Tuesday patch with Kerberos, bunch of vulnerabilities and security breaches
Lots of buzz about the FireEye hack this week, but most hack news is often a consequence of the lack of a vulnerability management process. Also this week a lot of vulnerabilities were found in Internet protocols and even Steam games. In our digests we try to show the most significant and interesting news for the last time.
- Vulnerabilities: Microsoft Patches, OpenSSL, D-link routers and even Games;
- Tools: xCyclopedia and offensive;
- News: Hacking famous (and not) companies and new malware in all browsers;
- Research: FireEye breach, turn off Windows Defender and others.
Really short feedback -> here
Vulnerabilities
Microsoft released the latest security patch for 2020, addressing at least 58 vulnerabilities in Microsoft Windows, PowerPoint, Microsoft Outlook, Microsoft Exchange, Microsoft Kerberos, Azure DevOps, Azure Sphere, and other solutions.
The vulnerabilities of remote code execution in Microsoft Windows NTFS CVE-2020-17096, Microsoft Exchange, Microsoft SharePoint, Microsoft Excel, Microsoft PowerPoint CVE-2020-17124, Microsoft Visual Studio CVE-2020-17148, CVE-2020-17156, CVE- 2020-17150.
It also resolved Kerberos security bypass issue CVE-2020-16996 that could allow an attacker to gain unauthorized access to an application, and provided a workaround for a DNS spoofing vulnerability in Windows DNS Resolver that could be cached by DNS Forwarder or DNS Resolver.
Also, details of the CVE-2020-17049 vulnerability, which was patched with the December update, were revealed this week. Jake Karnes published details and an exploit for it, the attack was named Kerberos Bronze Bit (not Ticket) because it is based on flipping just one bit. It is a variation of the older and more widely known Golden Ticket and Silver Ticket attacks against Kerberos. The difference between Golden Ticket, Silver Ticket and Bronze Bit is the part of the Kerberos protocol the attacker exploits. Author's research and workflow: https://blog.netspi.com/cve-2020-17049-kerberos-bronze-bit-overview
https://vulners.com/rapid7blog/RAPID7BLOG:99D9180FBF3F900ADB0CDC5EF79EC080

Critical vulnerabilities were discovered in the network library that powers Valve's online games, the exploitation of which could allow attackers to remotely crash video games and even take control of affected third-party game servers to execute arbitrary code.
Researchers discovered four vulnerabilities in the Game Networking Sockets library, which combines UDP and TCP protocol functions and supports encryption:
The affected games include CS:GO, Dota, Left 4 Dead and others.
https://vulners.com/threatpost/THREATPOST:278458B8B7AD1BAD24FB2C2C5F0B1441

The OpenSSL Project has fixed a dangerous DoS vulnerability CVE-2020-1971, associated with null pointer dereferencing (in ASN.1 structure handler), which a remote attacker can use to invoke a denial-of-service state using TS_RESP_verify_response and TS_RESP_verify_token API functions.
Three vulnerabilities were found in D-link routers:
- CVE-2020-25757 allows high privilege (root) commands to be executed without authentication;
- CVE-2020-25758 and CVE-2020-25759 allow commands to be executed by any authenticated user.
Two of these vulnerabilities are in the process of being fixed, patches will be released in mid-December, and another one depends on router functionality and cannot be fixed in devices that have already been released.
Affected models: DSR-150, DSR-250, DSR-500 и DSR-1000AC.
https://vulners.com/threatpost/THREATPOST:C7799EF097814CAB36419E678D6DD441
Forescout found 33 vulnerabilities in open-source Internet protocols that make millions of embedded devices open to cyberattacks, including information interception, denial of service and taking full control.
Vulnerable stacks are used in 158 vendors' products. These are communication modules, office equipment, IoT, etc. The researchers warn that this is the minimum number of vulnerable vendors, because not all products specify information about the use of a specific implementation of the TCP/IP stack. Tens and hundreds of millions of different devices may be vulnerable.
Some of the vulnerabilities discovered are elementary programming errors such as the absence of input validation mechanisms that prevent the system from accepting problem values or operations. Many of the vulnerabilities are memory corruption vulnerabilities, hence the name Amnesia: 33. With their help an attacker can read or add data to the device's memory, extract information, disable the device or take control of it. Several vulnerabilities are also related to Internet connectivity mechanisms such as the way the stack handles DNS records and IP addressing, such as IPv4 and IPv6.
https://vulners.com/thn/THN:812B2C8E4446362B541FFE932E10CC78
Tools

xCyclopedia: A project that "attempts to document all executable binaries (and eventually scripts) that reside on a typical operating system."
https://github.com/strontic/xcyclopedia

**Sak1To-Shell
**Multi-threaded c2 server and reverse TCP shell client written in pure C (Windows).
https://vulners.com/kitploit/KITPLOIT:3056304803628582479
holehe
It allows you to check if the mail is used on different sites like Twitter, Instagram and will retrieve information on sites with the forgotten password function.
https://github.com/megadose/holehe
News

The American company FireEye, one of the world's leading information security vendors, was recently attacked by an extremely sophisticated hacker group. The company was attacked by a highly professional hacker group with a high level of resistance to cyber forensics. The attack was tailored specifically for a specific target.
https://vulners.com/fireeye/FIREEYE:CE15ADEFFA503A24136DFE24B327638F

"Foxconn is the world's largest electronics manufacturer, with revenues of $172,000,000,000 in 2019 and more than 800,000 employees worldwide. Foxconn subsidiaries include Sharp Corporation, Innolux, FIH Mobile and Belkin."
Ransomware DoppelPaymer successfully hacked the world's largest electronics manufacturer Foxconn. On Nov. 29, hackers hacked into Foxconn's plant in Mexico. The DoppelPaymer leak website then published some of the stolen data. This leak includes only business documents and reports, and does not contain any financial information or personal information about employees.
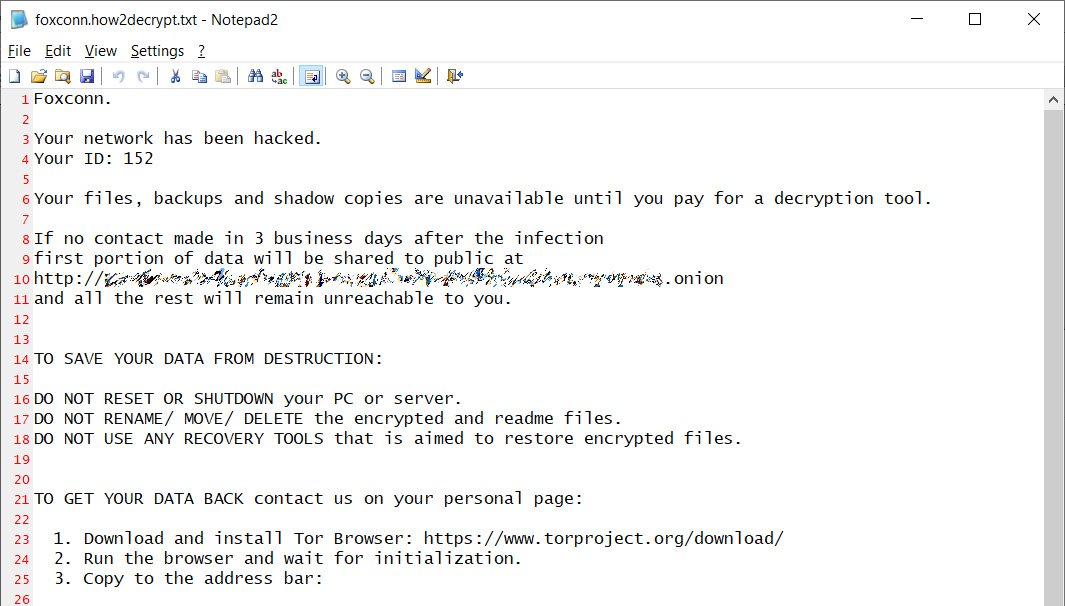
As you can see from the text of the note that was left on the servers, the attackers are demanding a ransom from the company in the amount of 1804.0955 BTC, that is, about $ 34 million at the current exchange rate.
https://vulners.com/threatpost/THREATPOST:9AD0EC0A8E38B604F59658CE3410B97A
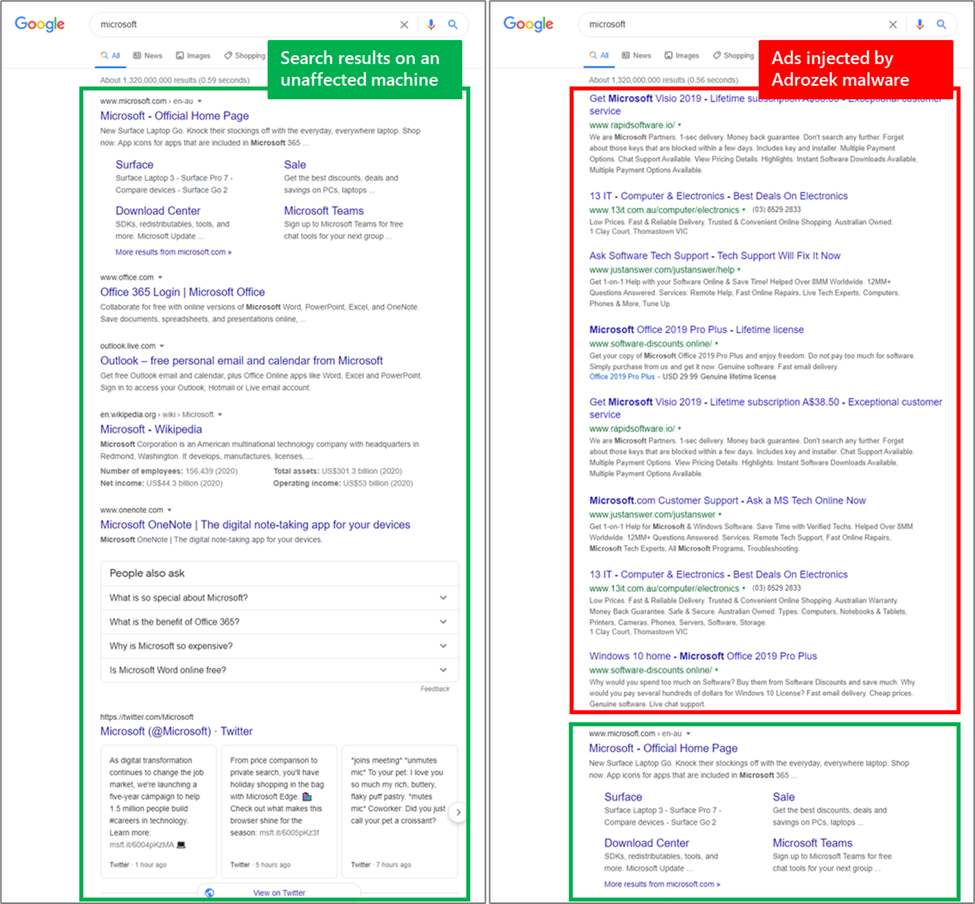
Microsoft revealed the Adrozek malware that has compromised more than 30,000 browsers. Microsoft has warned of a new malware that infects users' devices and changes their browser settings to place ads in search results.
Currently, malware is spread using classic drive-by attacks. That is, users are redirected from legitimate sites to the domains of attackers, where they are tricked into installing malware, which then ensures itself a permanent presence in the system by registering in the registry.
Microsoft reports that Adrozek operations are extremely complex, especially when it comes to distribution infrastructure. Since May 2020, the company has tracked 159 domains that hosted Adrozek installers. Each of the domains hosted an average of 17,300 dynamically generated URLs, and each URL hosted more than 15,300 dynamically generated Adrozek installers.
https://vulners.com/mmpc/MMPC:47717210762AA39C4D630CBD1381F500

For weeks unknowns disrupted the PickPoint checkpoint network. Due to the attack, many checkpoints opened the doors of the cells, and the items stored in them were available to anyone.
The company explained that the PickPoint team managed to save most of the orders from the hacker attack. Within 20 minutes from the moment of hack the developers deactivated about 80% of 2732 infected postal terminals, so the doors of the cells did not open. By December, 7th the company managed to restore work of the infected outlets for 95 %. In addition, new software is being installed on the postal terminals.
Research
Everyone knows that FireEye has posted various methods of detecting their utilities, but few have seen the report with the analysis of the FireEye red team tools. Picus Labs analyzed all the 60 stolen FireEye red team tools and revealed the Tactics, Techniques and Procedures (TTPs) used by them. Read the blog post for a detailed analysis and recommendations. (According to the analysis, 43% of them are based on open-source tools)
The why, what, and how of threat research and detection. Detection engineering and research methodology from Red Canary. Worth the read. https://redcanary.com/blog/threat-research-questions
More and more companies are outsourcing their infrastructure. Such solutions must necessarily include quite a bit of cybersecurity. An example of a set of such solutions can be the guys from Ntiva.
Velociraptor and OSQuery: https://medium.com/velociraptor-ir/velociraptor-and-osquery-2a4306dd23c
Defender Control - Defender Control is a free software utility we’ve come across in various intrusions to turn off Windows Defender: https://thedfirreport.com/2020/12/13/defender-control
Really short feedback -> here
ss in various intrusions to turn off Windows Defender: https://thedfirreport.com/2020/12/13/defender-control
Really short feedback -> here
