Install relevant security updates for CentOS with Errata plugin from Vulners
The Vulners team presents an additional auditing method for Linux CentOS distributions of versions 7 and 8 via errata for centos. Errata is a yum-plugin-security for installing only security updates/patching individual vulnerabilities on Linux systems. What is the point of installing ALL UPDATES every time? Let's tell you more.

Free CentOS errata from Vulners
Introduction
Errata for CentOS is the same yum-plugin-security as for RHEL. Why is it important to be able to install separate advisories or patch individual vulnerabilities? When installing all full updates, it is possible that some update may affect the application/service/something important on your server. The problems of any critical system are problems for the business: money, reputation, any risks, etc.
Initially, the Vulners team began to develop such a solution, because we ourselves need it due to the presence of Linux CentOS in our infrastructure. We performed a research and did not find free or high-quality working solutions. The team then proceeded to implement their own and today we are sharing this with the information security community.
Not commerce just sec to sec!
How it works?
Ok, it sounds cool, but how to try it? The benefit of using errata for CentOS is that you can start doing it right now by following a few steps (e.g. via ansible):
1. Get free license and create API key
2. Add a repository to your system:
cat /etc/yum.repos.d/vulners-errata.repo
[vulners-errata]
name=Vulners Errata
baseurl=https://<your apikey here>@vulners.com/errata/centos/$releasever
enabled=1
gpgcheck=0
3. After step 1, you can start using the following useful commands:
[root@c9e98ae2ac45 /]# yum updateinfo list
Failed to set locale, defaulting to C.UTF-8
Last metadata expiration check: 0:01:09 ago on Wed Jun 2 14:48:13 2021.
RHSA-2021:1679 Important/Sec. bash-4.4.19-14.el8.x86_64
RHSA-2021:1582 Moderate/Sec. cpio-2.12-10.el8.x86_64
RHSA-2021:1610 Moderate/Sec. curl-7.61.1-18.el8.x86_64
RHSA-2020:5634 Important/Sec. dracut-049-95.git20200804.el8_3.4.x86_64
RHSA-2020:5634 Important/Sec. dracut-network-049-95.git20200804.el8_3.4.x86_64
[root@c9e98ae2ac45 /]# yum list-sec cves
Failed to set locale, defaulting to C.UTF-8
Last metadata expiration check: 0:01:35 ago on Wed Jun 2 14:48:13 2021.
CVE-2019-18276 Important/Sec. bash-4.4.19-14.el8.x86_64
CVE-2019-14866 Moderate/Sec. cpio-2.12-10.el8.x86_64
CVE-2020-8231 Moderate/Sec. curl-7.61.1-18.el8.x86_64
4. Start installing only the updates you need:
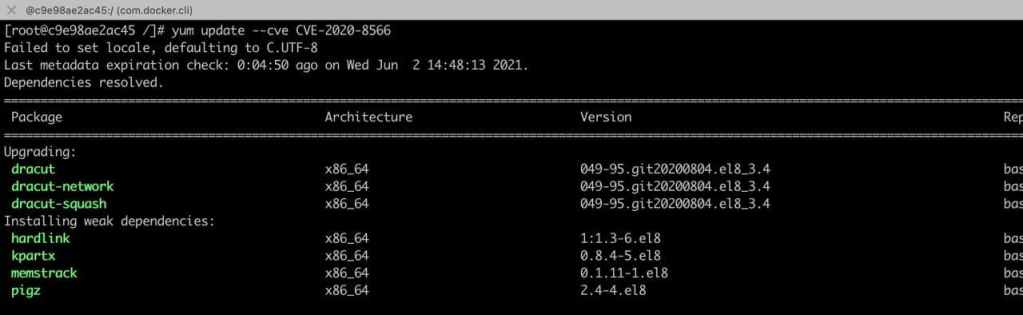
[root @ c9e98ae2ac45 /] # yum update-minimal --cve CVE-2020-8566
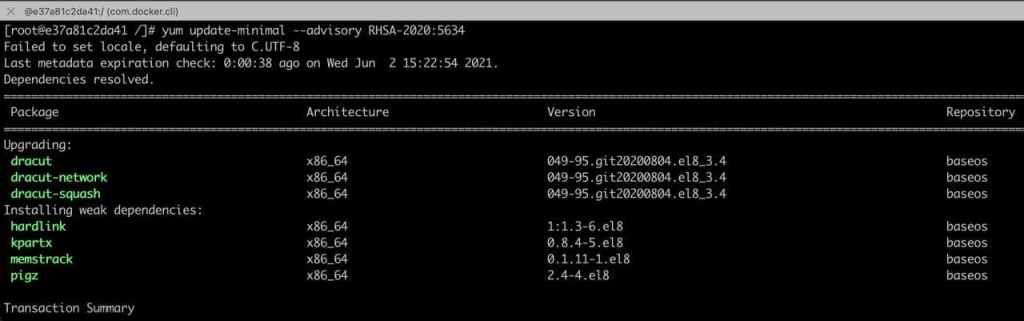
[root @ c9e98ae2ac45 /] # yum update-minimal --advisory RHSA-2020: 5634
5*. It's possible to add installation of updates directly to /etc/cron.d/security-update:
<required time format> root /usr/bin/yum -y update-minimal --security
Now you can give up your expensive vulnerability assessment solution. And you are ready to use Vulners. Enjoy it!
Conclusion
As mentioned above, we did some research on suitable solutions. According to results, we couldn't find a solution to resolve our tasks. But since we did it for ourselves, why not share it with the community?
From a technical point of view it is as follows. Vulners does a search every 2 hours for new advisories suitable for CentOS. Then it prepares them properly on its side and returns to the user a fresh list of advisories / CVEs.
1 server - 1 API request - update. If you are quite advanced, you can implement a cache of such requests from your side and save on API limits. Judging by our experience, the standard update cycle is 1 week. In this mode, the free API limit is enough to maintain security audit for most companies.
Send us your questions and ideas for such solutions. Check our docs and subscribe on updates!
