More ransomware and more zero-days every week

Not much big news this week. Mainly ransomware attacks, which are actively expanding and the main vulnerabilities of the past week.
- Vulnerabilities: New PoC / Exploit for iis, car vulnerabilities and few zero-days for Android;
- Tools: Pentest tools;
- News: Ransomware activity, more info about February incident and FBI alert;
- Research: Have you ever try to dump svchost? AD attacks, hunting for persistence via Exchange and detection;
Vulnerabilities

Proof of Concept published for the CVE-2021-31166 vulnerability in Windows IIS. Vulnerability is associated with memory corruption in the HTTP protocol stack.
CVE-2021-31166 is critical: CVSSv3 scores 9.8. At the same time, there are a number of factors that decrease the risk. For example, only the latest versions of Windows Server 2016 (2004 and 20H2) and Windows 10 (2004 and 20H2) are vulnerable.

MBUX vulnerabilities
Tencent Security Keen Lab found five vulnerabilities in the Mercedes-Benz User Experience (MBUX) infotainment system. Four out of five vulnerabilities are critical and allow remote code execution. In addition, the specialists were able to identify a number of problems in the head unit of the car: a heap overflow vulnerability, the ability to configure a remote shell and a vulnerability in the Linux kernel that allows you to elevate privileges.

Android 0-day vulnerabilities
Google has warned of four zero-day vulnerabilities CVE-2021-1905, CVE-2021-1906, CVE-2021-28663, and CVE-2021-28664 in Android. Issues affect Qualcomm Graphics Module and Arm Mali GPU Driver.
- CVE-2021-1905: Contained in the Qualcomm graphics component and is associated with incorrect handling of memory mapping of several processes at the same time;
- CVE-2021-1906: Related to incorrect handling of address deregistration, which could result in a failure to allocate addresses for the new GPU;
- CVE-2021-28663: Allows a non-privileged user to perform GPU memory operations to gain superuser or data access;
- CVE-2021-28664: Allows an unprivileged user to gain read / write access to persistent memory and thereby escalate privileges or DoS.
Successful exploitation of vulnerabilities allows an attacker to gain access to the device and take control over it.
Tools
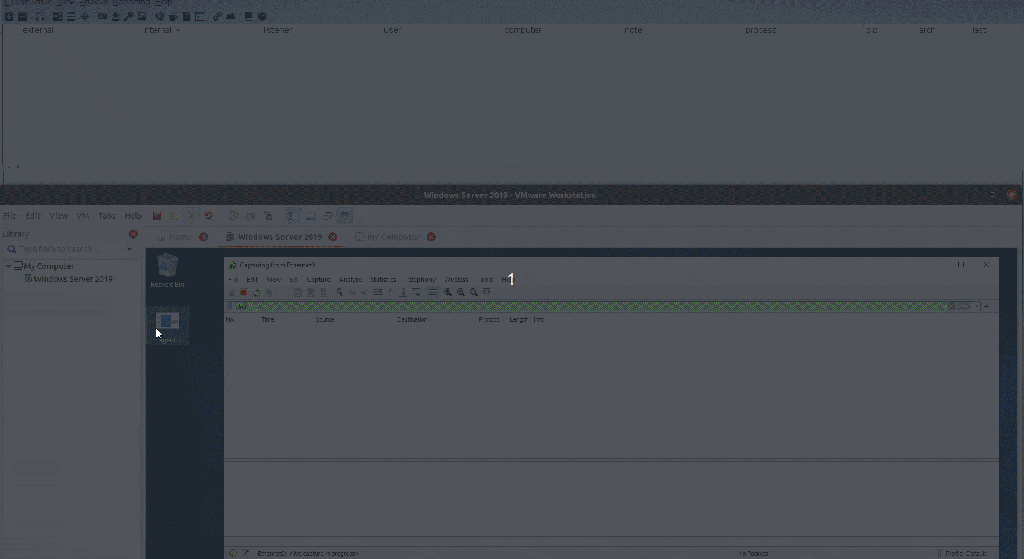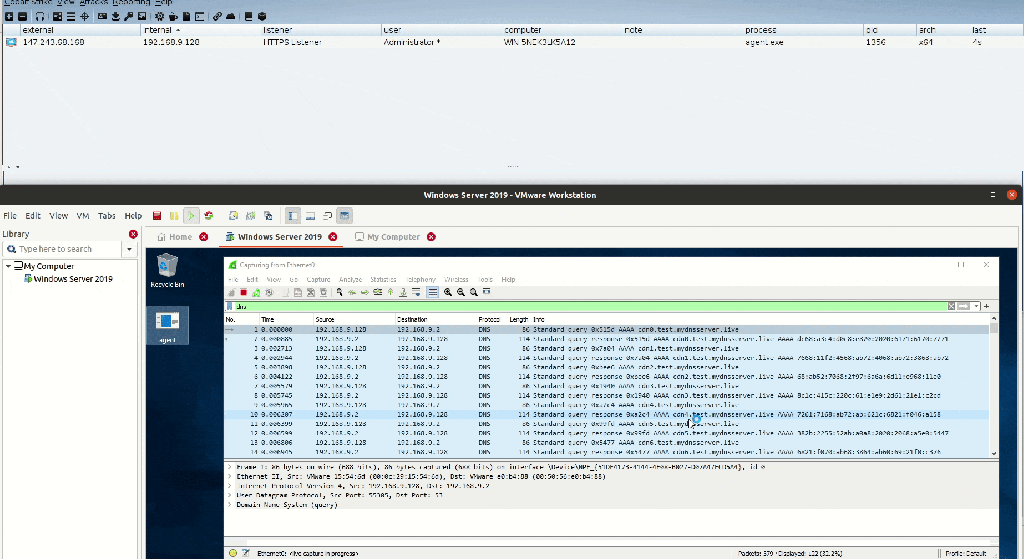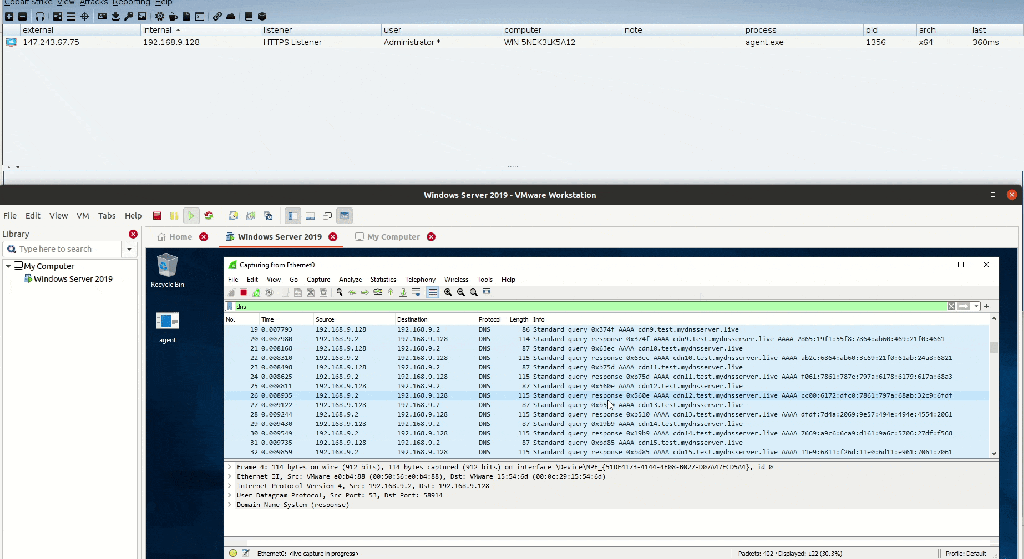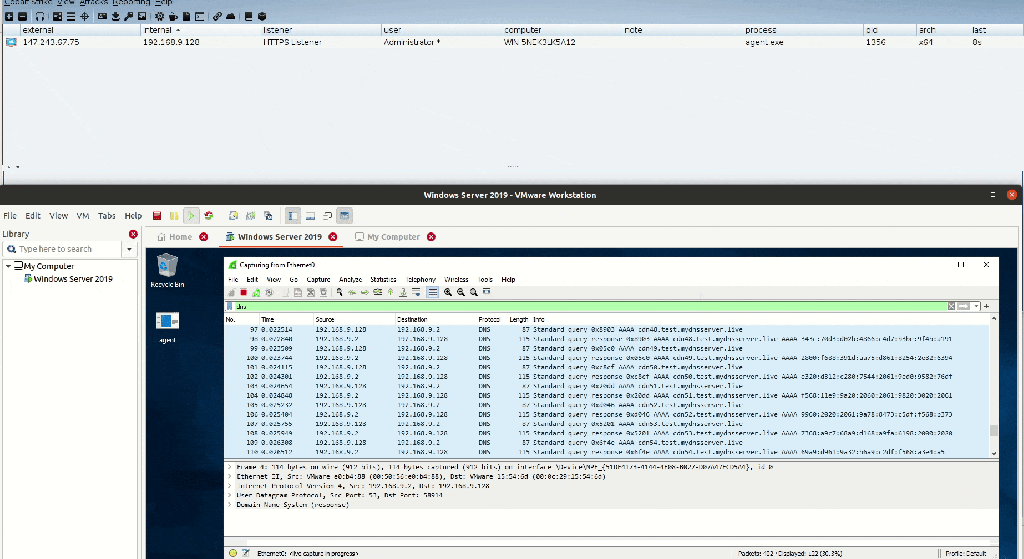
DNSStager is is an open-source tool used to help Pentesters / RedTeamers to hide their payload in DNS and resolve it based on multiple DNS records such as IPv6 and TXT and then Inject it into memory and run it for you.
GraphQLmap is a scripting engine to interact with a graphql endpoint for pentesting purposes.

IPED is an open source software that can be used to process and analyze digital evidence, often seized at crime scenes by law enforcement or in a corporate investigation by private examiners.
News

The French multinational insurance company AXA has been attacked using the ransomware Avaddon. The attack came after the company announced its refusal to sell cyber insurance programs in France on May 9 this year, which reimburse customers for the ransom payments.
The hackers themselves announced the incident on their website, reporting the theft of more than 3 TB of confidential information from the company's Asian divisions, as well as unleashing massive DDoS attacks on its sites. AXA took the incident very seriously and connected a special working group with the involvement of external experts to the investigation, informed the supervisory authorities and partners.

Florida Water Utilities
Dragos released interim results of an investigation into an incident in February, during which an attacker gained access to the control system of a water treatment facility in the city of Oldsmar, in the US state of Florida. The researchers found that the website of a Florida-based wastewater treatment contractor had hosted malicious code in a seemingly typical "watering hole" attack. Apparently, the targets were water utilities, and on the day of the hack, the Oldsmar Water Treatment Facility was hacked into the infected site.
The attacker used a hole in one of the WordPress plugins to host code that collected fingerprints from visitors to the site, including information about the OS and processor, browser and used layouts, video card, and so on. Dragos believe that the malicious code is designed to collect browser fingerprints for further use in the Tofsee botnet in order to more successfully imitate real users. Whether the hacking of the contractor's website is related to the hacking of the water treatment system in Oldsmare is not clear.

Ransomware Conti, best known for a series of high-profile incidents including the recent attack on the Irish Health Authority (HSE) systems, attacked more than 400 organizations around the world last year, including health and emergency organizations, the Federal Bureau said in a warning US investigations.
Research
In some cases, RDP passwords are stored in the server's memory in plaintext in svhost.exe. Thus, by sdamping svchost, an attacker can theoretically pull credentials from there and use them to further propagate to the target network.
How to Exploit Active Directory ACL Attack Paths Through LDAP Relaying Attacks: https://www.praetorian.com/blog/how-to-exploit-active-directory-acl-attack-paths-through-ldap-relaying-attacks
Difference between Microsoft Azure Security Center and Azure Sentinel: https://www.taliun.com/difference-between-microsoft-azure-security-center-and-azure-sentinel
Hunting for persistence via Microsoft Exchange Server or Outlook: https://speakerdeck.com/heirhabarov/hunting-for-persistence-via-microsoft-exchange-server-or-outlook
Sysmon configuration repository for everybody to customize: https://github.com/olafhartong/sysmon-modular
Feedback
r-or-outlook)
Sysmon configuration repository for everybody to customize: https://github.com/olafhartong/sysmon-modular
