Monthly review without Microsoft, a lot of cool tools, Flipper project and new malware
More and more new news about bypassing fixed vulnerabilities appear. And it's great! After all, it means that there are more people who care and they continue to research the problems after they have been fixed.
- Vulnerabilities: Cisco and Apache are trying very hard to fix their vulnerabilities, but there are still too many…;
- Tools: All new popular tools and updates of old, well known tools;
- News: New tojans/malware and nice ending to the project 'Flipper Zero' on kickstarter;
- Research: The author cannot silently pass by interesting research.
Enjoy!
Feedback -> here
Vulnerabilities
We already wrote about these vulnerabilities in our digest, and they were even fixed by the monthly Microsoft update (May).
But security researchers at yf at BlackHat 2020 have demonstrated a workaround for the patch Microsoft released to fix CVE-2020-1048 vulnerability in Windows Print Services, the exploitation of which allows attackers to execute malicious code with elevated privileges. A workaround for this fixed vulnerability has been classified as a new issue CVE-2020-1337
Check previous matrials from digest :)
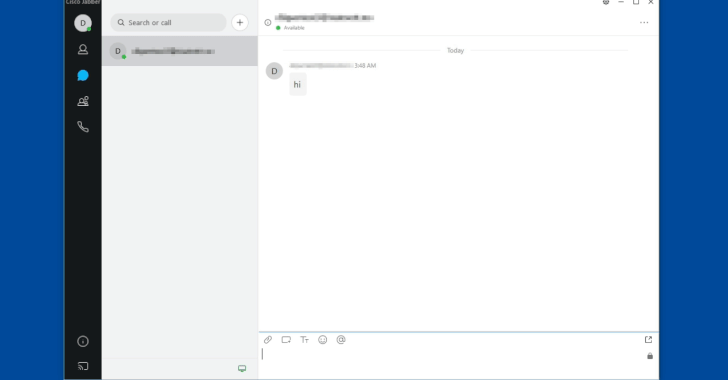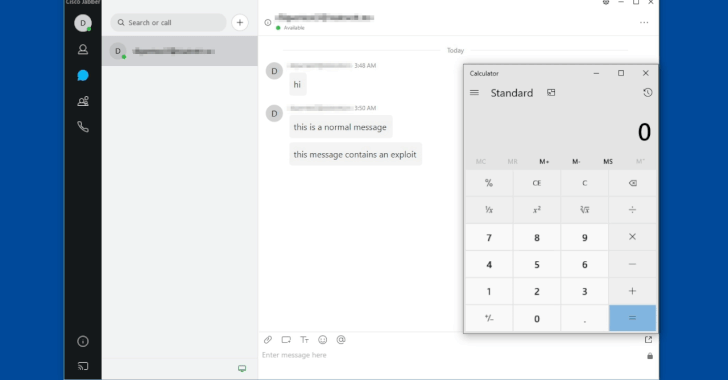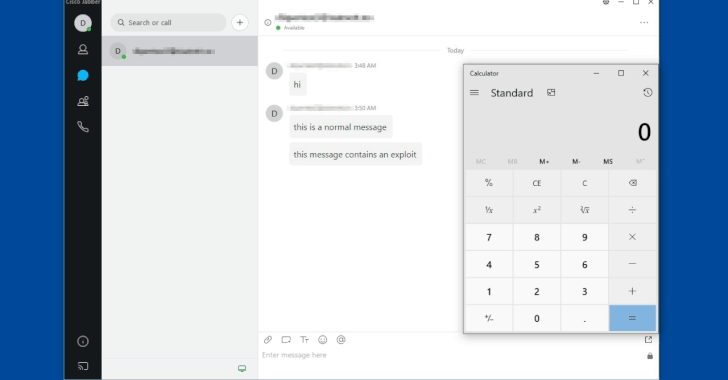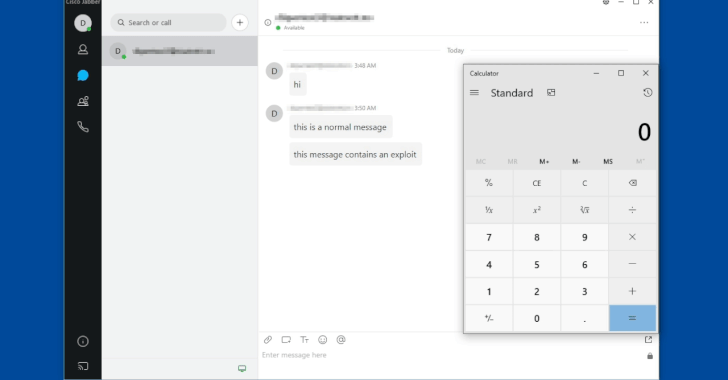
Cisco released a security update that fixes four vulnerabilities in Jabber's fast messaging system, including a critical issue that allows arbitrary code execution. CVE-2020-3495 vulnerability affects Jabber Windows client versions with XMPP messaging service activated.
Using this vulnerability, attackers can create a worm that can automatically spread malware to Jabber users without the need for any action on their part. The main problem is that the application does not check incoming HTML messages, instead passing them through an unreliable XSS filter. The remaining 3 vulnerabilities: CVE-2020-3430, CVE-2020-3498, CVE-2020-3537 can be exploited for command injection and disclosure.
https://vulners.com/thn/THN:4BE868261372143E25379A8422C42E17

This month, Cisco discovered and patched a high-severity 0-day vulnerability in its Cisco IOS XR operating system, which is used on carrier-grade switches.
The error lies in the implementation of processing DVMRP protocol packets and can lead to a denial of service by exhausting the memory of the attacked device. In this case, the attacker does not need to be authenticated. The vulnerability, designated CVE-2020-3566, affects all Cisco devices running any Cisco IOS XR release if multicast routing is enabled.
https://vulners.com/threatpost/THREATPOST:A5D4FD6C2281AE395B821A8D0EB5736D

The Agency for Cyber Security and Infrastructure Security (CISA) has issued a warning for two bugs that are tracked as CVE-2019-0230 and CVE-2019-0233. This affected Apache Struts versions 2.0.0-2.5.20. According to the Apache Struts security group, the fix includes an upgrade to Struts 2.5.22.
- https://vulners.com/atlassian/ATLASSIAN:CONFSERVER-60189
- https://vulners.com/threatpost/THREATPOST:0DD2AEA1738F9B6612B1C845F3BC949F
**3 new Apache vulnerabilities.
**Google Researcher Reported 3 Flaws in Apache Web Server Software. Apache Foundation developers fixed three dangerous vulnerabilities within the Apache web server. Vulnerabilities could lead to arbitrary code execution, failure or denial of service:
https://vulners.com/thn/THN:5CBAB87993B908AA48688CDD57262B40

TeamViewer Desktop for Windows
Vulnerability CVE 2020-13699 relates to the way TeamViewer handles URI headers, which allows an attacker to force the software to send an NTLM authentication request to the attacker's system. An attacker can use the TeamViewer URI scheme to force an application installed on the victim's system to initiate a connection to the attacker's SMB network folder. Thus, it can leak the system name and NTLMv2 hashed version of the password and log into the victim's system.
https://vulners.com/thn/THN:03DCDBB188020C1EAB4A67AFB2448826
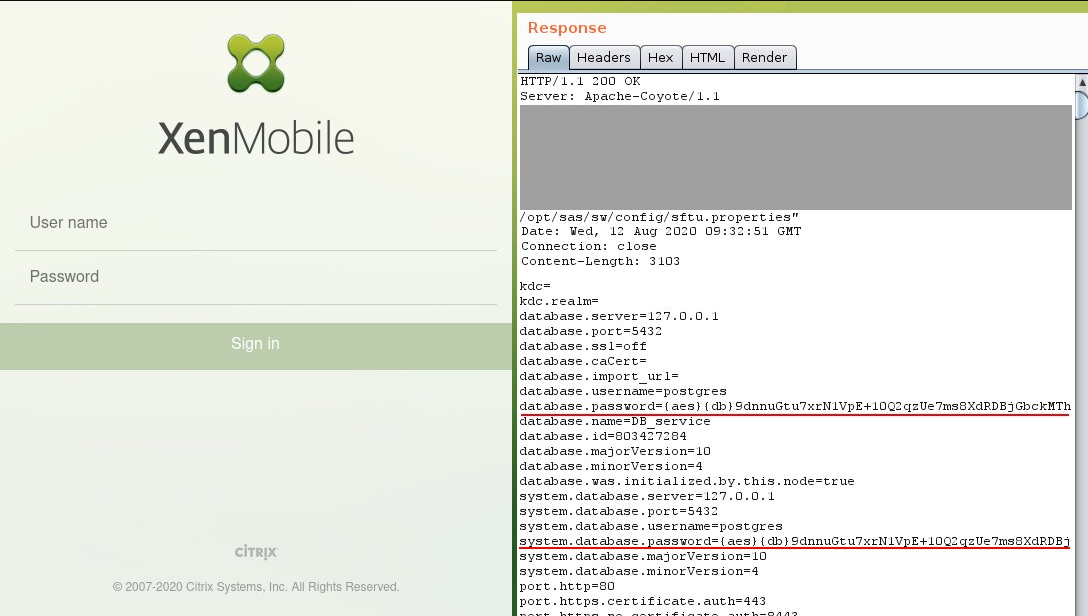
Citrix engineers released patches for Citrix Endpoint Management (XenMobile Serve) in August. Vulnerabilities are critical for XenMobile versions 10.12 to RP2, 10.11 to RP4, 10.10 to RP6 and all versions up to 10.9 RP5. Vulnerability CVE-2020-8209 was discovered by Positive Technologies specialist Andrey Medov, which belongs to the Path Traversal class and is associated with insufficient input data validation.
Versions 10.9.x should be updated immediately (preferably to the newest 10.12 RP3), as some problems can be exploited remotely and without authentication
https://vulners.com/threatpost/THREATPOST:163B67EFAB31CDAD34D25B9194438851
The vulnerability is not always accompanied by a detailed research, but this is exactly the case here. The author describes in detail how he managed to detect it and according to his words this path allowed him to get into Active Directory through the brute force. Let's read it?
https://honoki.net/2020/08/10/cve-2020-11518-how-i-bruteforced-my-way-into-your-active-directory
Tools
PyWSUS
The main goal of this tool is to be a standalone implementation of a legitimate WSUS server which sends malicious responses to clients.
- https://github.com/GoSecure/pywsus
- https://www.gosecure.net/blog/2020/09/03/wsus-attacks-part-1-introducing-pywsus

ReconSpider
It is most Advanced Open Source Intelligence (OSINT) Framework for scanning IP Address, Emails, Websites, Organizations and find out information from different sources.
https://vulners.com/kitploit/KITPLOIT:4092831499812504329

**Pyre-Check
**Pyre is a performant type checker for Python compliant with PEP 484 . Pyre can analyze codebases with millions of lines of code incrementally – providing instantaneous feedback to developers as they write code.
https://vulners.com/kitploit/KITPLOIT:6694889785828925271
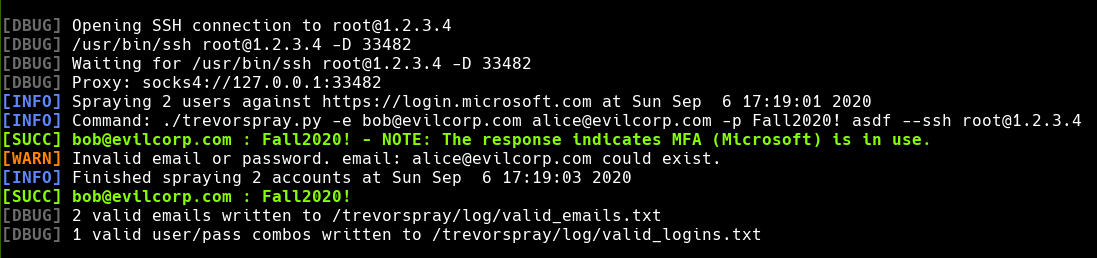
TREVORspray
Microsoft is getting better and better about blocking password spraying attacks against O365. A featureful Python O365 sprayer based on MSOLSpray which uses the Microsoft Graph API.
https://github.com/blacklanternsecurity/TREVORspray
Penglab
Penglab is a ready-to-install setup on Google Colab for cracking passwords with an incredible power, really useful for CTFs.
News

Indian authorities banned 118 apps in the country that "secretly steal and transfer user data outside India, thereby undermining its sovereignty and national security." Apps include Baidu, WeChat, AliPay, PUBG, etc. All apps seem to be related to Chinese developers. Earlier in late June, India blocked 59 Chinese apps, which included TikTok, WeChat and Weibo.
https://vulners.com/threatpost/THREATPOST:696DA10F577DA8594B43B305F85D0503

The US Department of Homeland Security's Cyber and Infrastructure Security Agency (DHS CISA) issued Binding Operational Directive 20-01, according to which, by March 2021, US federal authorities must develop and implement vulnerability disclosure policies (VDPs).
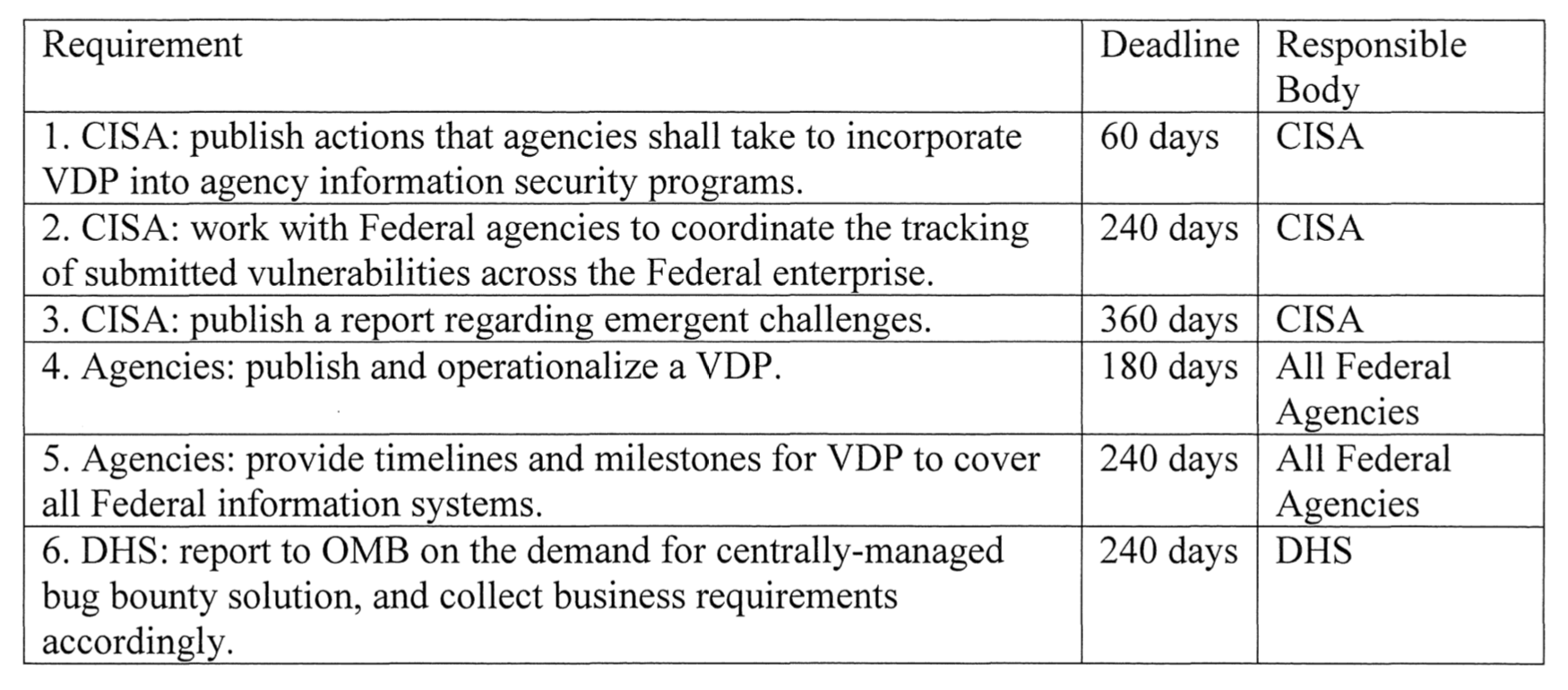
Over the next 60 days, CISA intends to publish guidance on how to implement VDP in agency information security programs. Within 180 days, government agencies must develop or update existing vulnerability disclosure policies to reflect the new requirements.
https://vulners.com/threatpost/THREATPOST:289CFB5DB5452FE519F8F625904586CF
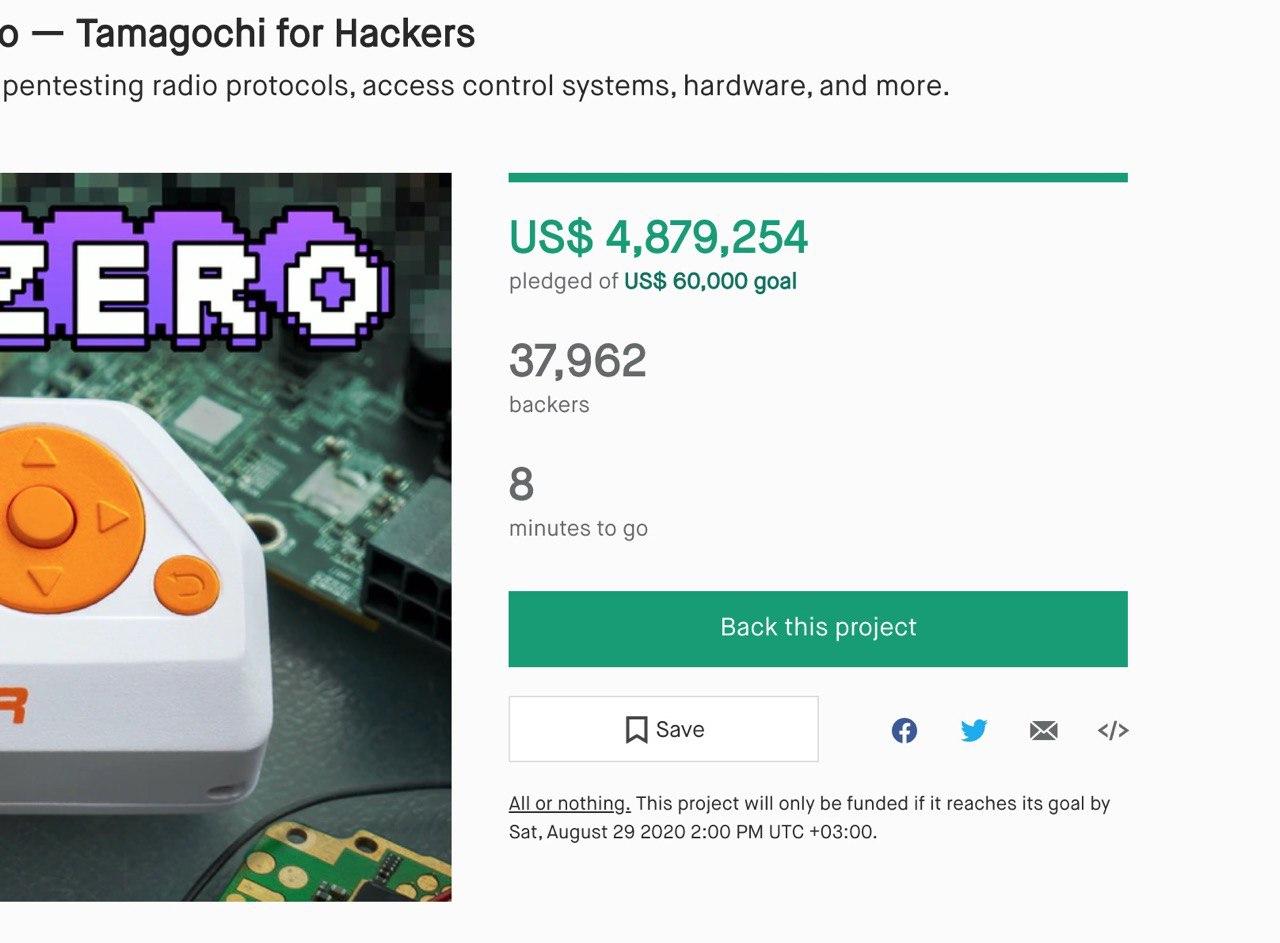
"Tamagotchi for Hackers" raised almost $ 5 million
As a result, Flipper Zero raised $ 4,882,784. 37,987 people invested in the project on the crowdfunding platform. Initially, when entering Kickstarter, the task was to raise the amount of $ 60 thousand, which was collected in 8 minutes. A day after the placement, the project had more than $ 500 thousand in fees, and a day and a half after it collected $ 1 million.
According to the developers, as many hardware tools as possible for testing penetration into electronic systems are combined in one device.
The next version: http://flipperzero.one

Affable Kraut discovered that web skimmer operators began to use Telegram channels to extract data stolen from users. The name MageCart was given to one hack group, which was the first to introduce web skimmers (malicious JavaScript) on the pages of online stores to steal bank card data.
Malwarebytes researcher Jerome Segura was also interested in this script, and after studying it, he said that the author of this web skimmer used a simple Base64 for the bot ID, Telegram channel and API requests.
https://vulners.com/threatpost/THREATPOST:20CE12B47663EDBA45713BF8CBF640D4

The US Cybersecurity Agency (CISA), in conjunction with the FBI, yesterday released a report on new malware used by North Korean APT Lazarus. The malware is a RAT (remote access tool), BLINDINGCAN. It is designed to collect information from an infected host and exfiltrate it, and also has the functionality to clean up traces of its presence in the attacked system.
BLINDINGCAN's distribution mechanism is spear phishing; the targets of the attack were employees of the defense and aerospace sectors. North Korean hackers pretended to be recruiters of large corporations, and during the interview they sent files with a malicious attachment.
One of the common phrases used was the "dream job" sentence. Therefore, ClearSky called this North Korean hacker campaign Operation Dream Job.
https://vulners.com/thn/THN:888D339CA6E31146BD406F95BB7E214B
FritzFrog is written in Go and has been brute-forcing SSH servers since early 2020. The main goal of FritzFrog is to mine Monero cryptocurrency. To do this, an XMRig miner is deployed on infected systems, connected to the web.xmrpool.eu pool via port 5555.
If the brute-force attack on the SSH server is successful, the malware leaves almost no traces on the attacked system, since it runs in memory and is classified as fileless malware. After starting FritzFrog, the malware is unpacked under the names ifconfig and NGINX and listens on port 1234 waiting for commands.
Typically, the very first command it receives connects the victim machine to the P2P botnet. If some processes on the server take up CPU resources, malware can kill them so that the miner can work more efficiently.
https://vulners.com/thn/THN:98E58D3336F3AFB87D3267D52432A919
Research
Non-standard and modern malware that uses various modern tactics and techniques. PowerShell payload used DNS over HTTPS to request TXT record of a doppelganger domain which looked like a DKIM signature which after decoding actually contained C2 IPs. Hiding in Plain Sight: https://blog.huntresslabs.com/hiding-in-plain-sight-part-2-dfec817c036f
Simple bugs with complex exploits: https://www.elttam.com/blog/simple-bugs-with-complex-exploits
Windows Group policy client service - Insecure file operations causing escalation of privilege (no patch available): https://docs.google.com/document/d/1sRrftambp4gz4koVX1Qs1l1ODDFTp1eUd6j6NvmCt1U
Windows Group policy client service - Insecure file operations causing escalation of privilege (no patch available): https://docs.google.com/document/d/1sRrftambp4gz4koVX1Qs1l1ODDFTp1eUd6j6NvmCt1U
New Trick to Detect Lateral Movement via Network File Shares: https://blog.menasec.net/2020/08/new-trick-to-detect-lateral-movement.html
Offensive security officialy announces it launch of dedicated lab play grounds with previous oscp retired machines added occasionally and upto 3hrs of free acess to all: https://www.offensive-security.com/labs/individual
Deployment of virtual machines for research, digital forensics and more is becoming popular:
https://0xbanana.com/blog/one-click-forensics-lab-in-the-cloud
Feedback -> here
