Vulners weekly digest #13

There are 4 sections:
Vulnerabilities
Tools
News
Research
Feedback: https://forms.gle/D17BaFwD5hJnKkUUA
Vulnerabilities

Vulnerability CVE-2020-5902 in F5 BIG-IP received a CVSS score of 10. Exploiting the vulnerability allows executing commands on behalf of an unauthorized user and completely compromising the system, for example, intercepting the traffic of web resources controlled by the controller.
https://vulners.com/thn/THN:02088F21DB6E2D58FA2FBFDB5C735108

Multiple vulnerabilities in popular remote desktop client Apache Guacamole (over 10 million downloads on Docker Hub). The bugs were found in March, and at the end of June Guacamole developers released version 1.2.0, which fixed them. The vulnerabilities allow an attacker who infected one of the remote systems with the client installed to perform a reverse attack via the RDP protocol and capture the system from which remote administration is performed.
Since some technical details of the errors are now published by Check Point, it is highly probable that the corresponding exploits will appear soon.
https://vulners.com/thn/THN:77F832E3FCBED966C47D5256B7841AFD
https://vulners.com/threatpost/THREATPOST:B6B17DDF563BDA6C7BB968C7C736774D
CVE-2020-2021
Critical vulnerability was discovered in the PAN-OS operating system for firewalls and corporate VPN installations from Palo Alto Networks (CVE-2020-2021). Exploiting the vulnerability allows an unauthorized attacker to bypass authentication. The problem affects versions of PAN-OS 9.1, older than 9.1.3; PAN-OS version 9.0, older than 9.0.9; PAN-OS 8.1 versions older than 8.1.15, and all versions of PAN-OS 8.0. The vulnerability has been fixed in PAN-OS 8.1.15, PAN-OS 9.0.9, PAN-OS 9.1.3 and in all later versions.
The U.S. Cyber Command has warned that foreign cybercriminals are likely to attempt to exploit the discovered vulnerability in PAN-OS. Researchers at Boston's Rapid7 found on the network nearly 70 thousand devices based on PAN-OS, 40% of which protect networks in the United States.
https://vulners.com/threatpost/THREATPOST:14236108003AC6A3E1AB861A15ECA88F
Tools

BLUESPAWN
An Active Defense and EDR software to empower Blue Teams. Looks COOL.
https://github.com/ION28/BLUESPAWN
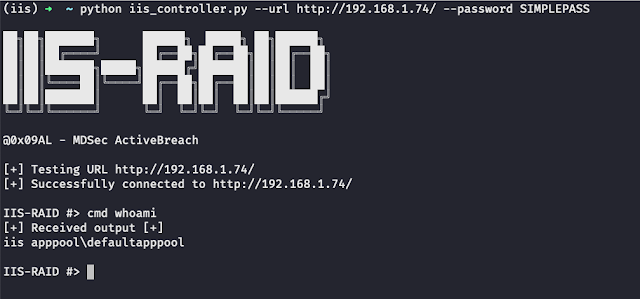
**IIS-Raid
**IS Raid is a native IIS module that abuses the extendibility of IIS to backdoor the web server and carry out custom actions defined by an attacker.
https://vulners.com/kitploit/KITPLOIT:7334903124975060426

**Kube-Bench
**kube-bench is a Go application that checks whether Kubernetes is deployed securely by running the checks documented in the CIS Kubernetes Benchmark.
https://vulners.com/kitploit/KITPLOIT:2999774102121351087
News

University of California, San Francisco (UCSF) paid $ 1.14 million to ransomware Netwalker.
Earlier, on June 1, the operator Netwalker hacked into the internal network of the UCSF Medical School, stealing and encrypting information including personal data of students and staff, medical research data and information about financial transactions.
Netwalker is a ransomware that appeared in the fall of 2019 and works under the Ransomware as a Service (RaaS) scheme.
https://vulners.com/threatpost/THREATPOST:953F87EC9AB118D2C3EFBC3D8169CC30

EvilQuest was discovered earlier this week by K7 Lab and analyzed by a team of researchers from Malwarebytes, Jamf and BleepingComputer. It encrypts files in a compromised system, but masquerading as a ransomware, it also has the ability to collect information from an infected host, including a keylogger and theft of cryptocurrency wallet data.
EvilQuest will check whether it is running on a virtual machine, as well as the presence of popular anti-virus products (Avast, Kaspersky, Mcaffee, etc.) in the attacked system. After encrypting the files, he offers to pay $ 50 for a static bitcoin wallet, however, he leaves no way of feedback, which makes it impossible to link the payment to a specific victim.
After the victim has paid the ransom, the attacker will still remain in the system and will collect the data of interest to him, and the files will remain encrypted. EvilQuest is the third identified ransomware species for MacOS after KeRanger and Patcher.
- https://vulners.com/thn/THN:A62E7777947C6A6EA407B313FAAD2F34
- https://vulners.com/threatpost/THREATPOST:B3541DE31E8F05DC7155F0B873AF67D2
- https://vulners.com/malwarebytes/MALWAREBYTES:76A9F8E0428E8BEC56B1C3CCA3D6D5E5

Facebook reported an incident involving a breach of confidentiality by social network users. According to the company, about 5,000 software developers continued to receive user data even after the expiration of the period of access to information by applications.
The Facebook privacy mechanism blocks applications from accessing user data if users have not used the programs for 90 days. According to Facebook, in some cases the security mechanism was not activated and allowed applications to continue accessing user data.
https://vulners.com/threatpost/THREATPOST:42E9A757393EF46DCDE909FB5D3A271F
Research
Vulnserver Exploit vs Windows Defender Exploit Guard. Great write-up, worth a thorough read: https://chadduffey.com/2020/06/27/VulnServerVSExploitGuard.html
Exploit Guard vs Process (DLL) Injection: https://chadduffey.com/2020/07/01/ExploitGuardImageLoads.html
Red Team C2 over VirusTotal - SharpHungarian - C#
This is an unifished console app for defeating EDR, defeating internal centralised loggin, and using Virustotal as an outbound command and control channel for C2.
https://github.com/hadur-borzsei-kallo/SharpHungarian
Elastic Security opens public detection rules repo: https://www.elastic.co/blog/elastic-security-opens-public-detection-rules-repo
Interesting tactic by Ratty & Adwind for distribution of JAR appended to signed MSI - Securityinbits: https://www.securityinbits.com/malware-analysis/interesting-tactic-by-ratty-adwind-distribution-of-jar-appended-to-signed-msi
Feedback: https://forms.gle/D17BaFwD5hJnKkUUA
