Monthly Vulners Review with TOP vulnerabilities and news

This month, Vulners published new functionality for auditing Linux CentOS via Errata plugin (like RHEL). After that, we updated our new docs and wrote current monthly review of the top news. This month was full of zero-day, critical patches (not for everyone) and many different hacks with information security news.
- Vulnerabilities: Mobile processors, Realtek, Cisco, WordPress and scanning for VMware (patch it faster)
- Tools: DFIR and Kubernetes (new trends)
- News: Meat attack, new WhatsApp policies and etc.;
- Research: Attack and defensive articles.
Really short feedback -> here
Vulnerabilities

Check Point reported that it was discovered CVE-2020-11292 vulnerability in Qualcomm's Mobile Station Modem (MSM) chipset.
CVE-2020-11292 allows an attacker to inject malicious code into MSM, making it invisible to any application and OS-level security mechanisms. In the future, an attacker can gain access to the history of calls and SMS correspondence, as well as intercept voice traffic.
Vdoo discovered critical vulnerabilities
Vdoo identified the critical vulnerabilities CVE-2020-27301 and CVE-2020-27302. Their operation allows you to get elevated privileges on the device, completely seize control over the module and increase the privileges in the OS.
Realtek RTL8710C Wi-Fi is at the heart of Ameba's Arduino-compatible programmable platform. It is equipped with peripheral interfaces to create various IoT applications for agriculture, automotive, etc.

Less than a month after Cisco closed the critical CVE-2021-1479 RCE vulnerability in SD-WAN vManage, fresh ones are on the way.
Cisco released updates that closed several vulnerabilities in SD-WAN vManage that allowed an unauthenticated attacker to remotely execute code (RCE). The company also fixed two other vulnerabilities in HyperFlex HX that allowed unauthenticated remote command execution.

A critical RCE vulnerability was discovered in the popular plugin Fancy Product Designer. This plugin for WordPress, WooCommerce and Shopify is a visual product configurator and is installed on over 17,000 sites.
Using a vulnerability in Fancy Product Designer, hackers can bypass built-in checks that block the download of malicious files and deploy PHP executables to sites where the plugin is installed. Ultimately, this will allow criminals to completely seize control of the resource.

Skylight Cyber published details of 13 vulnerabilities in Nagios software. Nagios is an open-source IT infrastructure tool analogous to SolarWinds Network Performance Monitor (NPM) that offers monitoring and alerting services for servers, network cards, applications, and services.
Exploitation of vulnerabilities allows an attacker to compromise IT networks without operator intervention. The critical CVE-2020-28648 vulnerability is related to incorrect input validation in Nagios XI's Auto-Discovery component, which researchers used as a starting point to launch a chain of five exploits.

Critical RCE in VMware vCenter Server
Last week we wrote about critical vulnerabilities in VMware vCenter Server CVE-2021-21985. It was reported this week that attackers are actively scanning servers on the Internet in search of this vulnerability.
At least 14,858 vCenter servers were found reachable over the internet, according to Bad Packets and Binary Edge.
It is highly recommended to update your own servers (even if they are on the internal network!). According to recent research, it wormed its way into exposed VMware vCenter servers by abusing the same security weakness to boost the malware's infection propagation capabilities.
Tools

IPED is an open source software that can be used to process and analyze digital evidence, often seized at crime scenes by law enforcement or in a corporate investigation by private examiners.
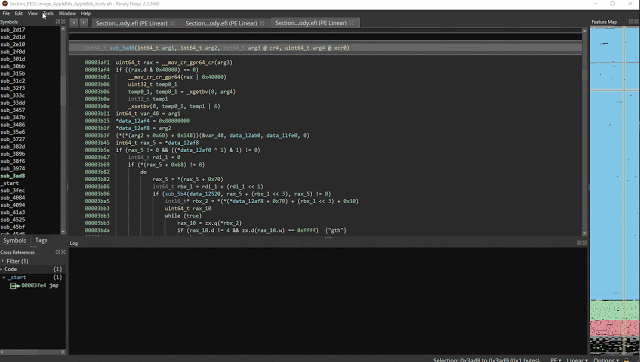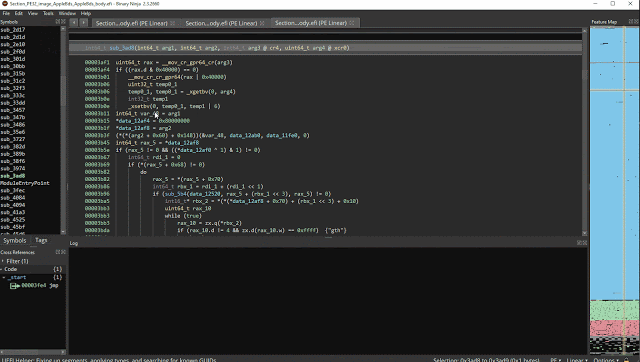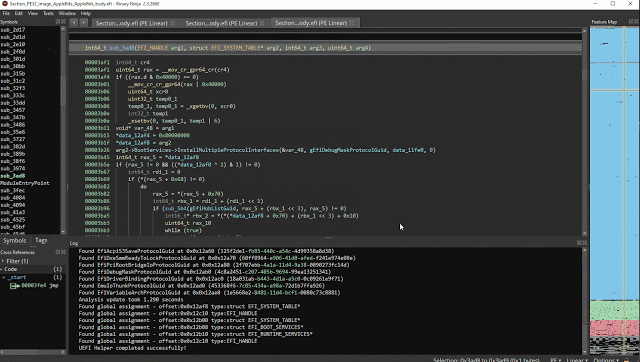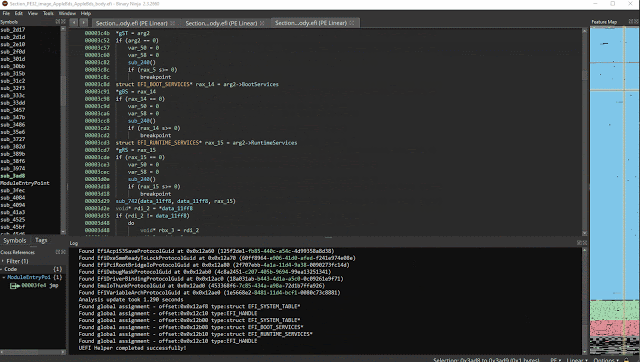
bn-uefi-helper: Helper plugin for analyzing UEFI firmware.

Penglab is a ready-to-install setup on Google Colab for cracking hashes with an incredible power, really useful for CTFs.
It installs by default :
- Hashcat
- John
- Hydra
- SSH (with ngrok)

DFIR-O365RC: PowerShell module for Office 365 and Azure AD log collection

KubeArmor is a container-aware runtime security enforcement system that restricts the behavior (such as process execution, file access, networking operation, and resource utilization) of containers at the system level.

Red Kube is a collection of kubectl commands written to evaluate the security posture of Kubernetes clusters from the attacker’s perspective.
News

The American government is concerned about the possible consequences of a ransomware attack on the world's largest meat processor JBS and, as a result, a malfunction in the work of JBS USA IT systems, on the American meat market.
JBS Australia director Brent Eastwood confirmed the information about the cyberattack, as a result of which the organization was forced to suspend production. He was unable to predict how long the slaughterhouses and other facilities of the company would be closed.
Later, a statement appeared on the official website of the FBI, according to which the REvil group was behind the attack on JBS. The Bureau urges every organization that has been the victim of a cyberattack to immediately notify the FBI through one of the offices. According to the latest reports, JBS is now ready to rebuild its operations after the incident.

For several months in a row, WhatsApp stated that users who do not adopt the new rules by May 15 will eventually not be able to use all the messenger's features, but now plans have changed. Facebook, which owns WhatsApp, has officially stated that users who do not accept the updated policy will not see any limited functionality on WhatsApp.

NSA monitored European politicians through a telecommunications center in Denmark
The media reported that the Danish intelligence services provided the US NSA with access to the country's telecommunications center, allowing the National Security Agency to monitor the reports of European politicians. Denmark is the geographic center of telecommunications in Europe, giving Danish intelligence services access to a huge amount of traffic.
Owner of telegram channel: Freedom Fox has been arrested by Russian authorities. https://securityaffairs.co/wordpress/118464/cyber-crime/pavel-sitnikov-arrested.html
Research
Attacking Active Directory https://zer1t0.gitlab.io/posts/attacking_ad
From Binary Patch to Proof-of-concept: a VMware ESXi vmxnet3 Case Study https://zerodayengineering.com/research/vmware-esxi-vmxnet3-from-patch-to-poc.html
m0chan Blog - Info Sec, CTF & Hacking https://m0chan.github.io/2019/07/31/How-To-Attack-Kerberos-101.html
Exploiting custom protocol handlers for cross-browser tracking in Tor, Safari, Chrome and Firefox https://fingerprintjs.com/blog/external-protocol-flooding
PE Reflection: The King is Dead, Long Live the King
https://bruteratel.com/research/feature-update/2021/06/01/PE-Reflection-Long-Live-The-King
Really short feedback -> here
ve the King
https://bruteratel.com/research/feature-update/2021/06/01/PE-Reflection-Long-Live-The-King
Really short feedback -> here
