Typical zero-days and new malware features, what else is required?

All of the vulnerabilities mentioned in the post are critical, some of them zero-day vulnerabilities that need to be urgently updated in their own products. For the second week, our news consists of malwares that are hijacking new targets (like Apple contractor) and actively evacuating.
- Vulnerabilities: zero-day in PulseSecure, SonicWall and Chrome, but some of them have been fixed;
- Tools: Research tools, mostly useful for DFIR;
- News: C&C via Telegram, ransomware for Apple contractor and new botnet for your Exchange;
- Research: Typically research.
Feedback -> here
Vulnerabilities

CISA USA issued an emergency directive after reports of Chinese hackers exploiting a zero-day vulnerability in Pulse Connect Secure gateways CVE-2021-22893.
To control Pulse Secure devices, hackers exploited known CVE-2019-11510, CVE-2020-8243, CVE-2020-8260 and CVE-2021-22893, identified the day before, and then planted malware (SLOWPULSE, RADIALPULSE, THINBLOOD, ATRIUM, PACEMAKER, SLIGHTPULSE and PULSECHECK), which allowed them to leave backdoors. Hacker activity continued to be recorded until March 2021.
Together with FireEye, Pulse Secure VPN developed and released a temporary patch package and a special scanner for Pulse Security Integrity Checker Tool servers to detect possible unauthorized interference. The full patch will be available in May 2021.

SonicWall ES fixed three zero-day vulnerabilities
FireEye has warned that hackers are using three zero-day vulnerabilities in SonicWall products to break into corporate networks and install backdoors. The vulnerabilities affect SonicWall Email Security, an email security solution that companies use in the cloud or on-premises to scan email traffic.
- CVE-2021-20021: bypass authentication, create administrator account;
- CVE-2021-20023: reading local files;
- CVE-2021-20022: modification of local files or download of web-shells used as backdoors.
SonicWall patched all three vulnerabilities on April 13, 2021, but did not provide any information about them at the time. Only on April 20 did the company report that they were already being exploited in real attacks.

Google recommends that customers update their Chrome browser to version 90.0.4430.85 as soon as possible. The vulnerability directly affects the JavaScript V8 engine and is the fourth zero-day vulnerability in Chrome discovered in 2021. The data typing bug, numbered CVE-2021-21224, was reported by Jose Martinez, an IS expert at VerSprite.
Tools

Cypheroth: Automated, extensible toolset that runs cypher queries against Bloodhound’s Neo4j backend and saves output to spreadsheets.

Posta - Cross-document Messaging Security Research Tool.
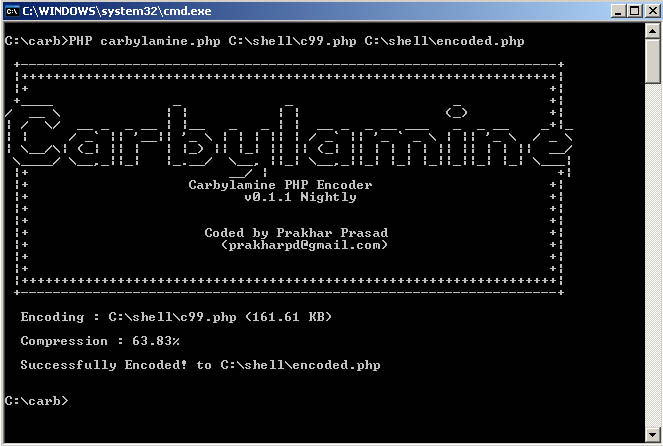
Carbylamine PHP Encoder is a PHP Encoder to 'Obfuscate/Encode' PHP Files.
News

RAT ToxicEye
Check Point revealed that attackers are increasingly using Telegram as a ready-made C&C system in their attacks. In particular, the messenger is used in conjunction with the new RAT ToxicEye Trojan.
First, attackers create an account and a special bot in the messenger, link it to the Trojan, which, in turn, is spread via spam mail. When the victim opens the malicious attachment in the mailing, the Trojan is deployed to the host, triggering a series of exploits.
Once installed on the victim's computer, ToxicEye connects it to the attacker's C&C. As a result, attackers are able to control the infected computer using commands sent via Telegram.

REvil managed to hack Apple contractor Quanta Computer, a Taiwanese company. Quanta Computer is one of the few companies that assemble Apple products based on schematics and designs provided by them. These schematics and designs were made available to attackers as a result of the hack.
The REvil operators have published a message on their website demanding to pay $50 million for the stolen data by April 27. Otherwise, the criminals are threatening to put dozens of stolen schematics and blueprints in the public domain. At the moment 21 screenshots of MacBook blueprints are published on the website of criminals. The criminals promise to publish new data every day until the ransom is paid.
As patches for ProxyLogon problems are still not installed by everyone, vulnerable Microsoft Exchange servers continue to be attacked by attackers. Now researchers have discovered the Prometei botnet, which mines Monero cryptocurrency on vulnerable machines.
Research
Named Pipe Pass-the-Hash: https://s3cur3th1ssh1t.github.io/Named-Pipe-PTH
Azure Sentinel Query Creator Notebook
MS External Email Warning Bypass: https://whynotsecurity.com/blog/external-email-warning-bypass
Telegram bug bounties: XSS, privacy issues, official bot exploitation and more.
Malware training vol 1: https://github.com/hasherezade/malware_training_vol1
Feedback -> here
cial-bot-exploitation-and-more-5277fa78435)
Malware training vol 1: https://github.com/hasherezade/malware_training_vol1
Feedback -> here
