2023’s Critical WordPress Vulnerabilities and How They Work
9.9 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
0.238 Low
EPSS
Percentile
96.5%
 Did you know we're running a Bug Bounty Extravaganza again?
Did you know we're running a Bug Bounty Extravaganza again?
Earn over 6x our usual bounty rates, up to $10,000, for all vulnerabilities submitted through February 29th, 2024 when you opt to have Wordfence handle responsible disclosure!
In 2023, the Wordfence Threat Intelligence team's primary focus was to research high-impact, high- or critical-severity vulnerabilities. This means that we spent a lot of time looking for vulnerabilities like arbitrary file uploads, user password resets, authentication bypasses, and privilege escalations. Fortunately, we were able to discover a lot of these vulnerabilities and get them remediated before attackers could find and exploit them.
Now that we have launched our Bug Bounty Program that pays the biggest bounties for the most impactful research, we hope to continue a positive trend of researchers finding critical, high impact vulnerabilities and responsibly disclosing those through our program so we can work with vendors to ensure they get patched.
In today’s post, we’d like to highlight some of the big vulnerabilities of 2023 that we focused on, along with providing some background on these vulnerability types.
2023 Wordfence Critical Vulnerability Research in Review
Authentication Bypass
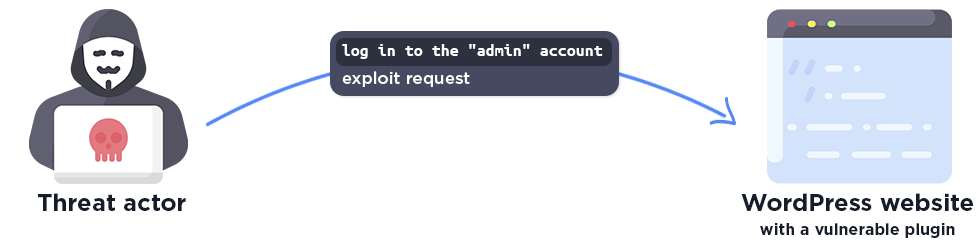
An authentication bypass vulnerability occurs when an attacker exploits weaknesses in the authentication mechanism to log into a user’s account, typically a high-privileged user. These vulnerabilities make it easy for threat actors to completely compromise a vulnerable WordPress site with minimal user interaction and often easy automation.
Authentication bypass exploits are special in that the attacker does not change or even know the credentials, but instead bypasses the authentication process. This means that the victim does not notice the attack, because their account is not changed, and the WordPress website administrator can log in in the same way.
Note that most authentication bypass vulnerabilities in WordPress also bypass two-factor authentication, so even that does not protect against the attack. It’s important to run a WordPress specific web application firewall, such as Wordfence, to provide protection against these types of attacks.
As seen, a single exploit request is enough for the attacker to gain administrator privileges on the website.
The Wordfence Team found a total of 13 authentication bypass vulnerabilities in 2023. You can find the details of these vulnerabilities below.
UserPro <= 5.1.1 - Authentication Bypass to Administrator
Plugin Slug: userpro Affected Versions:<= 5.1.1 CVE ID:CVE-2023-2437 **CVSS Score:**9.8 (Critical) Researcher/s: István Márton
RegistrationMagic <= 5.2.1.0 - Authentication Bypass
Plugin Slug: custom-registration-form-builder-with-submission-manager Affected Versions:<= 9.8 CVE ID:CVE-2023-2499 **CVSS Score:**9.8 (Critical) Researcher/s: István Márton
WP User Switch <= 1.0.2 - Authenticated (Subscriber+) Authentication Bypass via Cookie
Plugin Slug: wp-user-switch Affected Versions:<= 1.0.2 CVE ID:CVE-2023-2546 **CVSS Score:**8.8 (High) Researcher/s: István Márton
BP Social Connect <= 1.5 - Authentication Bypass
Plugin Slug: bp-social-connect Affected Versions:<= 1.5 CVE ID:CVE-2023-2704 **CVSS Score:**9.8 (Critical) Researcher/s: István Márton
MStore API <= 3.9.0 - Authentication Bypass
Plugin Slug: mstore-api Affected Versions:<= 3.9.0 CVE ID:CVE-2023-2733 **CVSS Score:**9.8 (Critical) Researcher/s: István Márton
MStore API <= 3.9.1 - Authentication Bypass
Plugin Slug: mstore-api Affected Versions:<= 3.9.1 CVE ID:CVE-2023-2734 **CVSS Score:**9.8 (Critical) Researcher/s: István Márton
MStore API <= 3.9.2 - Authentication Bypass
Plugin Slug: mstore-api Affected Versions:<= 3.9.2 CVE ID:CVE-2023-2732 **CVSS Score:**9.8 (Critical) Researcher/s: István Márton
User Email Verification for WooCommerce <= 3.5.0 - Authentication Bypass
Plugin Slug: woo-confirmation-email Affected Versions:<= 3.5.0 CVE ID:CVE-2023-2781 **CVSS Score:**8.1 (High) Researcher/s: István Márton
BookIt <= 2.3.7 - Authentication Bypass
Plugin Slug: bookit Affected Versions:<= 2.3.7 CVE ID:CVE-2023-2834 **CVSS Score:**9.8 (Critical) Researcher/s: István Márton
WordPress Social Login and Register (Discord, Google, Twitter, LinkedIn) <= 7.6.4 - Authentication Bypass
Plugin Slug: miniorange-login-openid Affected Versions:<= 7.6.4 CVE ID:CVE-2023-2982 **CVSS Score:**9.8 (Critical) Researcher/s: István Márton
Abandoned Cart Lite for WooCommerce <= 5.15.1 - Authentication Bypass
Plugin Slug: woocommerce-abandoned-cart Affected Versions:<= 5.15.1 CVE ID:CVE-2023-2986 **CVSS Score:**9.8 (Critical) Researcher/s: István Márton
Stripe Payment Plugin for WooCommerce <= 3.7.7 - Authentication Bypass
Plugin Slug: payment-gateway-stripe-and-woocommerce-integration Affected Versions:<= 3.7.7 CVE ID:CVE-2023-3162 **CVSS Score:**9.8 (Critical) Researcher/s: István Márton
Web3 – Crypto wallet Login & NFT token gating <= 2.6.0 - Authentication Bypass
Plugin Slug: web3-authentication Affected Versions:<= 2.6.0 CVE ID:CVE-2023-3249 **CVSS Score:**9.8 (Critical) Researcher/s: István Márton
Privilege Escalation
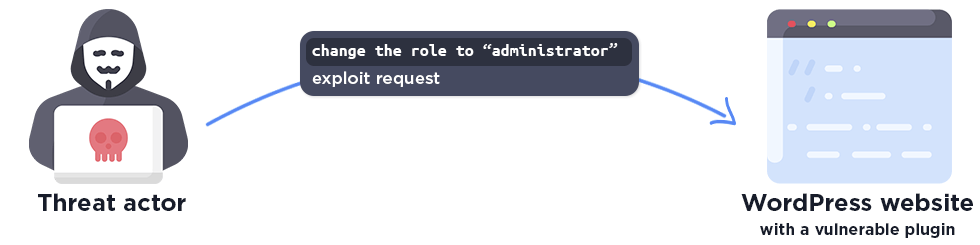
A privilege escalation vulnerability occurs when an attacker exploits weaknesses in user management, modifying a low-privileged account, such as a subscriber, to elevate it to a high-privileged account, effectively becoming an administrator. These vulnerabilities also make it easy for threat actors to completely compromise a vulnerable WordPress site, however, they typically require at least some form of access on the site in order for privileges to be elevated.
As shown, a single exploit request is typically enough for the attacker to gain administrator privileges on the website.
We found a total of 12 privilege escalation vulnerabilities in 2023. The more serious vulnerabilities, which can be exploited with low privileges, are listed below (11 out of 12 in total):
UserPro <= 5.1.4 - Authenticated (Subscriber+) Privilege Escalation
Plugin Slug: userpro Affected Versions:<= 5.1.4 CVE ID:CVE-2023-6009 **CVSS Score:**8.8 (High) Researcher/s: István Márton
Feather Login Page 1.0.7 - 1.1.1 - Missing Authorization to Authentication Bypass and Privilege Escalation
Plugin Slug: feather-login-page **Affected Versions:**1.0.7 - 1.1.1 CVE ID:CVE-2023-2545 **CVSS Score:**8.1 (High) Researcher/s: István Márton
OTP Login Woocommerce & Gravity Forms <= 2.2 - Authentication Bypass to Privilege Escalation
Plugin Slug: mobile-login-woocommerce Affected Versions:<= 2.2 CVE ID:CVE-2023-2706 **CVSS Score:**8.1 (High) Researcher/s: István Márton
ReviewX <= 1.6.13 - Arbitrary Usermeta Update to Authenticated (Subscriber+) Privilege Escalation
Plugin Slug: reviewx Affected Versions:<= 1.6.13 CVE ID:CVE-2023-2833 **CVSS Score:**8.8 (High) Researcher/s: István Márton
ProfileGrid <= 5.5.2 - Missing Authorization to Arbitrary Group Option Modification and Privilege Escalation
Plugin Slug: profilegrid-user-profiles-groups-and-communities Affected Versions:<= 5.5.2 CVE ID:CVE-2023-3714 **CVSS Score:**7.5 (High) Researcher/s: István Márton
WP Project Manager <= 2.6.4 - Arbitrary Usermeta Update to Authenticated (Subscriber+) Privilege Escalation
Plugin Slug: wedevs-project-manager Affected Versions:<= 2.6.4 CVE ID:CVE-2023-3636 **CVSS Score:**8.8 (High) Researcher/s: István Márton, Chloe Chamberland
BAN Users <= 1.5.3 - Missing Authorization to Authenticated (Subscriber+) Settings Update & Privilege Escalation
Plugin Slug: ban-users Affected Versions:<= 1.5.3 CVE ID:CVE-2023-4153 **CVSS Score:**8.8 (High) Researcher/s: István Márton
Real Estate Manager <= 6.7.1 - Arbitrary Usermeta Update to Authenticated (Subscriber+) Privilege Escalation
Plugin Slug: real-estate-manager Affected Versions:<= 6.7.1 CVE ID:CVE-2023-4239 **CVSS Score:**8.8 (High) Researcher/s: István Márton
Premium Packages - Sell Digital Products Securely <= 5.7.4 - Arbitrary User Meta Update to Authenticated (Subscriber+) Privilege Escalation
Plugin Slug: wpdm-premium-packages Affected Versions:<= 5.7.4 CVE ID:CVE-2023-4293 **CVSS Score:**8.8 (High) Researcher/s: István Márton
Donation Forms by Charitable <= 1.7.0.12 - Unauthenticated Privilege Escalation
Plugin Slug: charitable Affected Versions:<= 1.7.0.12 CVE ID:CVE-2023-4404 **CVSS Score:**9.8 (Critical) Researcher/s: István Márton
WP Data Access <= 5.3.7 - Authenticated (Subscriber+) Privilege Escalation
Plugin Slug: wp-data-access Affected Versions:<= 5.3.7 CVE ID:CVE-2023-1874 **CVSS Score:**7.5 (High) Researcher/s: Chloe Chamberland
Arbitrary File Upload
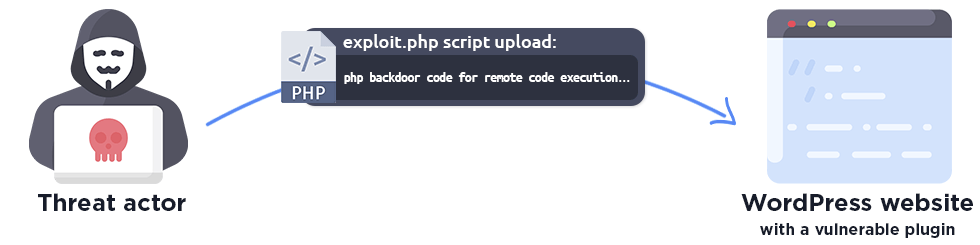
An arbitrary file upload vulnerability occurs when an attacker exploits weaknesses in file management, uploading a malicious php file that allows an attacker to execute remote code. These vulnerabilities also make it easy for threat actors to completely compromise a vulnerable WordPress site and are often a prime target for threat actors looking to upload malware and backdoors/webshells to maintain persistence.
As seen, also a single exploit request is enough for the attacker to upload a malicious php file to the website.
All Wordfence users, including Free, Premium, Care, and Response, are protected from exploits targeting this vulnerability type by default thanks to the Wordfence Firewall’s built-in Malicious File Upload protection, which makes use of a layered approach to detect and block malicious file uploads.
We found a total of 20 arbitrary file upload vulnerabilities in 2023. The more serious vulnerabilities, which can be exploited with low privileges, are listed below (9 out of 20 in total):
Go Pricing - WordPress Responsive Pricing Tables <= 3.3.19 - Improper Authorization to Arbitrary File Upload
Plugin Slug: go_pricing Affected Versions:<= 3.3.19 CVE ID:CVE-2023-2496 **CVSS Score:**7.1 (High) Researcher/s: István Márton
User Registration <= 3.0.2 - Authenticated (Subscriber+) Arbitrary File Upload
Plugin Slug: user-registration Affected Versions:<= 3.0.2 CVE ID:CVE-2023-3342 **CVSS Score:**9.9 (Critical) Researcher/s: István Márton
Drag and Drop Multiple File Upload - Contact Form 7 <= 1.3.7.3 - Unauthenticated Arbitrary File Upload
Plugin Slug: drag-and-drop-multiple-file-upload-contact-form-7 Affected Versions:<= 1.3.7.3 CVE ID:CVE-2023-5822 **CVSS Score:**8.1 (High) Researcher/s: István Márton
Paid Memberships Pro <= 2.12.3 - Authenticated (Subscriber+) Arbitrary File Upload
Plugin Slug: paid-memberships-pro Affected Versions:<= 2.12.3 CVE ID:CVE-2023-6187 **CVSS Score:**7.5 (High) Researcher/s: István Márton
Piotnet Forms <= 1.0.26 - Unauthenticated Arbitrary File Upload
Plugin Slug: piotnetforms Affected Versions:<= 1.0.26 CVE ID:CVE-2023-6220 **CVSS Score:**8.1 (High) Researcher/s: István Márton
MW WP Form <= 5.0.1 - Unauthenticated Arbitrary File Upload
Plugin Slug: mw-wp-form Affected Versions:<= 5.0.1 CVE ID:CVE-2023-6316 **CVSS Score:**9.8 (Critical) Researcher/s: István Márton
Unlimited Addons for WPBakery Page Builder <= 1.0.42 - Authenticated (Editor+) Arbitrary File Upload
Plugin Slug: unlimited-addons-for-wpbakery-page-builder Affected Versions:<= 1.0.42 CVE ID:CVE-2023-6925 **CVSS Score:**7.2 (High) Researcher/s: István Márton
Note: Contributors can also use the page builder depending on the plugin settings.
Essential Real Estate <= 4.3.5 - Authenticated (Subscriber+) Arbitrary File Upload
Plugin Slug: essential-real-estate Affected Versions:<= 4.3.5 CVE ID:CVE-2023-6827 **CVSS Score:**7.5 (High) Researcher/s: István Márton
Unlimited Elements For Elementor (Free Widgets, Addons, Templates) <= 1.5.66 - Authenticated (Contributor+) Arbitrary File Upload
Plugin Slug: unlimited-elements-for-elementor Affected Versions:<= 1.5.66 CVE ID:CVE-2023-3295 **CVSS Score:**8.8 (High) Researcher/s: Chloe Chamberland, and another researcher (duplicated)
Arbitrary File Deletion
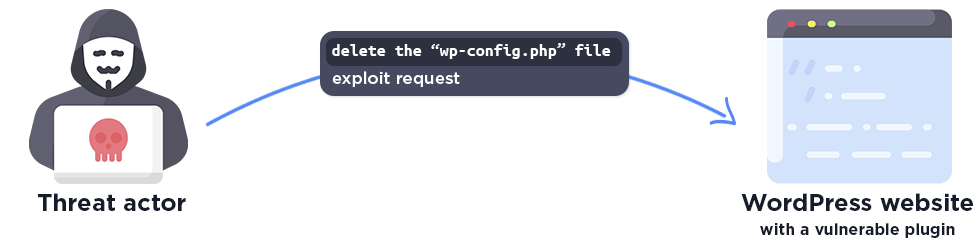
An arbitrary file deletion vulnerability occurs when an attacker exploits weaknesses in file management. This can be used to delete any file, however, attackers often target the wp-config.php in WordPress. Deleting the wp-config.php file allows an attacker to reset the installation and gain administrator access to the site by pointing it to a remote database under their control. This makes it possible to achieve remote code execution on the server. As such, these vulnerabilities also make it easy for threat actors to completely compromise a vulnerable WordPress site.
All Wordfence users, including Free, Premium, Care, and Response, are protected from exploits targeting this vulnerability type by default thanks to the Wordfence Firewall’s built-in Directory Traversal and Local File Inclusion protection.
We found a total of 1 arbitrary file deletion vulnerability in 2023.
AI ChatBot <= 4.8.9 and 4.9.2- Authenticated (Subscriber+) Arbitrary File Deletion via qcld_openai_delete_training_file
Plugin Slug: chatbot **Affected Versions:**4.9.2 - 4.9.2, <= 4.8.9 CVE ID:CVE-2023-5212 **CVSS Score:**9.6 (Critical) Researcher/s: Marco Wotschka, Chloe Chamberland
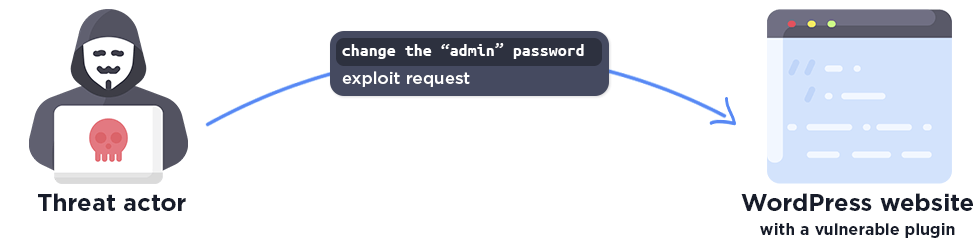
Arbitrary User Password Change
An arbitrary user password change vulnerability occurs when an attacker exploits weaknesses in user management, typically through an insecure direct object reference vulnerability, providing a specific value to modify the password of an 'admin' account instead of their attacker's own 'user' account. This can easily be used by attackers to take over administrative user accounts and further infect a victim.
As seen, a single exploit request is enough for the attacker to change the administrator password on the website.
We found a total of 7 arbitrary user password change vulnerabilities in 2023. The more serious vulnerabilities are listed below, which can also be exploited with low privileges (5 out of 7 in total):
WCFM Membership – WooCommerce Memberships for Multivendor Marketplace <= 2.10.7 - Unauthenticated Insecure Direct Object Reference to Arbitrary User Password Change
Plugin Slug: wc-multivendor-membership Affected Versions:<= 2.10.7 CVE ID:CVE-2023-2276 **CVSS Score:**9.8 (Critical) Researcher/s: István Márton
SP Project & Document Manager <= 4.67 - Authenticated (Subscriber+) Insecure Direct Object Reference to Arbitrary User Password Change
Plugin Slug: sp-client-document-manager Affected Versions:<= 4.67 CVE ID:CVE-2023-3063 **CVSS Score:**8.8 (High) Researcher/s: István Márton
LearnDash LMS <= 4.6.0 - Authenticated (Subscriber+) Insecure Direct Object Reference to Arbitrary User Password Change
Plugin Slug: sfwd-lms Affected Versions:<= 4.6.0 CVE ID:CVE-2023-3105 **CVSS Score:**8.8 (High) Researcher/s: István Márton
Simplr Registration Form Plus+ <= 2.4.5 - Authenticated (Subscriber+) Insecure Direct Object Reference to Arbitrary User Password Change
Plugin Slug: simplr-registration-form Affected Versions:<= 2.4.5 CVE ID:CVE-2023-4213 **CVSS Score:**8.8 (High) Researcher/s: István Márton
Directorist <= 7.5.4 - Authenticated (Subscriber+) Arbitrary User Password Reset to Privilege Escalation
Plugin Slug: directorist Affected Versions:<= 7.5.4 CVE ID:CVE-2023-1888 **CVSS Score:**8.8 (High) Researcher/s: Alex Thomas
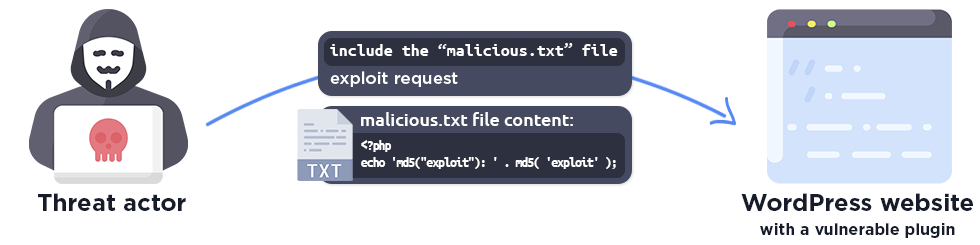
Local or Remote File Inclusion
A local file inclusion vulnerability occurs when an attacker exploits weaknesses in file management to include or execute arbitrary files on the server. Attackers once again often target wp-config.php, which contains database credentials and secret keys. A remote file inclusion vulnerability, on the other hand, allows remote code execution by directly allowing attackers to execute code from a remote site under their control.
All Wordfence users, including Free, Premium, Care, and Response, are protected from exploits targeting local file inclusion vulnerabilities thanks to the Wordfence Firewall’s built-in Directory Traversal and Local File Inclusion protection.
We found a total of 8 local or remote file inclusion vulnerabilities in 2023. The more serious vulnerabilities are listed below, which can also be exploited with low privileges (7 out of 8 in total):
Dropbox Folder Share <= 1.9.7 - Unauthenticated Local File Inclusion
Plugin Slug: dropbox-folder-share Affected Versions:<= 1.9.7 CVE ID:CVE-2023-4488 **CVSS Score:**9.8 (Critical) Researcher/s: Marco Wotschka
Canto <= 3.0.4 - Unauthenticated Remote File Inclusion
Plugin Slug: canto Affected Versions:<= 3.0.4 CVE ID:CVE-2023-3452 **CVSS Score:**9.8 (Critical) Researcher/s: Marco Wotschka
LWS Affiliation <= 2.2.6 - Unauthenticated Remote/Local File Inclusion
Plugin Slug: lws-affiliation Affected Versions:<= 2.2.6 CVE ID:CVE-2023-32297 **CVSS Score:**9.8 (Critical) Researcher/s: Marco Wotschka, and another researcher (duplicated)
WP Directory Kit <= 1.1.9 - Unauthenticated Local File Inclusion via wdk_public_action
Plugin Slug: wpdirectorykit Affected Versions:<= 1.1.9 CVE ID:CVE-2023-2278 **CVSS Score:**9.8 (Critical) Researcher/s: István Márton
PHP to Page <= 0.3 - Authenticated (Subscriber+) Local File Inclusion to Remote Code Execution via Shortcode
Plugin Slug: php-to-page Affected Versions:<= 0.3 CVE ID:CVE-2023-5199 **CVSS Score:**9.9 (Critical) Researcher/s: István Márton
Grid Plus <= 1.3.3 - Authenticated (Subscriber+) Local File Inclusion via Shortcode
Plugin Slug: grid-plus Affected Versions:<= 1.3.3 CVE ID:CVE-2023-5199 **CVSS Score:**8.8 (High) Researcher/s: István Márton
HTML filter and csv-file search <= 2.7 - Authenticated (Contributor+) Local File Inclusion via Shortcode
Plugin Slug: hk-filter-and-search Affected Versions:<= 2.7 CVE ID:CVE-2023-5099 **CVSS Score:**8.8 (High) Researcher/s: Alex Thomas
Remote Code Execution
The remote code execution vulnerability occurs when an attacker is able to execute arbitrary remote code on the server. This can be used by attackers to upload malware, maintain persistence, and further compromise the victim’s server.
We found a total of 5 remote code execution vulnerabilities in 2023. The more serious vulnerabilities are listed below, which can also be exploited with low privileges (3 out of 5 in total):
Allow PHP in Posts and Pages <= 3.0.4 - Authenticated (Subscriber+) Remote Code Execution via Shortcode
Plugin Slug: allow-php-in-posts-and-pages Affected Versions:<= 3.0.4 CVE ID:CVE-2023-4994 **CVSS Score:**9.9 (Critical) Researcher/s: István Márton
OpenHook <= 4.3.0 - Authenticated (Subscriber+) Remote Code Execution via Shortcode
Plugin Slug: thesis-openhook Affected Versions:<= 4.3.0 CVE ID:CVE-2023-5201 **CVSS Score:**9.9 (Critical) Researcher/s: István Márton
Ads by datafeedr.com <= 1.1.3 - Unauthenticated (Limited) Remote Code Execution
Plugin Slug: ads-by-datafeedrcom Affected Versions:<= 1.1.3 CVE ID:CVE-2023-5843 **CVSS Score:**9.0 (Critical) Researcher/s: István Márton
Final Summary
All of the vulnerabilities we discovered and documented in 2023 were easily exploitable high impact vulnerabilities that required no user interaction. They were all prime targets for attackers, and we are glad we were able to work with the vendors to get these issues patched before attackers could find them.
Due to the unique nature of many of these vulnerabilities, a new firewall rule is required in almost every case to protect against them. That is one of the reasons we strongly recommend running a WordPress-specific web application firewall like Wordfence on your WordPress site.
More Vulnerabilities Found in 2023
We didn’t stop there, over the year 2023 we found several other vulnerabilities and worked with vendors to get them patched. You can read more about these vulnerability types and what we discovered below.
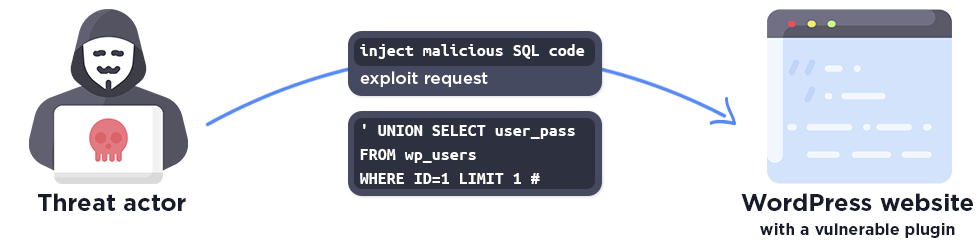
SQL Injection
A SQL injection vulnerability occurs when an attacker is able to inject arbitrary SQL code into a SQL statement. This is often used to exfiltrate sensitive data like password hashes from the database.
We found more than 30 SQL injection vulnerabilities in 2023.
All Wordfence users, including Free, Premium, Care, and Response, are protected from exploits targeting this vulnerability thanks to the Wordfence Firewall’s built-in SQL Injection protection.
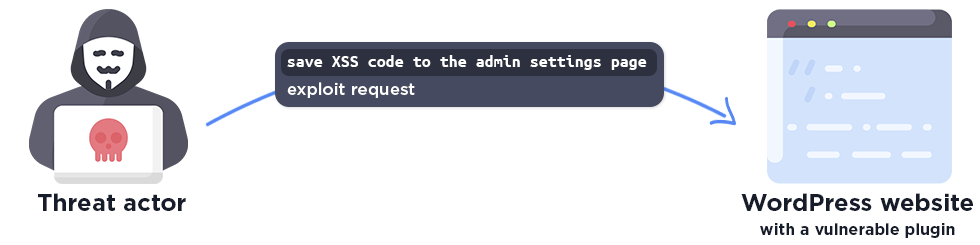
Stored Cross-Site Scripting (XSS)
A stored Cross-Site Scripting vulnerability occurs when an attacker is able to store the exploit payload, often malicious JavaScript, on the website.
The stored malicious code may only load on a specific admin settings page. This means that the attacker has to wait until the victim, in the most serious cases an administrator, opens the affected admin page.
This is a much more complicated attack, it requires preparation and the attacker has to wait for the victim, but the impact can be critical.
It may happen that the malicious script is stored on a public and easily accessible page, even on the home page, but this is the rarest case.
As with all XSS vulnerabilities, a malicious payload could be used to perform actions as an administrator, including adding new malicious administrator users to the site and embedding backdoors in plugin and theme files, as well as redirecting users to malicious sites.
We found a total of more than 170 stored cross-site scripting vulnerabilities in 2023.
Highlighting Alex Thomas's research, who found unauthenticated stored cross-site scripting vulnerabilities in a total of 14 email plugins.
Title: Multiple WordPress Plugins – Unauthenticated Stored Cross-Site Scripting via Email **CVSS Score:**7.2 (High) Researcher/s: Alex Thomas
Highlighting the Wordfence Threat Intelligence team's research, where we found shortcode-based stored cross-site scripting vulnerabilities in more than 100 plugins.
Title: Multiple WordPress Plugins – Contributor+ Stored Cross-Site Scripting via Shortcode **CVSS Score:**6.4 (Medium) Researcher/s: István Márton, Alex Thomas
All Wordfence users, including Free, Premium, Care, and Response, are protected from exploits targeting this vulnerability thanks to the Wordfence Firewall’s built-in Cross-Site Scripting protection.
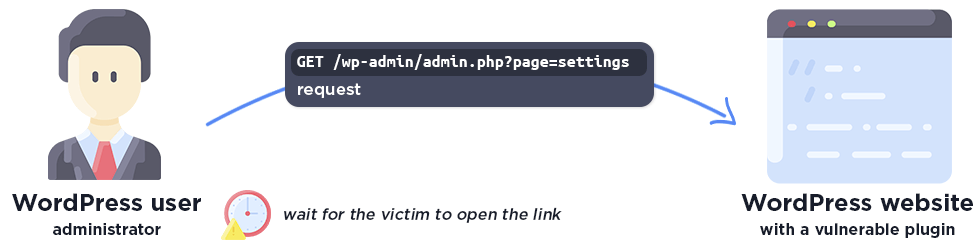
Reflected Cross-Site Scripting (XSS)
A Reflected Cross-site Scripting vulnerability occurs when an attacker exploits improper escaping and sanitization in an URL parameter, crafting a specific link that contains the XSS payload.
The attacker must wait for the victim to open the link. This XSS type generally involves some degree of social engineering in order to be successful and it’s worth noting that the payload is never stored on the server so the chance of success relies on the initial interaction with the user.
All Wordfence users, including those using Wordfence Free, Premium, Care, and Response, are protected from exploits targeting this type of vulnerability thanks to the Wordfence Firewall’s built-in Cross-Site Scripting protection.
Cross-Site Request Forgery (CSRF)
A Cross-Site Request Forgery makes it possible for attackers to forge requests on behalf of a site administrator, when there is a lack of a nonce check in the vulnerable function.
This was one of the most common vulnerability types disclosed in 2023.
The attacker must trick a victim into clicking on a link. The impact can vary widely, ranging from trivial to very serious, depending on the vulnerable code.
We often don't focus on CSRF during our research because it’s not likely to be exploited en masse due to the unique nature of CSRF. This is fortunate, as it is impractical to defend against CSRF vulnerabilities with a Web Application Firewall.
Conclusion
We hope to provide some insight into our research efforts with the 2023 Wordfence Critical Vulnerability Research in Review, highlighting the most impactful vulnerabilities and detailing how we protect our customers from potential threats.
We express our gratitude to the talented independent researchers working to make the WordPress ecosystem more secure and hope that our own internal efforts and our Bug Bounty Program motivates them to find the most impactful vulnerabilities so that they can be responsibly disclosed. Together, we can accomplish far more than our individual efforts.
Join the Bug Bounty Program today! https://www.wordfence.com/threat-intel/researcher-register
The post 2023's Critical WordPress Vulnerabilities and How They Work appeared first on Wordfence.
9.9 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
0.238 Low
EPSS
Percentile
96.5%