 vulnerabilities:
CVE-2021-41773: Discovered by cPanel on September 29, 2021 and allows subjects to map URLs to files outside the expected document root by launching a path traversal attack. For the attack to work, the victim must be running Apache HTTP Server 2.4.49 and have the 'require all denied' access control disabled (default configuration). 2.4.50 fixes 0-day CVE-2021-41773 after update 2.4.50 was not fully fixed (new vulnerability was named CVE-2021-42013) and therefore version 2.4.51 was released.
CVE-2021-41524: HTTP/2 request processing vulnerability that allow an attacker to perform a denial of service (DoS) on a server.
It is highly recommended for Apache users to install fixes as soon as possible and mitigate the risks associated with active exploitation of vulnerabilities.

Critical vulnerabilities found in Honeywell Experion PKS and ACE controllers
The vulnerabilities were discovered by Claroty, affecting all versions of Honeywell Experion Process Knowledge System C200, C200E, C300 and ACE controllers:
- CVE-2021-38397 (CVSS: 10.0) - Unlimited download of dangerous file type.
- CVE-2021-38395 (CVSS: 9.1) - Incorrect neutralization of special items in the output used by the downstream component.
- CVE-2021-38399 (CVSS: 7.5) Path Traversal.
All of these vulnerabilities are related to the code loading procedure, which is required to program the logic running in the controller, which allows an attacker to mimic the process and load arbitrary CLL binaries.
It is highly recommended that you install the hotfixes as soon as possible to fully fix these vulnerabilities

More than 50 new security fixes for the Android mobile operating system
10 vulnerabilities were fixed with updates from 10.01.2021. The most critical vulnerability in CVE-2021-0870 is related to a bug in an operating system component that can be used for remote code execution.
The following update fixes 41 vulnerabilities, 3 of which are critical. According to Google, the most critical of these is a bug in system components. The vulnerability affects Android 8.1, 9, 10, 11 and is tracked as CVE-2021-0870. A critical vulnerability could allow a remote attacker to execute arbitrary code in the context of a privileged process. The remaining 40 issues affect the core, telecom and Qualcomm elements of privilege escalation and information disclosure.
In addition, Google Pixel devices that have identified 20 additional vulnerabilities according to the Pixel Security Bulletin will receive the update.

Google patches critical vulnerabilities in its browsers every week
Updated versions of Chrome are available for Windows, Mac and Linux that address a total of four vulnerabilities.
- CVE-2021-37977: deals with a garbage collection issue that may lead to arbitrary code execution on the target system;
- CVE-2021-37978: Blink Browser Buffer Overflow;
- CVE-2021-37979: WebRTC streaming mechanism;
- CVE-2021-37980: Inappropriate implementation in Sandbox.
Details of the vulnerabilities are not disclosed by Google until most users install a security update. In this connection, the search giant recommends updating as soon as possible. According to the company, the facts of use in targeted attacks have not yet been identified
Tools

Scrummage: ultimate OSINT and threat hunting framework.
GitOops: Attacking and defending CI/CD pipelines.
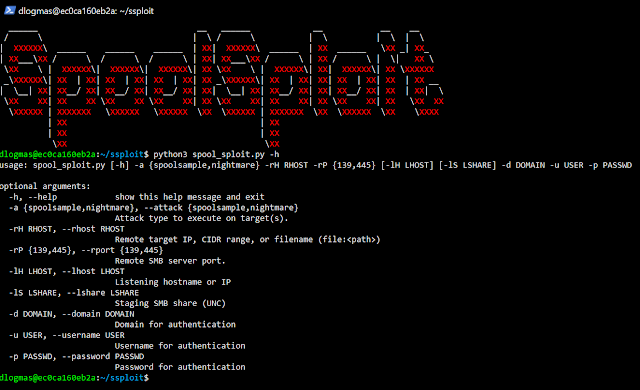
SpoolSploit: A collection of Windows print spooler exploits containerized with other utilities for practical exploitation.
News

Source code and financial data of the Twitch streaming service have been leaked
The published 125GB archive contains the source code for the Twitch app for desktop devices, mobile platforms and game consoles, internal SDKs, and proprietary penetration testing tools. In addition to this, the archive contains information on payments to streamers of the platform since 2019. The leaked archive includes:
- Twitch Contributor Payouts for the last 3 years;
- Twitch source code with a history of commits from the very beginning of development;
- Source code for Twitch clients for mobile, desktop, and video games;
- Code associated with proprietary SDKs and AWS back-end services used by Twitch;
- An unreleased competitor to Steam from Amazon Game Studios, codenamed Vapor;
- Data on other Twitch properties such as IGDB and CurseForge;
- Twitch Internal Security Tools;
- Encrypted passwords of some users.

ESPecter bootkit
Cybersecurity researchers from ESET have published details of a previously undocumented Unified Extensible Firmware Interface (UEFI) bootkit ESPecter, which was used by cybercriminals under Windows back in 2012 by modifying a legitimate Windows Boot Manager binary. The malware allows to bypass the forced use of Windows driver signatures and at the expense of downloading a malicious unsigned driver.

Kaspersky Lab publishes a report on ransomware operating in the CIS
Researchers reported on the main ransomware that most actively attack organizations in the CIS in 2021. The report contains a brief overview of the malware and its technical features.
Research
TRAM: Advancing Research into Automated TTP Identification in Threat Reports. https://medium.com/mitre-engenuity/tram-advancing-research-into-automated-ttp-identification-in-threat-reports-2d868fecc791
Windows 11 Security Book. A high-level overview of the security posture for the new Windows OS. https://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RWMyFE
S0cm0nkey's Reference Guide - OSINT and Passive Recon: https://s0cm0nkey.gitbook.io/s0cm0nkeys-security-reference-guide/osint-passive-recon
Threat hunting in large datasets by clustering security events: https://blog.talosintelligence.com/2021/10/threat-hunting-in-large-datasets-by.html
Hunting for Lateral Movement: Local Accounts: https://posts.bluraven.io/hunting-for-lateral-movement-local-accounts-bc08742f3d83
Feedback and Vulners docs
al-movement-local-accounts-bc08742f3d83](https://posts.bluraven.io/hunting-for-lateral-movement-local-accounts-bc08742f3d83)
Feedback and Vulners docs
