All-in-one vulnerability intelligence
Prioritize remediation efforts with rich context beyond the CVSS.
Drive offensive and defensive efforts with the latest updates on exploits.
Integrate vulnerability intelligence delivered in normalized and correlated machine-readable format.
0average CVE added per day
0k+exploits for popular software and systems
0mln+security advisories and bulletins
0average entries added per day
0hoursaverage hours to exploit published
0+software vendors and other security sources
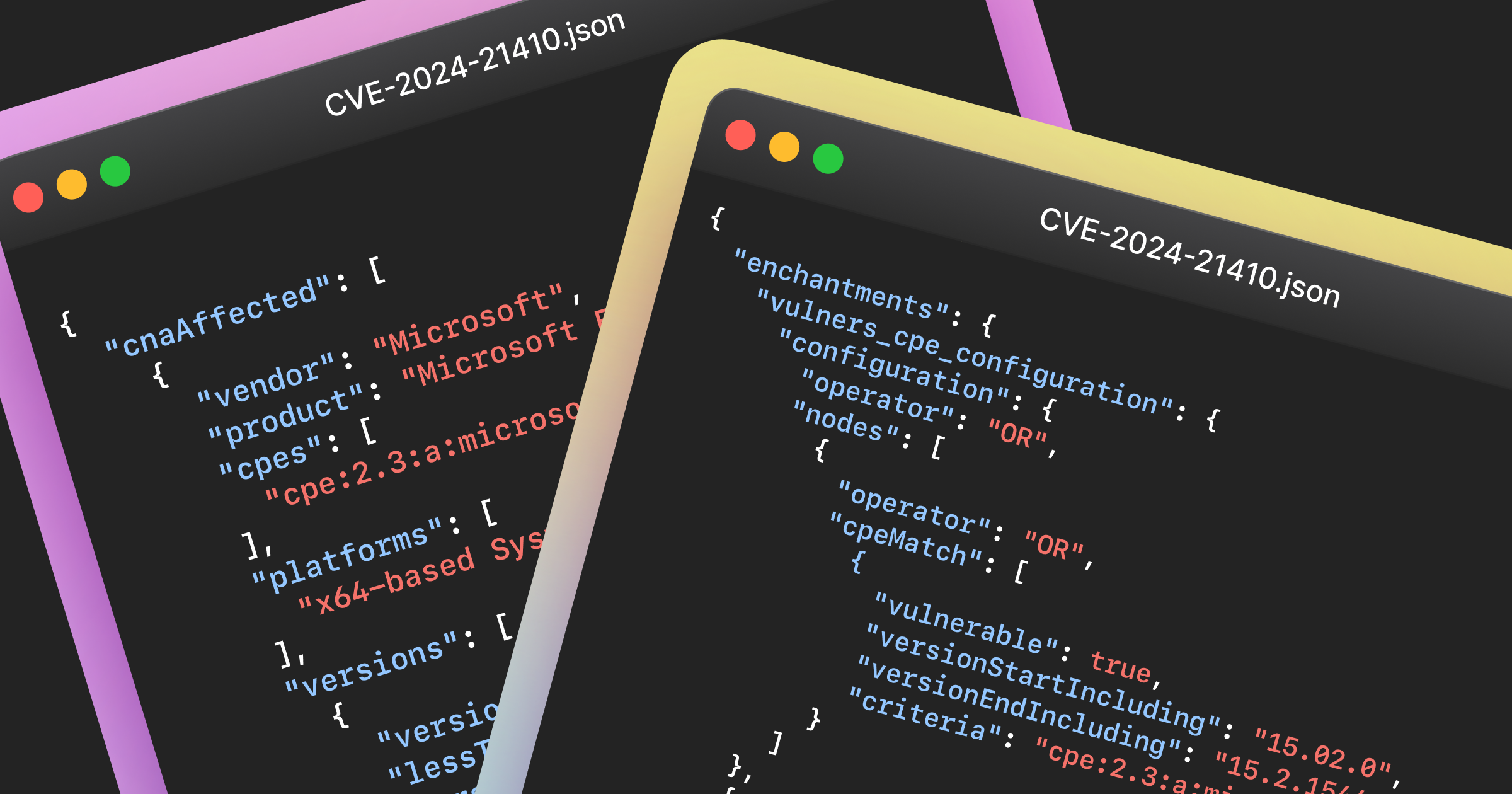
At Vulners core is a graph database
with a robust API allowing
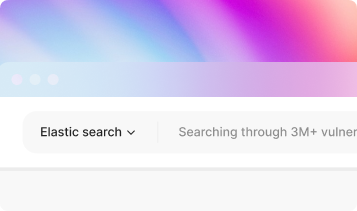
Precise search of vulnerabilities by CPE, name/version, or using full-text search
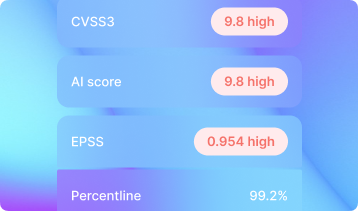
Getting all metrics like CVSS, EPSS,Vulners AI Score, CWE, exploited in the wild, and more with one call
Retrieving interlinked information about exploits, news, and blog posts
See how our API works — examples of queries with real responses
curl -XPOST https://vulners.com/api/v3/search/id \
-H 'Content-Type: application/json' \
-d '{
"id": "CVE-2024-21762",
"fields": ["*"],
"apiKey": "{API key}"
}'
APIPythonResponse
1Get full document by ID
2Full text search in the Database
3Get vulnerabilities by CPE
4Get vulnerabilities by product & version
5Search Exploits
Get key vulnerability intelligence insights
ReferencesDocuments in the database that reference the vulnerability
Is Wild ExploitedVulnerability included in the CISA KEV list or there are other exploitation evidence
Social networks activityActively discussed vulnerabilities often pose more risk
Vulners AI ScoreVulnerability impact estimation with our proprietary machine learning model
AI TagsChatGPT-powered classification of vulnerabilities for easy search and analysis
Exploits PoCInterlinked information about exploits PoC on popular resources
Documents HisoryWe track and store all changes to CVE and other documents in the database
CVSSVector and Base Score assigned by CNA and NVD
EPSSProbability of vulnerability exploitation in the next 30 days
Blog
Browse allStart using an API-first vulnerability intelligence platformDesigned for cybersecurity professionals like you
Power Your Products and OperationsWhether you're developing cybersecurity products or running an MSSP operation, our normalized and correlated vulnerability intelligence data streamlines your processes, all in a machine-readable format
Supercharge Your Vulnerability ManagementDon't just rely on CVSS scores. We provide rich context to help you prioritize remediation efforts, ensuring maximum impact on risk reduction
Stay Ahead of ThreatsKeep your defenses robust and your offensive strategies informed with our real-time updates on the latest exploits and vulnerabilities