
Meow Attack: A Reminder for Organizations to Identify and Secure Their Databases
Thousands of unsecured internet-facing databases have fallen prey to the “Meow” attack and have been permanently destroyed. Meow attacks replace the original index with a newly created one with the suffix “-meow”. With no ransomware demands or any other explanatory note, the attackers seem to have executed these massive attacks just for the sake of fun. According to Bob Diachenko, the security researcher who first found out about this attack, “…the malicious actors behind the attacks do it just for fun, because they can, and because it is really simple to do”.
The question that arises is, what makes such attacks so simple to execute? As evident in all the Meow attacks that have taken place so far, databases that were wiped out could be modified without credentials, or had some loosely configured settings. The attacks didn't impact the paid or premium versions, or the databases on cloud. It was impacting only the free, community versions. According to security analysts and researchers, this attack appears to be a bot, that seeks and destroys unsecured databases that run on a variety of software, including ElasticSearch, MongoDB, Cassandra, Hadoop, Jenkins, and others. The bot subsequently overwrites all data, effectively destroying the contents of the database.
The Meow Attack, and a similar but less malicious one that followed it shortly after, have come into light as a wake-up call to enterprises all over the world not to be complacent about their database assets. One must ensure continuous monitoring of the environment and have a robust process that flags anomalies before an intrusion occurs.
Qualys Policy Compliance enables you to detect databases in your IT environment that are not appropriately configured. Qualys PC’s rich content library, complete with its methodically devised controls, provides the best-possible security solution in the industry.
Automatically Discover Security Soft Spots in Your Database Assets
Databases are the most valuable assets in an organization and the most vulnerable target for attacks at the same time. To be able to protect the confidentiality, integrity, and availability of data against attacks such Meow, organizations must have a structure that’s woven into their system.
Qualys helps you have a standardized process in place to ensure a comprehensive security hygiene in your environment. Qualys’ extensive policy library includes out-of-the-box as well as custom controls and a broad coverage of hardening benchmarks published by Center for Internet Security (CIS). Organizations can quickly assess their databases against the established benchmarks and ensure that all critical security misconfigurations and loopholes are detected, so that they can be addressed before it’s too late.
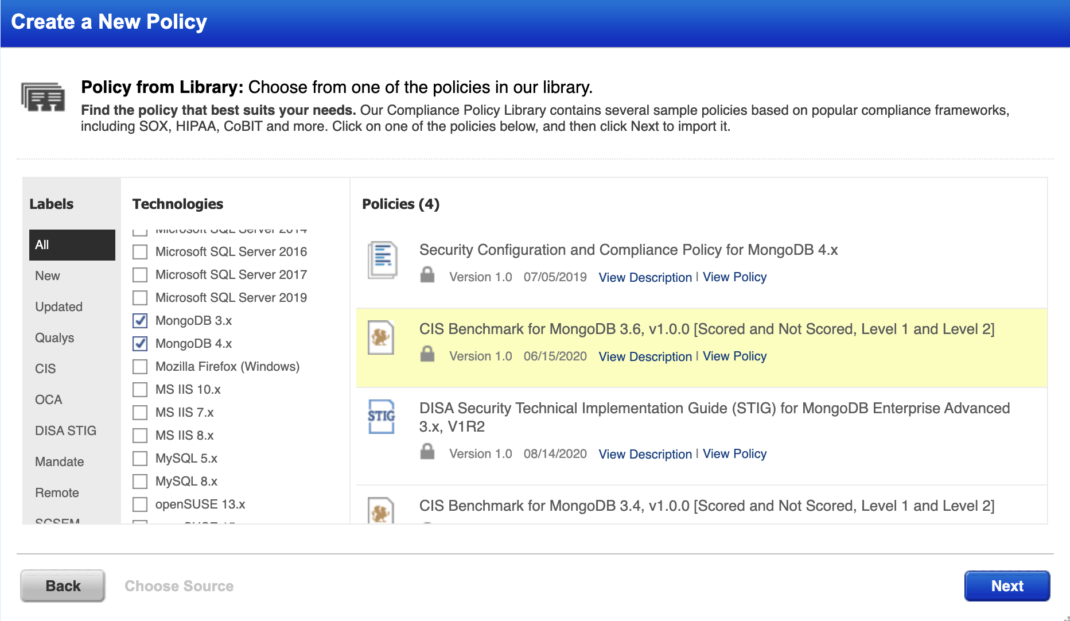
Weak settings in a database could involve loosely configured security parameters or even using default settings, which are highly capable of baring the security cover of the entire IT infrastructure. As we’ve seen in the recent Meow attacks, attackers can gain control of the unsecured and unauthenticated database instances, causing security breaches and data loss.
Qualys PC helps you to negate such loopholes and obtain a clearer picture, which is supported by robust data. Qualys PC’s specially crafted policies and controls for database instances help you conduct thorough security evaluations and take necessary action to mitigate risks.
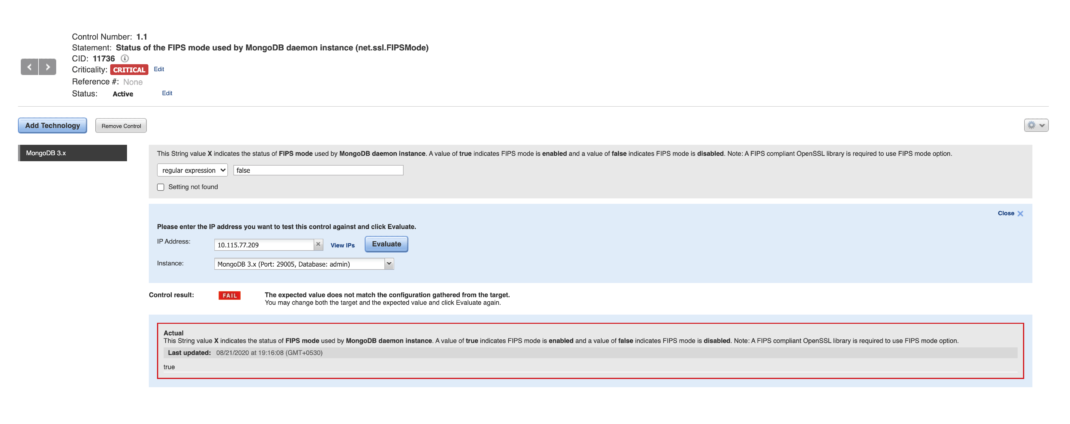
Single-Pane-of-Glass View
To have a precise understanding and an in-depth visibility into your assets, it is crucial that the data collected from various endpoints is thoroughly analyzed and presented to display a holistic view of the entire environment. The true essence of the Qualys Dashboard is the capability to present data in a way that enables you to take quick and precise business-critical decisions. Based on the compliance evaluations carried out on your target databases, the Qualys PC dashboard allows you to gain a comprehensive understanding of your database assets and their current compliance posture.
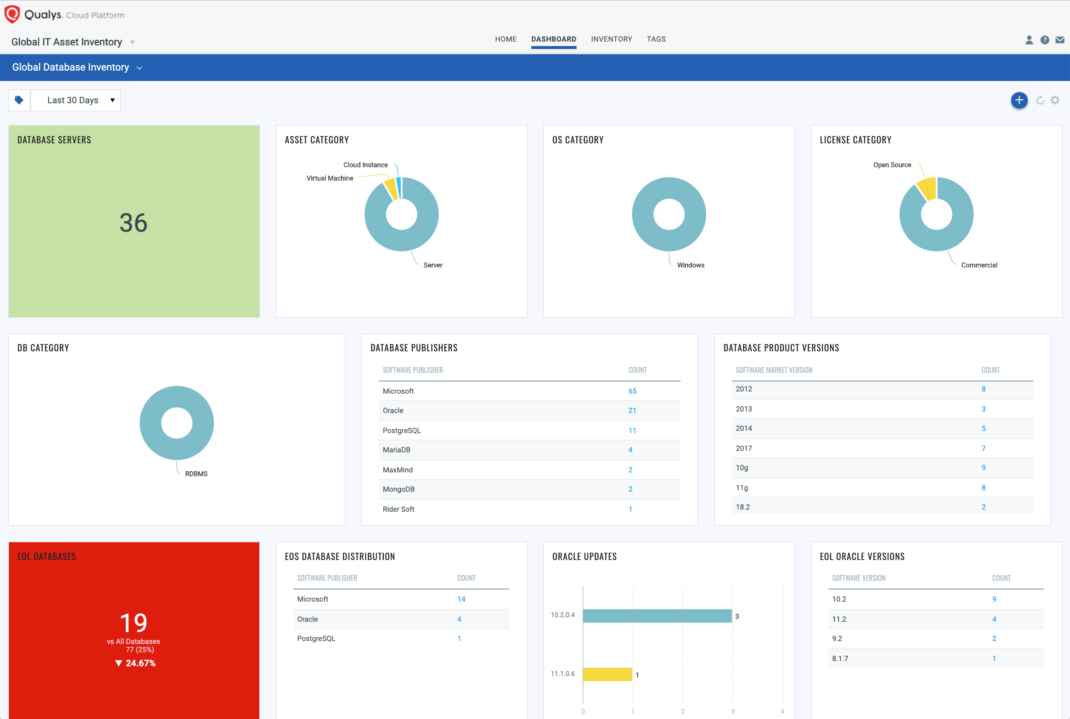
Database Protection in Your Compliance Program
Spot checking each database instance for misconfigurations or any other weak settings is a nearly impossible task, and leaving them vulnerable is not an option either. To ease the efforts required for ensuring security IT assets in general, and especially databases, Qualys PC has efficiently devised its controls and has helped organizations take proactive measures to strengthen database security. Built with the combination of a robust platform, intelligent architecture, and support of the extensive policies and controls, Qualys ensures that the security of your databases is not compromised.