40,000 WordPress Sites affected by Vulnerability That Leads to Privilege Escalation in Login/Signup Popup WordPress Plugin
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
8.5 High
AI Score
Confidence
High
0.001 Low
EPSS
Percentile
23.4%
_📢 Did you know Wordfence runs a Bug Bounty Program for all WordPress plugin and themes at no cost to vendors?_Researchers can earn up to $10,400, for all in-scope vulnerabilities submitted to our Bug Bounty Program! Find a vulnerability, submit the details directly to us, and we handle all the rest.
On May 17th, 2024, during our Bug Bounty Extravaganza, we received a submission for an Arbitrary Options Update vulnerability in Login/Signup Popup, a WordPress plugin with more than 40,000 active installations. This vulnerability could be used by authenticated attackers, with subscriber-level access and above, to update arbitrary options which can easily be leveraged for privilege escalation.
Props to 1337_Wannabe who discovered and responsibly reported this vulnerability through the Wordfence Bug Bounty Program. This researcher earned a bounty of $938.00 for this discovery during our Bug Bounty Program Extravaganza. Our mission is to Secure the Web, which is why we are investing in quality vulnerability research and collaborating with researchers of this caliber through our Bug Bounty Program. We are committed to making the WordPress ecosystem more secure, which ultimately makes the entire web more secure.
Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability on May 28, 2024. Sites using the free version of Wordfence will receive the same protection 30 days later on June 27, 2024.
We contacted the XootiX team on May 24, 2024, and received a response on the next day. After providing full disclosure details, the developer released a patch on May 28, 2024. We would like to commend the XootiX team for their prompt response and timely patch.
We urge users to update their sites with the latest patched version of Login/Signup Popup, which is version 2.7.3, as soon as possible.
Vulnerability Summary from Wordfence Intelligence
Description: Login/Signup Popup ( Inline Form + Woocommerce ) 2.7.1 - 2.7.2 - Missing Authorization to Arbitrary Options Update **Affected Plugin:**Login/Signup Popup Plugin Slug:easy-login-woocommerce **Affected Versions:**2.7.1 - 2.7.2 CVE ID:CVE-2024-5324 **CVSS Score:**8.8 (High) CVSS Vector:CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H Researcher/s:1337_Wannabe **Fully Patched Version:**2.7.3 Bounty Awarded: $938.00
The Login/Signup Popup ( Inline Form + Woocommerce ) plugin for WordPress is vulnerable to unauthorized modification of data due to a missing capability check on the 'import_settings' function in versions 2.7.1 to 2.7.2. This makes it possible for authenticated attackers, with Subscriber-level access and above, to change arbitrary options on affected sites. This can be used to enable new user registration and set the default role for new users to Administrator.
Technical Analysis
Login/Signup Popup ( Inline Form + Woocommerce ) is a lightweight WordPress plugin, which can be used to add login, registration and password reset forms to WordPress with many different settings.
Examining the code reveals that the plugin uses the import_settings() function in the Xoo_Admin class to import the plugin admin settings.
add_action( 'wp_ajax_xoo_admin_settings_import', array( $this, 'import_settings' ) );
public function import_settings(){
$settings = $_POST['import'];
$options = json_decode( html_entity_decode( stripslashes ($settings ) ), true );
foreach ( $options as $key => $value ) {
update_option( $key, $value );
}
die();
}
Unfortunately, it was found that capability checks as well as nonce checks were missing in this function in the vulnerable version. This makes it possible for authenticated attackers with subscriber-level permission to invoke the AJAX function.
Further examination of the code revealed that there are no restrictions on the option names that can be updated. For example, modifiable settings are not limited to the plugin’s settings. This makes it possible to update arbitrary options by sending a direct request to the server with the option names and values that the attacker would like to change. WordPress site options control a variety of settings such as site urls, general settings, registration, and registration roles to name a few.
As with any Arbitrary Options Update vulnerability, this can be used to accomplish a complete site compromise by setting the default registration role to administrator and enabling user registration (if not already enabled). Once an attacker has edited the site options they can create an administrative account on the WordPress site and then, once registered and logged in, they can then manipulate anything on the targeted site, just like a normal administrator would. This includes the ability to upload plugin and theme files, which can be malicious zip files containing backdoors, and modifying posts and pages which can be leveraged to redirect site users to other malicious sites.
Wordfence Firewall
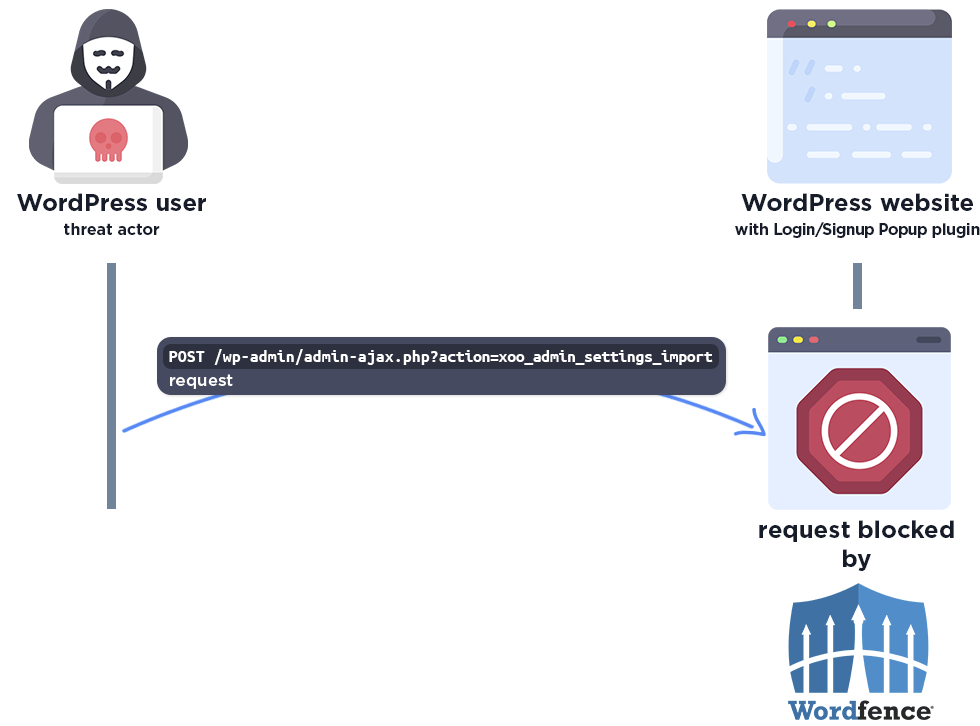
The following graphic demonstrates the steps to exploitation an attacker might take and at which point the Wordfence firewall would block an attacker from successfully exploiting the vulnerability.
The Wordfence firewall rule detects the malicious AJAX action and blocks the request.
Disclosure Timeline
May 17, 2024 – We received the submission for the Arbitrary Options Update vulnerability in Login/Signup Popup via the Wordfence Bug Bounty Program. May 24, 2024– We validated the report and confirmed the proof-of-concept exploit. May 24, 2024– We initiated contact with the plugin vendor asking that they confirm the inbox for handling the discussion. May 25, 2024– The vendor confirmed the inbox for handling the discussion. May 27, 2024– We sent over the full disclosure details. The vendor acknowledged the report and began working on a fix. May 28, 2024– Wordfence Premium, Care, and Response users received a firewall rule to provide protection against any exploits that may target this vulnerability. May 28, 2024– The fully patched version of the plugin, 2.7.3, is released. June 27, 2024 – Wordfence Free users will receive the same protection.
Conclusion
In this blog post, we detailed an Arbitrary Options Update vulnerability within the Login/Signup Popup plugin affecting versions 2.7.1 and 2.7.2. This vulnerability allows authenticated threat actors with subscriber-level permissions or higher to edit arbitrary site options which can be used to create administrator accounts. The vulnerability has been fully addressed in version 2.7.3 of the plugin.
We encourage WordPress users to verify that their sites are updated to the latest patched version of Login/Signup Popup.
Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability on May 28, 2024. Sites using the free version of Wordfence will receive the same protection 30 days later on June 27, 2024.
If you know someone who uses this plugin on their site, we recommend sharing this advisory with them to ensure their site remains secure, as this vulnerability poses a significant risk.
The post 40,000 WordPress Sites affected by Vulnerability That Leads to Privilege Escalation in Login/Signup Popup WordPress Plugin appeared first on Wordfence.
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
8.5 High
AI Score
Confidence
High
0.001 Low
EPSS
Percentile
23.4%