
Microsoft and Adobe Patch Tuesday (July 2021) – Microsoft 117 Vulnerabilities with 13 Critical, Adobe 26 Vulnerabilities
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C
Microsoft Patch Tuesday – July 2021
Microsoft patched 117 vulnerabilities in their July 2021 Patch Tuesday release, and 13 of them are rated as critical severity.
Critical Microsoft Vulnerabilities Patched
CVE-2021-34448 – Scripting Engine Memory Corruption Vulnerability
This is being actively exploited. The vulnerability allows an attacker to execute malicious code on a compromised website if a user browses to a specially crafted file on the website. The vendor has assigned a CVSSv3 base score of 6.8 and should be prioritized for patching.
CVE-2021-34494 - Windows DNS Server Remote Code Execution Vulnerability
Microsoft released patches addressing a critical RCE vulnerability in Windows DNS Server (CVE-2021-34494). This CVE has a high likelihood of exploitability and is assigned a CVSSv3 base score of 8.8 by the vendor. This is only exploitable to DNS servers only; however, it could allow remote code execution without user interaction.
CVE-2021-33780 - Windows DNS Server Remote Code Execution Vulnerability
Microsoft released patches addressing a critical RCE vulnerability in DNS Server (CVE-2021-33780). This CVE has a high likelihood of exploitability and is assigned a CVSSv3 base score of 8.8 by the vendor.
CVE-2021-31979 - Windows Kernel Elevation of Privilege Vulnerability
This has been actively exploited and is assigned a CVSSv3 base score of 7.2 by the vendor. This should be prioritized for patching.
CVE-2021-34489 – DirectWrite Remote Code Execution Vulnerability
The vulnerability allows an attacker to host a website that contains a specially crafted file designed to exploit the vulnerability. The vendor has assigned a CVSSv3 base score of 7.8 and should be prioritized for patching.
CVE-2021-34467, CVE-2021-34468 – Microsoft SharePoint Server Remote Code Execution Vulnerability
Microsoft released patches addressing critical RCE vulnerabilities in SharePoint Server (CVE-2021-34467, CVE-2021-34468). These CVEs have a high likelihood of exploitability and are assigned a CVSSv3 base score of 7.1 by the vendor. Along with these patches, CVE-2021-34520 should be prioritized for patching.
CVE-2021-34527 – Windows Print Spooler Remote Code Execution Vulnerability
This Patch Tuesday follows out-of-band updates released to fix remote code execution affecting Windows Print Spooler vulnerability, popularly known as PrintNightmare. While Microsoft had released updates to fix PrintNightmare vulnerability, it is important to ensure necessary configurations are set correctly. We also published a blog post on how to remediate PrintNightmare using Qualys VMDR.
Adobe Patch Tuesday – July 2021
Adobe addressed 26 CVEs this Patch Tuesday, and 22 of them are rated as critical severity impacting Acrobat and Reader, Adobe Framemaker, Illustrator, Dimension, and Adobe Bridge products.
Discover Patch Tuesday Vulnerabilities in VMDR
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledge Base (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability:(qid:50112 OR qid:50113 OR qid:91787 OR qid:91788 OR qid:91789 OR qid:91790 OR qid:91791 OR qid:91792 OR qid:91793 OR qid:91794 OR qid:91795 OR qid:110386 OR qid:110387 OR qid:375700 OR qid:375706 OR qid:375707 OR qid:375708 OR qid:375713 OR qid:375714 OR qid:375715)
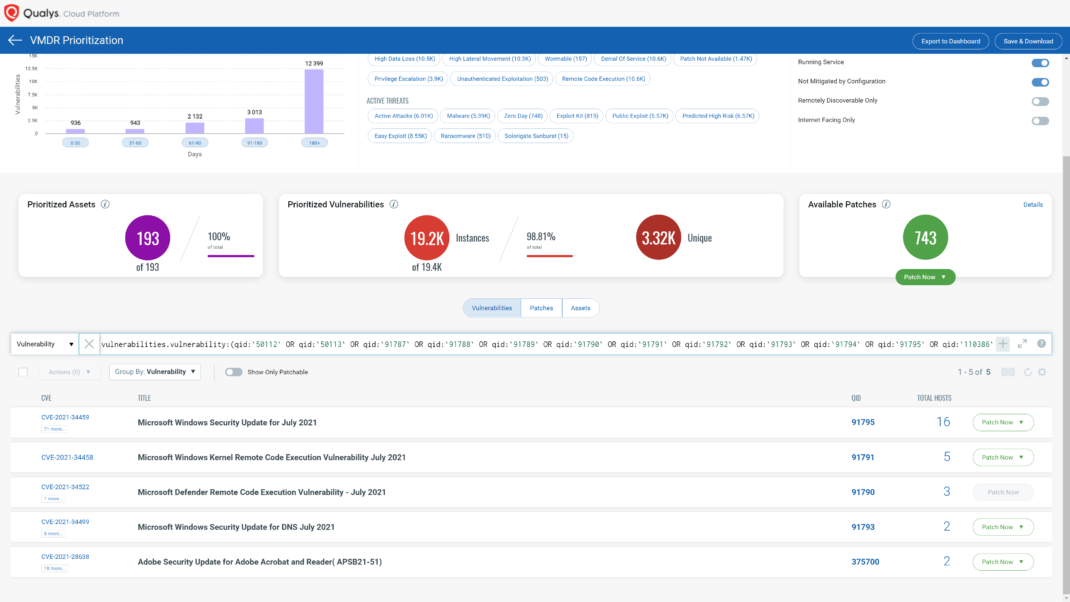
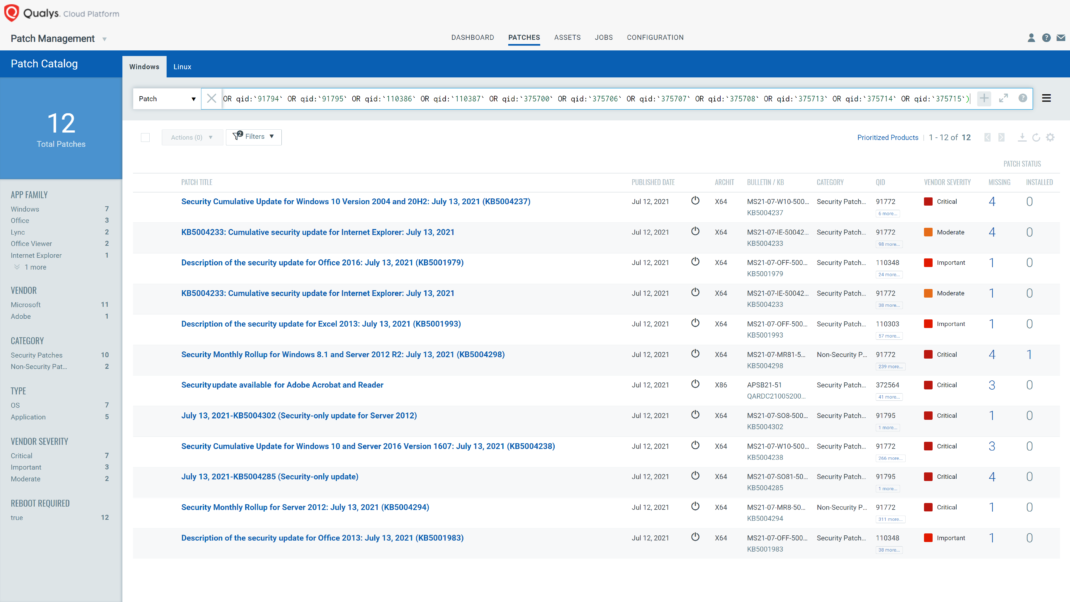
Respond by Patching
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches in one go.
The following QQL will return the missing patches pertaining to this Patch Tuesday:
(qid:50112 OR qid:50113 OR qid:91787 OR qid:91788 OR qid:91789 OR qid:91790 OR qid:91791 OR qid:91792 OR qid:91793 OR qid:91794 OR qid:91795 OR qid:110386 OR qid:110387 OR qid:375700 OR qid:375706 OR qid:375707 OR qid:375708 OR qid:375713 OR qid:375714 OR qid:375715)
Patch Tuesday Dashboard
The current updated Patch Tuesday dashboards are available in Dashboard Toolbox: 2021 Patch Tuesday Dashboard.
Webinar Series: This Month in Vulnerabilities and Patches
To help customers leverage the seamless integration between Qualys VMDR and Patch Management and reduce the median time to remediate critical vulnerabilities, the Qualys Research team is hosting a monthly webinar series This Month in Vulnerabilities and Patches.
We discuss some of the key vulnerabilities disclosed in the past month and how to patch them:
- Windows Print Spooler RCE Vulnerability
- Kaseya Multiple Zero-Day Vulnerabilities
- Sonicwall Buffer Overflow Vulnerability
- Microsoft Patch Tuesday, July 2021
- Adobe Patch Tuesday, July 2021
Join us live or watch on demand!
 Webinar July 15, 2021 or on demand.
Webinar July 15, 2021 or on demand.
About Patch Tuesday
Patch Tuesday QIDs are published at Security Alerts, typically late in the evening of Patch Tuesday, followed shortly after by PT dashboards.
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C