Vulners weekly digest #11

4 sections:
Vulnerabilities
Tools
News
Researches (red teaming, threat hunting, malware)
Vulnerabilities

June's "the second Tuesday patch" has become the largest in the history of Microsoft. The patches fix 129 vulnerabilities – the maximum number of security issues ever closed by Microsoft in a single "fix Tuesday". However, despite the number of vulnerabilities, none of them is a zero-day vulnerability.
The most dangerous security issues fixed by Microsoft on June 9th:
- CVE-2020-1181 - remote code execution in Microsoft SharePoint;
- CVE-2020-1225, CVE-2020-1226 - remote code execution in Microsoft Excel;
- CVE-2020-1223 - remote code execution in Word for Android;
- CVE-2020-1248 - remote code execution in the Windows Graphics Device Interface (GDI);
- CVE-2020-1281 - remote code execution in Windows OLE;
- CVE-2020-1299 - remote code execution during processing of .LNK files;
- CVE-2020-1300 - remote code execution in the print spooler component;
- CVE-2020-1301 - remote code execution in the Windows SMB protocol (Server Message Block);
- CVE-2020-1213, CVE-2020-1214, CVE-2020-1215, CVE-2020-1216, CVE-2020-1230, CVE-2020-1260 - remote code execution in the Windows VBScript scripting engine.
It is recommended to test for bug updates and install them as soon as possible. Recently, malware developers have been closely following Microsoft's monthly updates. They select the most useful vulnerabilities, using the diff utility find what exactly has been fixed, and create exploits for further attacks.
https://vulners.com/thn/THN:882595A940E5AB15E8B9C472154ACA45
https://vulners.com/threatpost/THREATPOST:B2D0023D9A73CEE9C328A0927149D5B2
CallStranger CVE-2020-12695
The vulnerability allows an attacker to conduct attacks of the type Reflected Amplified TCP DDOS Attack using millions of devices with the UPnP service enabled.
Universal Plug and Play (UPnP) - a set of network protocols for universal automatic configuration of network devices for home and corporate use. This service works both in home routers and in many IoT devices. The UPnP service does not provide authorization and is almost always enabled by default.
The vulnerability consists in the ability to specify an arbitrary URL as the Callback header, to which the URL will be sent a response. The UPnP service does not perform any checks on whether the message recipient and the address specified in the header are located in the same address space, which allows you to specify any destination node.
It is recommended to disable the UPnP service if it is not used. If this feature is not available and your device allows you to set up the service in detail - set a limit for SUBSCRIBE/NOTIFY messages to accept and send data only to local (private) addresses.

ZecOps cybersecurity researchers have discovered a new critical vulnerability (CVE-2020-1206) in the Microsoft Server Message Block (SMB) network communication protocol. Its operation allows attackers to remotely obtain confidential data from the kernel memory, and in combination with the previously discovered "worm-like" vulnerability SMBGhost in Windows 10 (CVE-2020-0796), the problem can be used to remotely execute code. PoC: https://github.com/ZecOps/CVE-2020-1206-POC
https://vulners.com/thn/THN:17F11846886656062FA1EA84D1C74534
Tools
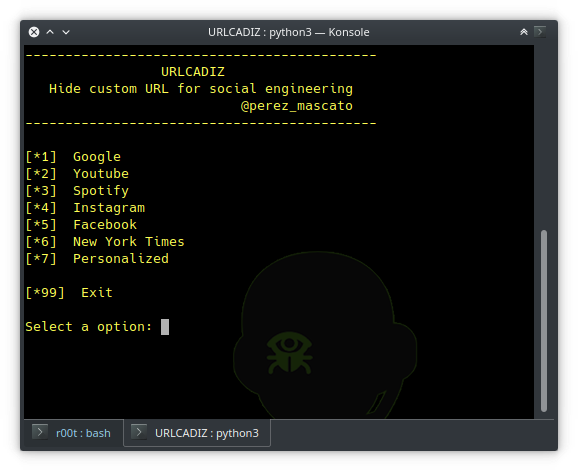
URLCADIZ
A simple script to generate a hidden url for social engineering.
https://vulners.com/kitploit/KITPLOIT:697990765205512366
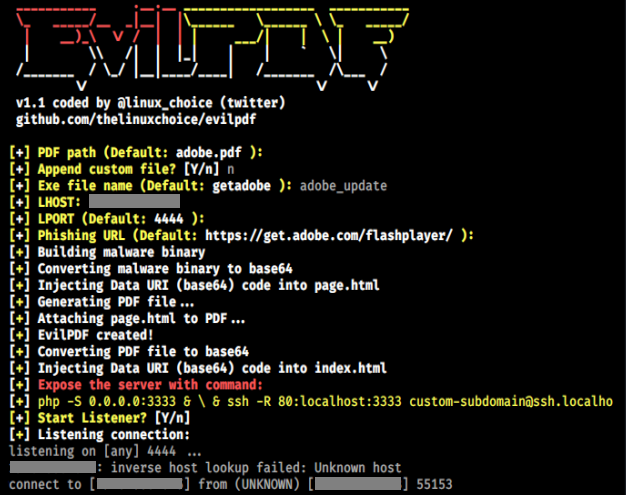
EvilPDF
Hiding executable files in PDF documents
https://vulners.com/kitploit/KITPLOIT:4909802323035039504

BabyShark
This is a basic C2 generic server written in Python and Flask.
https://vulners.com/kitploit/KITPLOIT:2200097804667459997
News
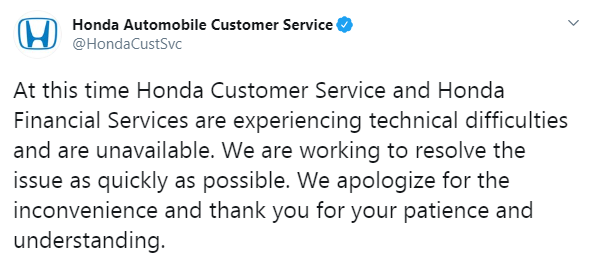
The Ekans ransomware attack disabled not only the customer service and financial services of the company.
According to the BBC, the internal network is encrypted, including mail servers. But more unpleasantly, the cyber attack affected Honda's production systems outside of Japan. And that means losing a lot of money.
Security researcher Milkream discovered a sample of Snake in VirusTotal, which was customized to attack Honda (the malware is specially programmed to check the name of the internal network mds.honda.com). Ekans aka SNAKE is a relatively new type of ransomware, discovered in December 2019. According to some researchers is the development of the Megacortex Ransomvari. Judging by some functionality, Ekans may be specifically designed for attacks on industrial control systems.
https://vulners.com/malwarebytes/MALWAREBYTES:BB5BB1F670997E83BD9555CB9995EB19
https://vulners.com/threatpost/THREATPOST:5E456ED94AC99EBFF8DE0E4DD9F16138

According to BleepingComputer, researchers at Abuse [.] Ch have identified a phishing campaign that uses a suggestion to vote anonymously on Black Lives Matter as a decoy. Well, and in the attached "voting form" contains a banking Trojan TrickBot.
It seems that the data on COVID-19 is beginning to lose its popularity as a bait in phishing mailings, in their place comes a new hype topic about BLM.
https://vulners.com/threatpost/THREATPOST:9BCCB9AB2D5CB0A94DC1E05B2C57F614

An unknown little Indian IT company provides hacking services, and in eight years has cracked more than 10 thousand accounts in email services.
Citizen Lab’s specialists, who have studied the infrastructure used by cybercriminals for more than two years, are confident that BellTroX employees are behind the cyber espionage campaign. “This is one of the largest disclosed custom espionage operations,” said Citizen Lab researcher John Scott-Railton
https://vulners.com/thn/THN:BB57F014633660940033AAB0D5877DC3
Researches
One of the ultimate goals of the red team may be exfiltration of the data. The guys rewrote one of the tools from Go to C # for themselves and described how they use it:
https://medium.com/@shantanukhande/red-team-using-sharpchisel-to-exfil-internal-network-e1b07ed9b49
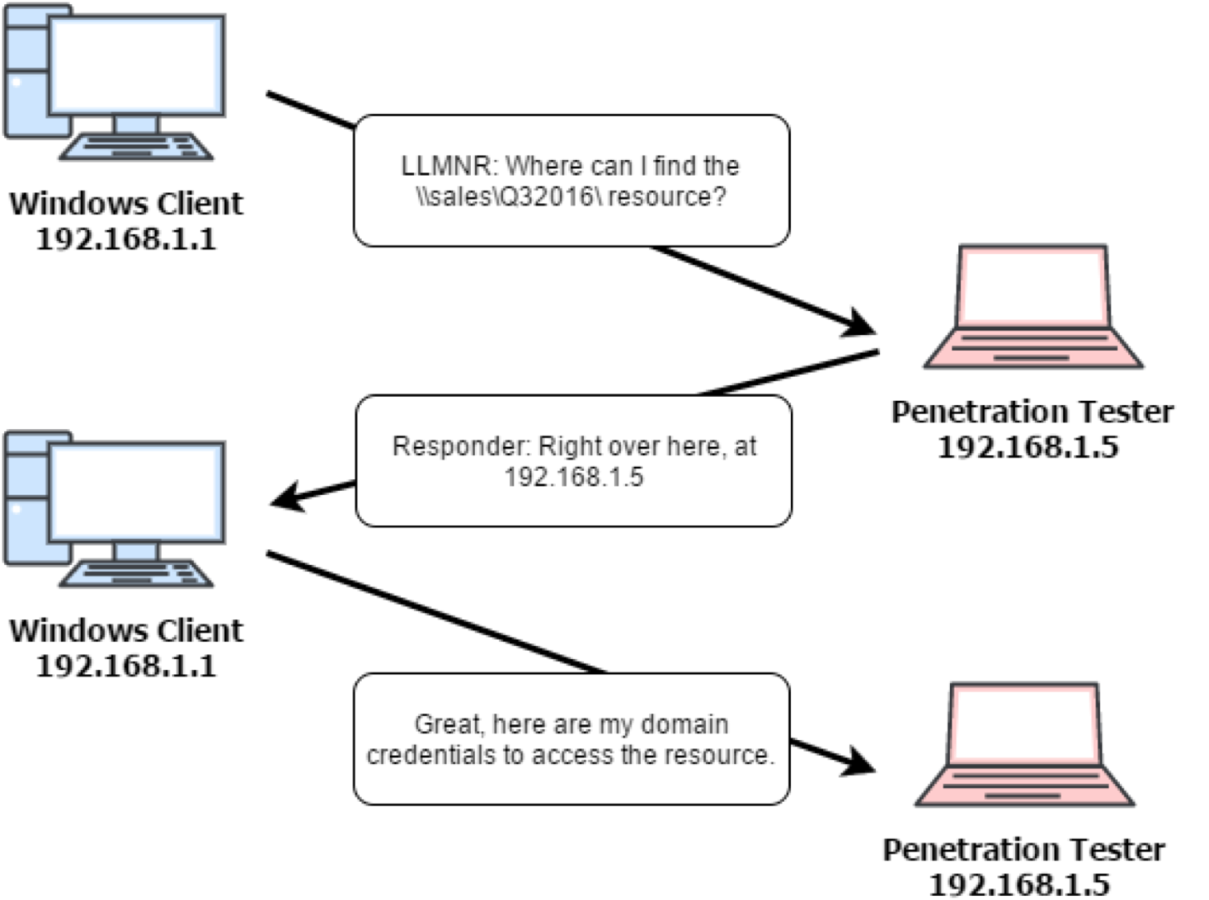
The functionality of the next tool is often used by pentester guys to hunt for account passwords. If you are from the red team and do not know about him, then it is better to familiarize yourself. If you are from the blue team and have not seen any responders in the logs, then it is better to test for a future detection.

You can’t just go and walk past a good research: https://medium.com/@valeriyshevchenko/from-crlf-to-account-takeover-a94d7aa0d74e?sk=54abf996cacadfe53113700a03181bb8
Web shell threat hunting with Azure Sentinel and Microsoft Threat Protection:
Ransomware has recently increased its activity, as a result of which it appears in more researches on the analysis of ransomware functional. TAU Threat Analysis: Hakbit Ransomware.
https://www.carbonblack.com/2020/06/08/tau-threat-analysis-hakbit-ransomware
Please leave your review. A few questions will take no more than one minute and helps us become better: https://forms.gle/D17BaFwD5hJnKkUUA