Vulners weekly digest #12

This week Vulners integrated with data about Android vulnerabilities!
Already available at Vulners DB: https://vulners.com/search?query=type:android
There's a lot more interesting news this week:
Combo of the Vulnerabilities
Serious tools
Some unusual news.
And very briefly on fresh research
Vulnerabilities

We already mentioned SMBleed in the last digest. This week, we managed to find some research on the subject. In the third part, the authors will show how it helped to achieve RCE.
CVE-2020-9332
SentinelOne researchers discovered a dangerous vulnerability in the USB for Remote Desktop bus driver from FabulaTech that redirects local USB devices to the remote system. The vulnerability (CVE-2020-9332) allows an attacker to increase his privileges on the system by adding spoofed devices.
Analysis: https://labs.sentinelone.com/click-from-the-backyard-cve-2020-9332

Researchers have discovered an unpatched, zero-day vulnerability in firmware for Netgear routers that put 79 device models at risk for full takeover, they said.
According to the researcher, the vulnerability affects 758 different firmware versions used in 79 Netgear routers over the years. The problem is contained in a web server component inside the vulnerable firmware of the Netgear router.
PoC code placed on GitHub for exploiting vulnerability demonstrates the process of launching Telnet daemon with superuser rights without password.
All links at the bottom of the news post: https://vulners.com/threatpost/THREATPOST:DF35DF449CB3A8F93C405B227A00E117

Researchers from the Palo Alto Network’s Unit 42 have discovered a total of 6 vulnerabilities in D-Link’s DIR-865L which is geared towards home network usage. Found in February 2020 and reported only last week. Currently, though, only a beta patch has been released and you may have to manually configure it.
- CVE-2020-13782 – Malicious Code Injection
- CVE-2020-13786 – CSRF
- CVE-2020-13785 – Lack of Encryption
- CVE-2020-13784 – Calculating Session Cookies
- CVE-2020-13783 – Plain Text Password
- CVE-2020-13787 – Weak Wifi Protocol
https://vulners.com/threatpost/THREATPOST:245E26684E2D6D9AC1CC8895F53365E9
CVE-2020-1181
The vulnerability was fixed in the last monthly update of Microsoft and a poc appeared a week later. Detailed vulnerability analysis with example exploitation:
Tools
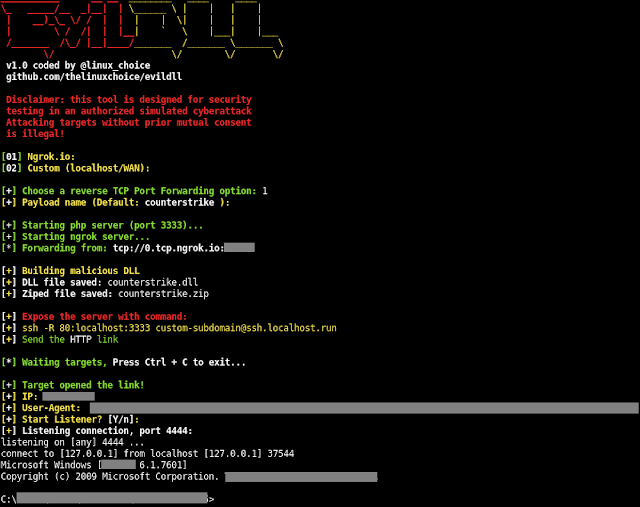
EvilDLL
Malicious DLL (Win Reverse Shell) generator for DLL Hijacking.
p.s. Usage of EvilDLL for attacking targets without prior mutual consent is illegal.
https://vulners.com/kitploit/KITPLOIT:6612426338264665401

SGN
SGN is a polymorphic binary encoder for offensive security purposes such as generating statically undetecable binary payloads.
https://vulners.com/kitploit/KITPLOIT:6458159002345904480
SGN execution Flow
"I am willing to give out the donation money for this project as a symbolic prize if anyone can write a YARA rule that can detect every encoded output."
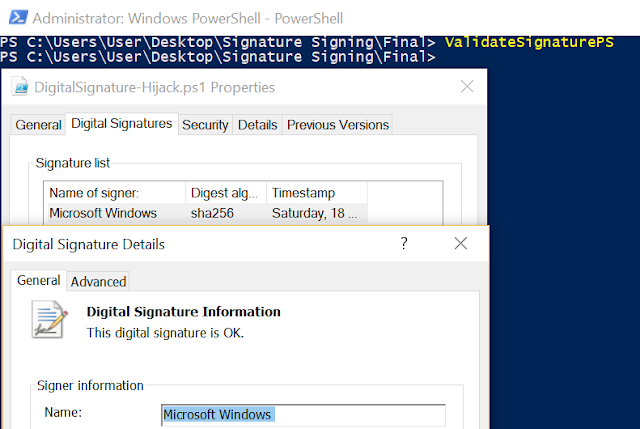
**Digital Signature Hijack
**It is a PowerShell script based on Matt Graeber research that can perform the following operations to digitally sign some executables/scripts on the host as Microsoft.
This could assist to bypass Device Guard restrictions and maintain stealthy in an engagement.
https://vulners.com/kitploit/KITPLOIT:7636175789108703829
News

Israeli researchers at Ben-Gurion University and the Weizmann Institute have discovered a new way of eavesdropping at a distance, which they called the Lamphone.
The essence of the new method is that lighting lamps, picking up sound, produce micro-vibrations that can be fixed using an electro-optical sensor connected to a telescope.

In a full-scale experiment, the researchers, taking vibration data from a 12-watt LED bulb from a distance of 25 meters, converting it into a digit and analyzing it using the Google Cloud Speech API, were able to recognize Beatles and Coldplay songs, as well as Trump's talk about Great again.
Protection options: to weight bulbs or to hang windows with impermeable curtains. Or negotiate with the lights off.
https://vulners.com/threatpost/THREATPOST:4FE49DA81A959EAE281BF9BDC50F7049

Noam Rotham and Ran Locar, vpnMentor researchers, published a report on a large-scale leak of data from specialized dating applications revealed at the end of May - 3somes, Cougary, Xpal, BBW Dating, Casualx, SugarD, Herpes Dating, GHunt and several others.
Among these applications there are both traditional ones (such as SugarD, an analogue of the domestic Zolushka Project, or Casualx), and specific ones for lovers of group sex, LGBT dating, and fetishists.
The drain contained more than 845 GB of data, including private photographs and also personal data, names, dates of birth and email addresses specified during registration. According to vpnMentor, the leak concerned hundreds of thousands, if not millions of users of services.
What is this for? To collect dirt and information about the addictions of a user.
https://vulners.com/wired/WIRED:CCD41ED23C65CAA34588CE383DE28FBB

According to companies Sanguine Security and ESET, hackers from the Magecart group hacked into three large online stores and injected their malicious code into them, with the help of which they stole payment card data entered by customers.
The websites of Clair's and its partner Icing were compromised from April 25 to 30, as a result of which all payment data was redirected to the claires-assets .com domain, registered just 4 weeks before the attack. As a result, everyone who made purchases on this site during the specified period of time is at risk of losing money from their payment cards.
Another site belonging to the European trading network Intersport (more precisely, its local versions for Croatia, Serbia, Slovenia, Montenegro and Bosnia) was hacked on April 30. On May 3, the malicious code was cleaned up, but on May 14, resources were hacked again. This time everything was corrected within a few hours. Intersport, by the way, also has a Russian local version of its website.
https://vulners.com/threatpost/THREATPOST:63A5AF6DBA80B1406297BB5825D56E32
Research
Tunneling with ProxyJump - Multi-hop SSH Tunnels with one simple configuration option.
https://medium.com/maverislabs/proxyjump-the-ssh-option-you-probably-never-heard-of-2d7e41d43464
Understanding NTLM relay in depth. NTLM relay is a technique of standing between a client and a server to perform actions on the server while impersonating the client
Detecting PoshC2 - Indicators of Compromise from a PoshC2 developer. PoshC2 is primarily written in Python3 and follows a modular format to enable users to add their own modules and tools, allowing an extensible and flexible C2 framework.
https://labs.nettitude.com/blog/detecting-poshc2-indicators-of-compromise
zloader: VBA, R1C1 References, and Other Tomfoolery. Malicious excel document analysis.
https://clickallthethings.wordpress.com/2020/06/19/zloader-vba-r1c1-references-and-other-tomfoolery/
Please leave your review. A few questions will take no more than one minute and helps us become better: https://forms.gle/D17BaFwD5hJnKkUUA