Critical Apache Guacamole Flaws Put Remote Desktops at Risk of Hacking
6.7 Medium
CVSS3
Attack Vector
LOCAL
Attack Complexity
HIGH
Privileges Required
LOW
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:L/AC:H/PR:L/UI:R/S:U/C:H/I:H/A:H
6.2 Medium
CVSS2
Access Vector
LOCAL
Access Complexity
HIGH
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:L/AC:H/Au:N/C:C/I:C/A:C
A new research has uncovered multiple critical reverse RDP vulnerabilities in Apache Guacamole, a popular remote desktop application used by system administrators to access and manage Windows and Linux machines remotely.
The reported flaws could potentially let bad actors achieve full control over the Guacamole server, intercept, and control all other connected sessions.
According to a report published by Check Point Research and shared with The Hacker News, the flaws grant “an attacker, who has already successfully compromised a computer inside the organization, to launch an attack on the Guacamole gateway when an unsuspecting worker tries to connect to an infected machine.”
After the cybersecurity firm responsibly disclosed its findings to Apache, the maintainers of Guacamole, on March 31, the company released a patched version in June 2020.
Apache Guacamole is a popular open-source clientless remote desktop gateways solution. When installed on a company’s server, it allows users to remotely connect to their desktops simply using a web browser post an authentication process.
Notably, Apache Guacamole remote desktop application has amassed over 10 million downloads to date on Docker Hub.
Memory Corruption Flaw to RCE
The attacks stem from one of the two possible ways the gateway can be taken over: either by a compromised machine inside the corporate network that leverages an incoming benign connection to attack the Apache gateway or a rogue employee who uses a computer inside the network to hijack the gateway.
Check Point team said it identified the flaws as part of Guacamole’s recent security audit, which also added support for FreeRDP 2.0.0 towards the end of January 2020.
It’s worth pointing out that FreeRDP, an open-source RDP client, had its own fair share of remote code execution flaws, which were disclosed early last year following the release of 2.0.0-rc4.
“Knowing that vulnerabilities in FreeRDP were only patched on version 2.0.0-rc4, this means that all versions that were released before January 2020 are using vulnerable versions of FreeRDP,” Check Point researcher Eyal Itkin said.
Here’s a quick summary of all flaws discovered:
- Information disclosure vulnerabilities (CVE-2020-9497) — Two separate flaws were identified in the developers’ custom implementation of an RDP channel used to handle audio packets from the server (“rdpsnd”). The first of the two flaws permits an attacker to craft a malicious rdpsnd message that could lead to an out-of-bounds read similar to Heartbleed. A second bug in the same channel is a data leak that transmits the out-of-bounds data to a connected client.
The third information disclosure bug is a variant of the aforementioned flaw that resides in a different channel called “guacai,” responsible for audio input and is disabled by default.
-
Out-of-bounds reads in FreeRDP — Looking to find a memory corruption vulnerability that could be leveraged to exploit the above data leaks, Check Point said they uncovered two additional instances of out-of-bounds reads that take advantage of a design flaw in FreeRDP.
-
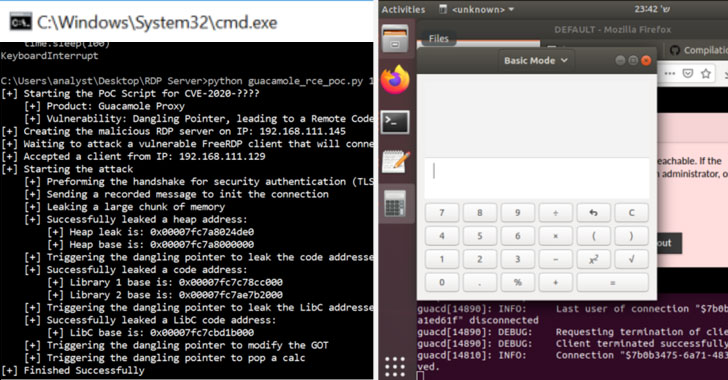
Memory Corruption flaw in Guacamole (CVE-2020-9498) — This flaw, present in an abstraction layer (“guac_common_svc.c”) laid over rdpsnd and rdpdr (Device Redirection) channels, arises from a memory safety violation, resulting in a dangling pointer that allows an attacker to achieve code execution by combining the two flaws.
Use-after-free vulnerabilities are memory corruption bugs that typically occur when an application tries to use memory space that is no longer assigned to it. This usually causes a program to crash but can also sometimes lead to other unintended consequences, such as code execution that can be exploited by malicious actors.
By using vulnerabilities CVE-2020-9497 and CVE-2020-9498, “a malicious corporate computer (our RDP ‘server’) can take control of the guacd process when a remote user requests to connect to his (infected) computer,” Itkin said.
A Case of Privilege Escalation
More concerning, Check Point found it was possible to seize control of all of the connections in the gateway from only a single guacd process, which runs on the Guacamole server to handle remote connections to the corporate network.
In addition to controlling the gateway, this privilege escalation allows an attacker to eavesdrop on all incoming sessions, record the credentials used, and even start new sessions to control the rest of the organization’s computers.
“While the transition to remote work from home is a necessity in these tough times of the COVID-19 pandemic, we can’t neglect the security implications of such remote connections,” Itkin concluded. “When most of the organization is working remotely, this foothold is equivalent to gaining full control over the entire organizational network.”
“We strongly recommend that everyone makes sure that all servers are up-to-date, and that whatever technology used for working from home is fully patched to block such attack attempts.”
6.7 Medium
CVSS3
Attack Vector
LOCAL
Attack Complexity
HIGH
Privileges Required
LOW
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:L/AC:H/PR:L/UI:R/S:U/C:H/I:H/A:H
6.2 Medium
CVSS2
Access Vector
LOCAL
Access Complexity
HIGH
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:L/AC:H/Au:N/C:C/I:C/A:C