
Five Eyes Alliance Advisory & Using Threat Intelligence

Trellix Global Defenders: Five Eyes Alliance Advisory and Using Threat Intelligence to Protect Against Future Attacks
By Taylor Mullins · May 6, 2022
Evolving intelligence continues to indicate that the Russian government is exploring options to launch cyberattacks in retaliation against governments that have assisted Ukraine or levied sanctions against Russia. In addition, threat groups that have sworn loyalty to Russia are continually seeking opportunities to attack large organizations and critical infrastructure. Due to the continued risk, an advisory from the Five Eyes Intelligence Oversight and Review Council (FIORC) which includes the intelligence alliances compromising of the United States, Australia, Canada, New Zealand, and the United Kingdom has been released outlining the threat groups at play and mitigations to proactively protect against being a victim.
CISA Alert: Russian State-Sponsored and Criminal Cyber Threats to Critical Infrastructure
Trellix is continuing to monitor the threat activity impacting the Ukrainian region and adding protections to our products for newly discovered malware variants and APT activities. Trellix recommends for organizations to continue adopting a heightened security posture to protect against current and future threats that could target their environment. Government agencies such as the CISA are providing guidance as part of Shields Up to help organizations assess their infrastructure.
<https://www.cisa.gov/shields-up>
Along with adopting the guidance from the CISA and Five Eyes alliance, Trellix would like to provide additional information and resources that could assist organizations with being prepared should they be targeted.
Keeping the Doors Locked – Continuing with a Heightened Posture
Trellix recommends reviewing the information provided by the CISA along with the items noted below to proactively prevent Initial Access in your environment.
- Reviewing the CVEs for all Public Facing Systems – CISA regularly updates and maintains a full list of CVEs that are known to be exploited: CISA: KNOWN EXPLOITED VULNERABILITIES CATALOG
- Over 90% of successful cyber-attacks begin with a phishing email, it is critical to continually monitor for spearphishing campaigns with malicious attachments and links.
- Communication – Along with monitoring, educating end users on what they could be receiving in their email can help them spot phishing campaigns before they click or download.
- Disabling all ports and protocols that are not essential, especially anything related to remote services.
- If Remote Desktop Protocol is used, limit access and utilize authentication mechanisms
- Enable multifactor authentication (MFA) for all users, without exception.
- Secure and utilize least privilege for account credentials, in previous attacks Russian APT actors have utilized this technique to maintain persistence.
- Implement time-based access for privilege accounts, i.e., do not allow usage on holidays or weekends.
- Performing an assessment of your Active Directory accounts and permissions is an initiative-taking measure to prevent adversaries from using stale credentials.
- Review security configurations for Cloud Services to prevent breaches, CISA: Strengthening Security Configurations to Defend Against Attackers Targeting Cloud Services
- Conduct regular endpoint security scans of IT assets using up-to-date signatures to detect any malicious files that have been staged.
Assessing who still has access to your environment
Often organizations grant credentials with elevated rights into their environment to contractors, temporary employees, or outside vendors for projects or engagements that are active for months or even years once the engagement ends. Performing an assessment of your Active Directory accounts and permissions is one initiative-taking measure to prevent adversarial activity using stale credentials.
The same can be done for external network connections, large organizations will often allow third party customers, vendors, partners, or suppliers to have remote access into their environment to perform specific tasks. As was seen in the Lapsus$ breaches, if an attacker cannot find entry into their desired target, they will at times look at which entities might have access into the company and look to hack the third party to gain access via their allowed connection. Auditing who has remote access into your environment and the cybersecurity posture, frameworks, and controls of third-party solution providers is highly recommended.
Resources for Threat Intelligence and Detection
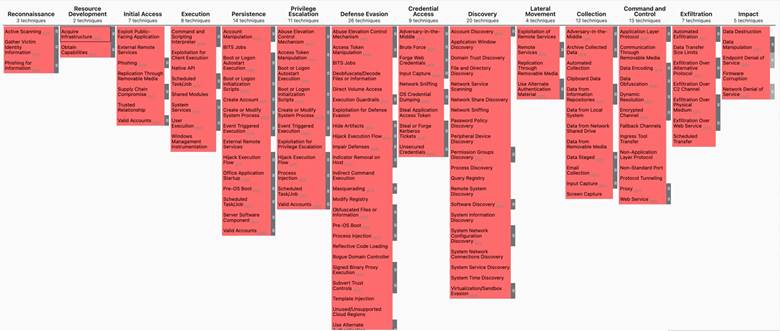 Figure 1. MITRE Framework for tactics and techniques specific to well-known to Russian APT groups.
Figure 1. MITRE Framework for tactics and techniques specific to well-known to Russian APT groups.
Vishwas Manral, Chief Architect from the Skyhigh Security Cloud team, and founder of NanoSec has created the above MITRE Framework based on tactics and techniques well known to APT groups out of Russia, also techniques identified with the software they use. Vishwas has made this MITRE Framework available in both json and xlsx format on the following GitHub site.
GitHub: MITRE ATT&CK MATRIX for Russian APT Groups.
The Trellix Advanced Threat Research Team has created a GitHub repository of aggregated Yara rules from various public sources, including our own, and make it available to organizations and individuals alike, to help combat these emerging threats.
<https://github.com/advanced-threat-research/Russian_CyberThreats_Yara>
The Trellix AC3 maintains a Threat Sightings site that notes tools are being used in attacks, this information is meant to assist Blue Teamers to generate actionable countermeasures. Among the information that a threat sighting may note is full command lines, API Calls, file system activity, network activity, etc.
The SANS Resource Center has outlined specific action items of consideration specific to the Russian/Ukraine Activity. This site from SANS can be used as a framework for security operations and provides guidance for CISOs on reporting to executives and board members.
SANS: Ukraine-Russia Conflict – Cyber Resource Center
Trellix Protections and Observed Activity
Trellix is currently monitoring threats detected and reported across the threat landscape, this is a fluid situation that is ever changing. Trellix will continue to add protections to all our products and alert customers as these threats are discovered. Below is an overview of how to utilize threat intelligence for knowing who may be targeting your sectors and the tools utilized by specific APT and threat groups to assist with early detection of malicious activity.
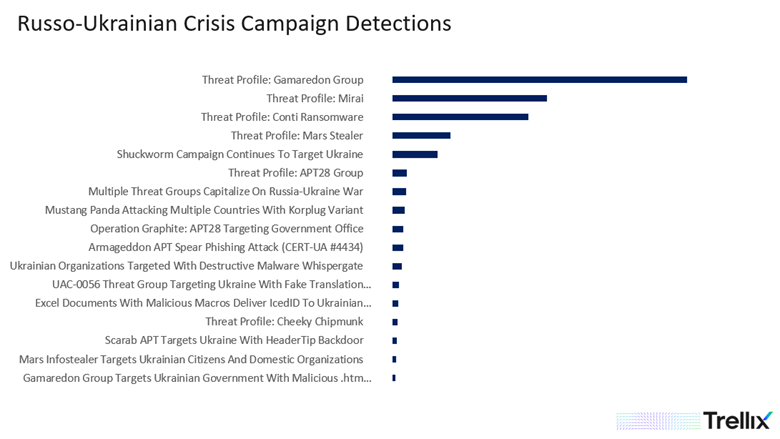 Figure 2. Russo-Ukrainian Crisis Threat Campaign Detections for the past 30 days. Source: Trellix APG Team
Figure 2. Russo-Ukrainian Crisis Threat Campaign Detections for the past 30 days. Source: Trellix APG Team
Utilizing Threat Intelligence for Event Correlations
One key area that can assist with initiative-taking detection and protection is correlating threat intelligence and Indicators of Compromise (IOCs) from MVISION Insights against event data within your organization. Customers of MVISION Insights can utilize the published APIs in MVISION API to pull down Campaigns, Indicators of Compromise (IOCs), and Tactics, Techniques, and Procedures (TTPs) into their environment to further correlate data and proactively detect threats. MVISION Insights regularly updated with campaigns and IOCs related to the threats related to the conflict in the Ukrainian region and the threat actors that are targeting outside entities as retaliation.
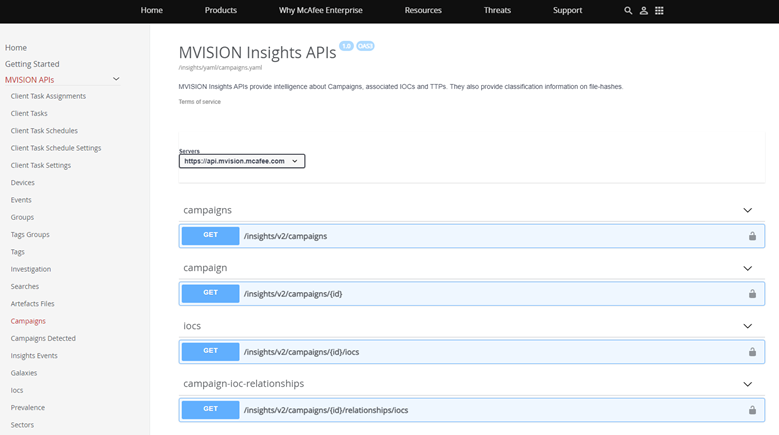 Figure 3. MVISION Insights APIs to access Campaigns, IOCs, and TTPs for added threat intelligence and correlation
Figure 3. MVISION Insights APIs to access Campaigns, IOCs, and TTPs for added threat intelligence and correlation
What Threat Group Could Be Targeting Your Sector
Part of the challenge of defending against the growing threats is knowing who might be targeting your sector and the techniques used to gain initial access and the techniques utilized by the adversary should they gain entry. The joint advisory noted above from the CISA provides an overview of the active threat groups and the sectors they are known to target.
In addition to the joint government advisory, MVISION Insights has added the “Russo-Ukrainian Crisis” label to all campaigns and threat profiles in MVISION Insights to help identify specific threats related to the conflict and utilizing the Campaign Connections can assist customers with filtering to the threats that are being seen in a specific sector.
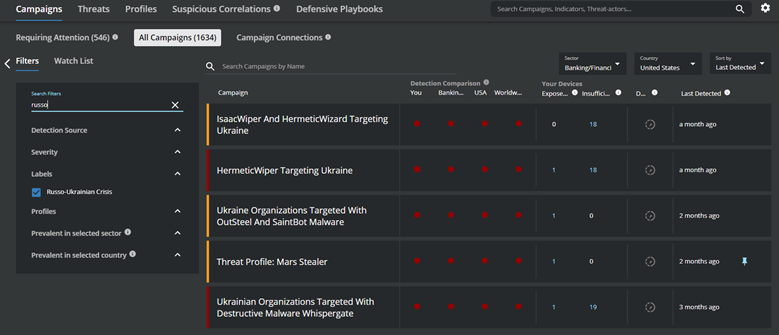 Figure 4. Filtering campaigns to those involved with the Russo-Ukrainian Crisis in MVISION Insights
Figure 4. Filtering campaigns to those involved with the Russo-Ukrainian Crisis in MVISION Insights
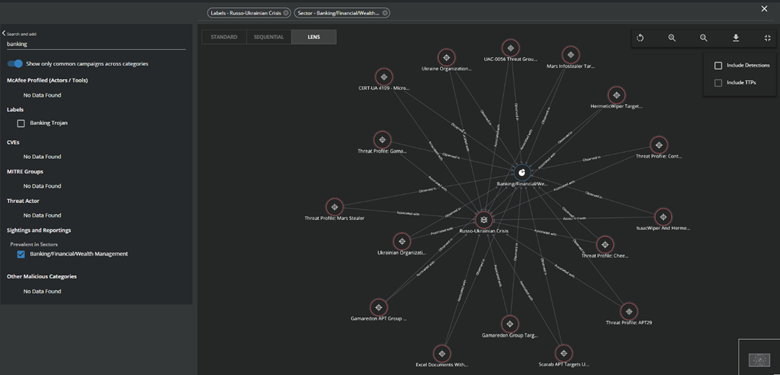 Figure 5. Graphical view of Russo-Ukrainian campaigns targeting specific sectors in MVISION Insights
Figure 5. Graphical view of Russo-Ukrainian campaigns targeting specific sectors in MVISION Insights
Knowing the Adversarial Tools and Their Usage
Ransomware gangs and APT groups often have a specific toolset that they utilize across their attacks, these tools can consist of open source and living off the land techniques. Being aware of these toolsets and monitoring for their usage in your environment can be an early indicator of adversarial activity if the usage of the tools is not known to be used for business purposes.
Below is an overview of common tools utilized by APT groups and ransomware gangs that have targeted entities across the Globe, hunting for the non-business usage of these tools can help with identifying emerging threats in your environment.
- Advanced IP Scanner is a free network scanner to analyze LAN. The program shows all network devices, gives you access to shared folders, provides remote control of computers (via RDP and Radmin), and can even remotely switch computers off.
- RCLONE is a command line utility used to synchronize cloud storage. Threat Groups have used RCLONE to aid in the exfiltration of sensitive data. Presence of RCLONE in a network can be an indication of un-authorized data exfiltration.
- UltraVNC is a powerful, easy to use and free - remote pc access software - that can display the screen of another computer (via internet or network) on your own screen. The program allows you to use your mouse and keyboard to control the other PC remotely. It means that you can work on a remote computer, as if you were sitting in front of it, right from your current location.
- AdFind is a Command line Active Directory query tool. Mixture of ldapsearch, search.vbs, ldp, dsquery, and dsget tools with other features. AdFind is a lightweight Active Directory enumeration tools often used by Threat groups once they are on a victims’ network. The tool itself is not malicious but an unexpected detection of AdFind can be an early indication of a network intrusion.
- Active Directory Explorer (AD Explorer) is an advanced Active Directory (AD) viewer and editor. You can use AD Explorer to easily navigate an AD database, define favorite locations, view object properties and attributes without having to open dialog boxes, edit permissions, view an object’s schema, and execute sophisticated searches that you can save and re-execute. AD Explorer also includes the ability to save snapshots of an AD database for off-line viewing and comparisons. When you load a saved snapshot, you can navigate and explore it as you would a live database. If you have two snapshots of an AD database you can use AD Explorer’s comparison functionality to see what objects, attributes and security permissions changed between them.
- USBStealer is malware that has used by Russian APT groups since at least 2005 to extract information from air-gapped networks. It does not have the capability to communicate over the Internet and has been used in conjunction with ADVSTORESHELL.
- AnyDesk is a remote desktop application distributed by AnyDesk Software GmbH. The proprietary software program provides platform independent remote access to personal computers and other devices running the host application.
- Wget is a free software package for retrieving files using HTTP, HTTPS, FTP and FTPS, the most widely used Internet protocols. It is a non-interactive command line tool, so it may easily be called from scripts, cron jobs, terminals without X-Windows support, etc.
- SharpView is a .NET port of PowerView and offers the ability to use any of the PowerView functions and arguments in a .NET assembly.
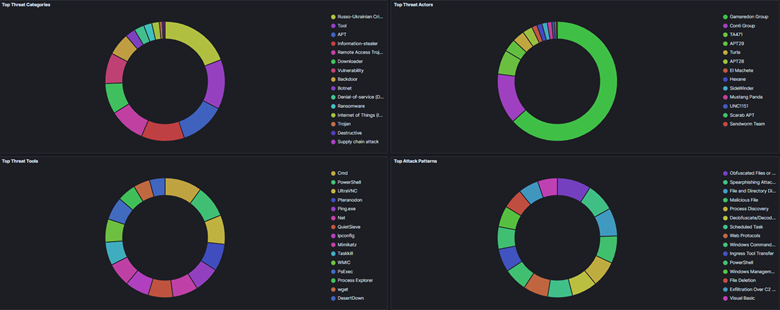 Figure 6. Graphical view of Russo-Ukrainian threat activity for the past 90 days. Source: Trellix APG Team
Figure 6. Graphical view of Russo-Ukrainian threat activity for the past 90 days. Source: Trellix APG Team
Additional Resources
Alert (AA22-057A) - Destructive Malware Targeting Organizations in Ukraine
Trellix Advanced Threat Research Team: Looking over the nation-state actors’ shoulders: Even they have a difficult day sometimes
Trellix Global Defenders: Cyberattacks Targeting Ukraine and HermeticWiper Protections
Trellix Advanced Threat Research Team: Return of Pseudo Ransomware
Conti Leaks: Examining the Panama Papers of Ransomware
Conti Group Targets ESXi Hypervisors With its Linux Variant
Ukrainian Companies Targeted by Wipers - Impact & Prevention