Too burning/hot weekly digest 🔥

Upgrade your Exchange servers, now! Some attackers/pentesters/red teamers/researchers have already converted Proxylogon PoCs into first versions of RCEs to exploit these vulnerabilities.
Microsoft has released another big and important update this week. Apart from that, there were many small but important updates with zero-day vulnerabilities. + There were various attacks, malware, and data centers burning.
- Vulnerabilities: Microsoft monthly update, Apple, Chrome and F5 emergency updates!;
- Tools: Analyze your repo, reporting tool (markdown to pdf) and pentest tools;
- News: New malware, ransomware attack and a burning datacenter. How was your week?;
- Research: Red teaming and Blue teaming.
Feedback -> here
Vulnerabilities

Microsoft released another Tuesday security update
A total of 89 vulnerabilities in the company's products were fixed, of which 14 were critical. Among them were two zero-day vulnerabilities, one of which was under attack.
Five vulnerabilities were exploited by hackers in the wild - four headliners in Microsoft Exchange exploited by Chinese APT Hafnium (in fact, the vulnerabilities were fixed with an unscheduled patch on March 2) + CVE-2021-26411 vulnerability in Edge and Internet Explorer. This vulnerability allows an attacker to execute remote code execution (RCE) when a user visits a malicious site.
- CVE-2021-26855: SSRF vulnerability that allowed sending arbitrary HTTP requests and bypassing authentication;
- CVE-2021-26857: Unified Messaging deserialization issue. Using this bug gave a hacker the ability to run code with SYSTEM privileges on the Exchange server. For the exploit to work properly, administrator rights or another vulnerability were required;
- CVE-2021-26858: Allows writing arbitrary files (after authentication in Exchange);
- CVE-2021-27065: Another arbitrary file writing vulnerability (after authentication with Exchange).
Along with fixes for zero-day bugs, experts prepared fixes for three vulnerabilities in Microsoft Exchange that were not used by hackers:
- CVE-2021-26412, CVE-2021-26854 and CVE-2021-27078: Microsoft Exchange issues related to remote code execution.
Another zero-day vulnerability patched this week was CVE-2021-27077 and is related to privilege escalation in Windows Win32k.
Bottom line: there are many vulnerabilities and need to be updated as soon as possible!

Apple has released an urgent, unscheduled update that fixes a dangerous vulnerability through which attackers can execute malicious code. The bug is known to threaten billions of devices, as updates are available for iOS, macOS and watchOS systems, as well as the Safari browser.
The bug is contained in the WebKit engine used by Safari and can lead to remote code execution (RCE) when visiting a malicious page.
Researchers assigned the vulnerability an identifier CVE-2021-1844, information about it was shared by Google Threat Analysis Group and Microsoft Browser Vulnerability Research.

F5 published a bulletin on several critical vulnerabilities. Researchers have published details on four critical vulnerabilities, two high-critical vulnerabilities, and one medium-critical vulnerability. Specialists recommend promptly starting work on fixing all the vulnerabilities found.

Google has released an update to Chrome 89.0.4389.90 that fixes five vulnerabilities, including CVE-2021-21193, a problem already being exploited by attackers (0-day). No details have been revealed yet, only that the vulnerability is caused by accessing an already freed memory location in the Blink JavaScript engine.
Tools
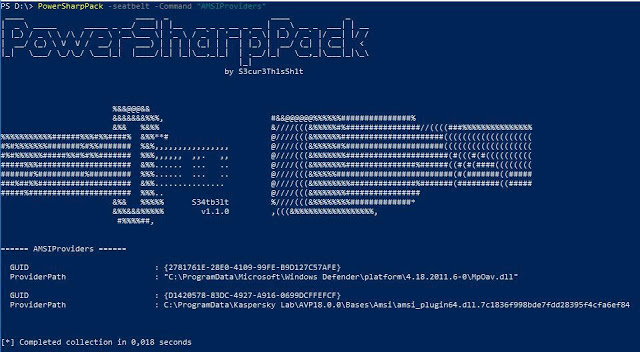
PowerSharpPack: usefull offensive CSharp Projects.
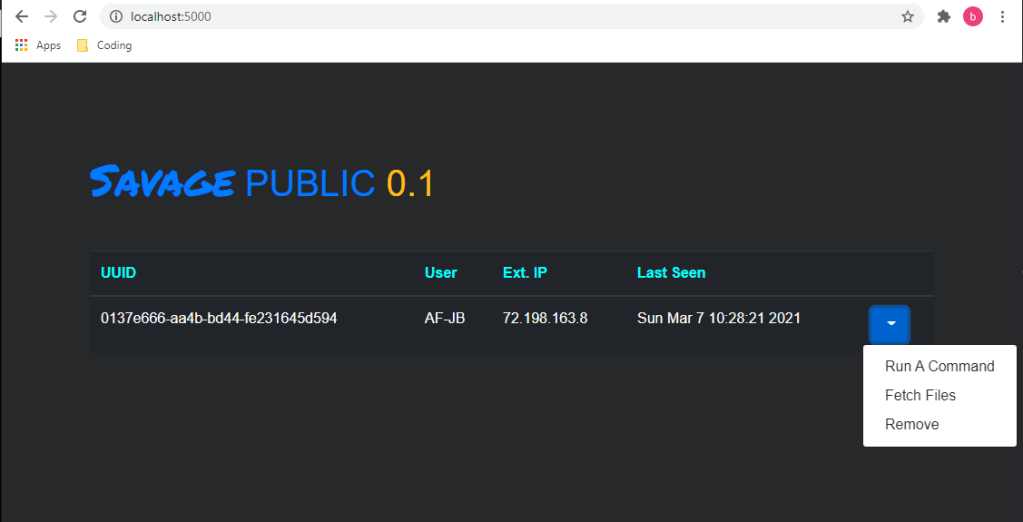
NEW! Web Interface for Post-Exploit Tool Savage, Utilizing Dropbox API!

Gitls - Enumerate Git Repository URL From List Of URL / User / Org
WriteHat is a reporting tool which removes Microsoft Word from the reporting process. Markdown->HTML->PDF. Created by penetration testers, for penetration testers. Written in Django (Python 3).
News

Apps that spread AlienBot and MRAT malware detected on Google Play
Malware has been found in the Google Play Store again. This time, Check Point experts found the Clast82 dropper, which was involved in the distribution of the AlienBot banker and MRAT trojan as part of nine apps.

The new malware is called RedXOR because it uses the XOR encryption algorithm to encrypt network data. The backdoor is able to collect system information: MAC address, username, distribution and kernel version, perform file operations, execute commands with system privileges, run arbitrary shell commands, and even remotely update. Basically, the use of the new malware was seen in attacks from Chinese groups.
Ransomware operator Ryuk successfully attacked the resources of the Spanish State Employment Agency (SEPE). As a result of the attack, the official SEPE portal does not function, services for citizens, social services and employment services are not provided. In total, the attack affected more than 700 SEPE branches throughout the country.
One of the OVH data centers in Strasbourg burned down. OVH is the largest hosting provider in Europe. In addition to VPN.AC, clients such as the well-known intelligence company Bad Packets, the crypto solution VeraCrypt, the game maker Rust and many others have suffered. Moreover, Rust confirmed that they completely lost all data on their servers.
Research
Active Directory exploitation cheet sheet and command reference: https://casvancooten.com/posts/2020/11/windows-active-directory-exploitation-cheat-sheet-and-command-reference
Complete Read Teaming EBook: https://dmcxblue.gitbook.io/red-team-notes-2-0
Bazar Drops the Anchor - The DFIR Report: https://thedfirreport.com/2021/03/08/bazar-drops-the-anchor
A Basic Timeline of the Exchange Mass-Hack: https://krebsonsecurity.com/2021/03/a-basic-timeline-of-the-exchange-mass-hack
Microsoft Exchange server exploitation: how to detect, mitigate, and stay calm: https://redcanary.com/blog/microsoft-exchange-attacks
Really short feedback -> here
xploitation: how to detect, mitigate, and stay calm: https://redcanary.com/blog/microsoft-exchange-attacks
Really short feedback -> here
