Vulners weekly digest #10

Default 4 sections:
Vulnerabilities
Tools
News
Threat hunting and malware research
Vulnerabilities
Apple has released updates to fix a CVE-2020-9859 that was used to jailbreak an iPhone with iOS 13.5. The vulnerability affects the iOS kernel and can allow an application to execute arbitrary code with kernel privileges.
CVE-2020-2883 in the Oracle WebLogic Server product of Oracle Fusion Middleware. Unauthenticated remote code execution can be achieved by sending a serialized 'BadAttributeValueExpException' object over the T3 protocol to vulnerable versions of WebLogic.
https://vulners.com/metasploit/MSF:EXPLOIT/MULTI/MISC/WEBLOGIC_DESERIALIZE_BADATTR_EXTCOMP
CVE-2020-3956 VMware Cloud Director
VMware Cloud Director is the popular software for deploying, automating and managing virtual infrastructure resources in multi-user cloud environments. The critical vulnerability is due to incorrect processing of input information and can be used by an authorized attacker to send malicious traffic to Cloud Director, resulting in arbitrary code execution.
Cisco Systems CVE-2020-10136
Vulnerability in products of Cisco Systems and other vendors, connected with the tunneling protocol IP-in-IP. An unauthorized attacker can route network traffic through the vulnerable device, conduct a DDoS attack, cause information leakage, and bypass network access controls.
https://vulners.com/threatpost/THREATPOST:B664DFB1B57D66837AE025D5CD687F70
PoC: github.com/CERTCC/PoC-Exploits/tree/master/cve-2020-10136
Tools
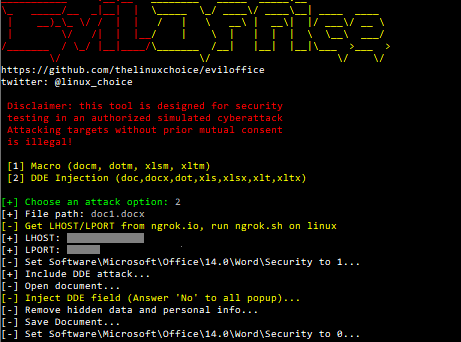
Eviloffice
Win python script to inject Macro and DDE code into Excel and Word documents (reverse shell).
https://vulners.com/kitploit/KITPLOIT:5850599175753788165
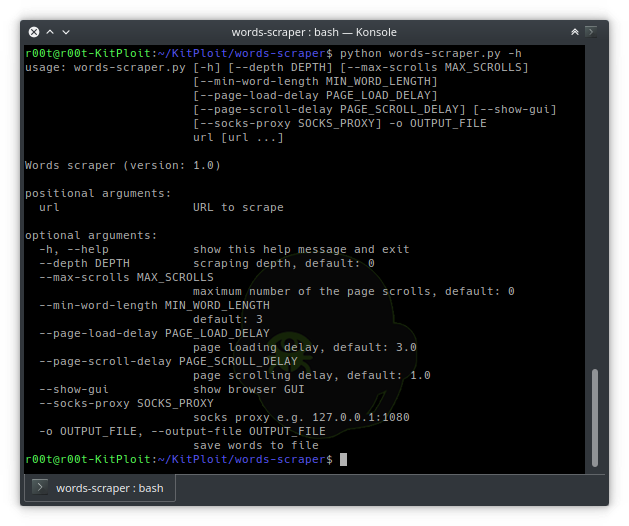
**Words Scraper
**Selenium based web scraper to generate passwords list.
https://vulners.com/kitploit/KITPLOIT:2751138742638729202
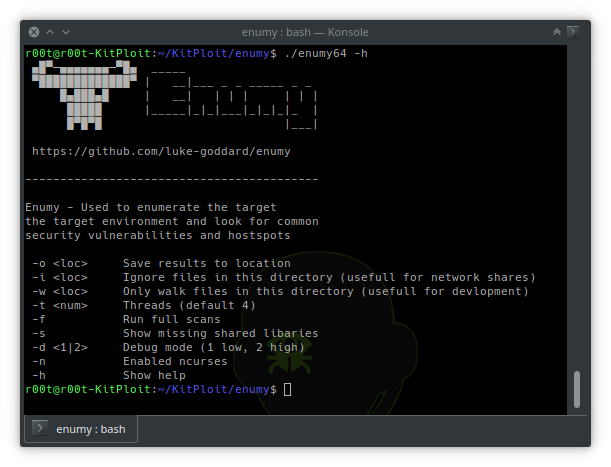
Enumy
Enumy is an ultra fast portable executable that you drop on target Linux machine during a pentest or CTF in the post exploitation phase. Running enumy will enumerate the box for common security vulnerabilities.
https://vulners.com/kitploit/KITPLOIT:6384515767173020709
News

This week, Cisco Talos reported two new vulnerabilities in ZOOM that potentially allow remote code execution on the target machine.
- The first vulnerability is the incorrect processing of GIF images, which can lead to the recording of a file created by an attacker with ZOOM user rights.
- The second vulnerability is the incorrect processing of messages by the ZOOM client, due to which a hacker can send a special message to the chat and achieve remote code execution (though this requires some “target interaction” with the attacked user).
Problems were discovered in May, and by now application developers have released relevant updates. Default recommendations - urgently update your ZOOM client.
https://vulners.com/thn/THN:96B1CC4A7203A91DE0E44071518570BB
Maze
U.S. military contractor Westech International was hacked by ransomware Maze, resulting in sensitive data being encrypted and copied by hackers. Leak confirmations are already posted on the network.

And all would be fine, after all, Westech International is not the first US military contractor to fall under ransomware, this company is directly involved in servicing the Minuteman III nuclear missiles that are in service with the United States.
https://vulners.com/threatpost/THREATPOST:E1D05D08F7124D4E36B712ECB4D58716
https://vulners.com/hackread/HACKREAD:7081B458B17F63A1C9C7DFFF7A19CD59
Sodinokibi
The REvil ransomware operators (Sodinokibi) launched an auction site like eBay, where they will put up for sale data stolen from companies. The first to be auctioned were data from a Canadian agricultural company whose networks were hacked last month. Starting price is $ 50 thousand in Monero cryptocurrency. The REvil operators abandoned Bitcoin in favor of Monero for security reasons in April this year.
Sodinokibi promise to soon reveal Madonna’s data stolen May 12 from the American law firm Grubman Shire Meiselas & Sacks, which they threatened with last week. Estimated starting price - $ 1 million.
https://vulners.com/malwarebytes/MALWAREBYTES:707641E0A447B0903AFE233DA91F69C7
Threat hunting and malware research
Detect in-memory .NET assemblies, detailing a case study of Cobalt Strike’s execute-assembly feature: https://www.mdsec.co.uk/2020/06/detecting-and-advancing-in-memory-net-tradecraft
Using macros in microsoft documents is one of the most popular techniques among attackers. Many security vendors currently do not have detection mechanisms to run these samples. Building signatures and correlation rules for this type of attack is an important task.
Research: https://www.lastline.com/labsblog/evolution-of-excel-4-0-macro-weaponization
Files as well as macros are actively used by attackers. One of the non-typical ways seen in the use of the APT group: https://blog.malwarebytes.com/threat-analysis/2020/06/higaisa
We can not just not mention the next analysis of the functionality of the new ransomware in our digest: https://www.carbonblack.com/2020/06/03/tau-threat-analyis-medusa-locker-ransomware
Please leave your review. A few questions will take no more than one minute and helps us become better: https://forms.gle/D17BaFwD5hJnKkUUA
