
CVE-2023-38831: Navigating the Threat Landscape of the Latest Security Vulnerability
8.5 High
AI Score
Confidence
High
CVE-2023-38831: Navigating the Threat Landscape of the Latest Security Vulnerability
By Neeraj Kumar Singh · November 09, 2023
Executive Summary
In August 2023, WinRAR released a security patch to address a remote code execution vulnerability in WinRAR’s ZIP archive. The vulnerability, known as CVE-2023-38831, was discovered and reported to RARLabs by a Group-IB Threat Intelligence researcher. This remote code execution vulnerability is creating buzz in the industry, since this vulnerability is used to deliver malware such as DarkMe, GuLoader, and Remcos RAT (Remote Access Trojan), etc in the form of benign archives.
The WinRAR archive comprise of any file type and a directory sharing the same name. Inside the directory, there could be a malicious executable file. When a user clicks on the file, a spoofed file within the directory is triggered and executed.
This capability can be particularly useful under certain vulnerability exploitation scenarios, such as when threat actor tries to deliver the malware, RAT and backdoor. Exploiting such a vulnerability is very easy because threat actor just needs to send the malicious archives as innocuous and once a user tries to view the file, exploitation occurs. In this exploitation scenario, an attacker can leverage a RAR file containing an exploit of this vulnerability to obtain remote code execution. Furthermore, when this vulnerability is combined with other vulnerabilities, it becomes possible to compromise the entire infrastructure of the target entity. Due to the presence of multiple vulnerabilities in WinRAR, threat actors are now exploiting additional WinRAR vulnerabilities and uploading fake exploits, such as CVE-2023-40477, to conceal the delivery of VenomRAT to the target.
Alternative utilization of this vulnerability occurred in the “Steal-it” campaign carried out by APT28. APT28, also known as Fancy Bear, is suspected to be behind the Steal-it campaign targeting organisations in Australia, Poland, and Belgium. In this campaign, LNK files concealed in ZIP archives are used to gain initial access, while sensitive information is exfiltrated via mocky API’s to Mockbin. The data leaked by the campaign includes NTLMv2 hashes, system information and geo-location.
In this blog post, we will take a deep dive into the technical details of CVE-2023-38831 and discuss the exploitation method. Additionally, we will examine how the security patch released by RARLabs fixes this issue. In response to the reported vulnerability, RARLabs released an update in 6.23 beta. Subsequently, to fix the vulnerability officially they released WinRAR 6.23 as well.
Introduction
WinRAR is a popular file archiver utility which can be used in multiple operating systems like Windows, Linux, macOS, etc. It is primarily used for compressing files and folders into a single compressed archive file, which can have the .rar file extension. WinRAR supports a variety of compression formats, including its proprietary RAR format as well as other common formats like ZIP, 7-Zip, and more.
There have been many instances in the past where WinRAR vulnerability has been used to deliver malware. In 2019 there was a vulnerability in the ACE (Advanced Correlation Engine) archive in which the attacker could create files in an arbitrary location during unpacking the ACE archive. WinRAR had to drop support for that file format in response. Another vulnerability in WinRAR is CVE-2023-40477, which is being used by threat actors to spread RAT to the cyber security research community. Also, there are many reports and news where CVE-2023-38831, a critical vulnerability known for being easy to exploit, has being used to spread DarkMe malware as well.
Among the various file formats that WinRAR can handle, it also has support for zip archives. This format is connected to the security vulnerability. All zip archives follow a fixed structure as shown below:
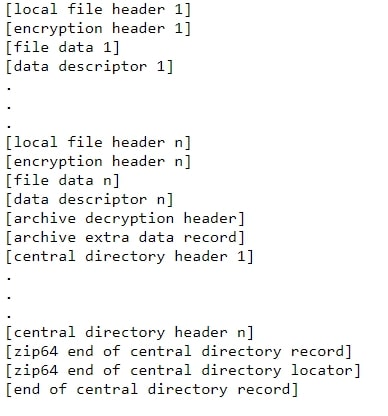 Figure 1: ZIP file structure
Figure 1: ZIP file structure
The Central Directory Header stores details about a single file and tells you where to find the Local File Header for that file. Together, these headers create the Central Directory, which helps quickly list all files in the archive. The Central Directory Header has the below syntax:
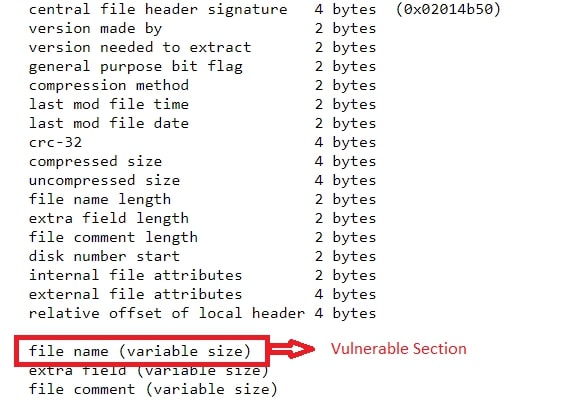 Figure 2: Central Directory Header structure
Figure 2: Central Directory Header structure
For more detailed information on zip archive structure, please visit this link.
Vulnerability Analysis
Overview
In this section, we will delve into the intricate workings of this vulnerability. We will explore how, merely by viewing a file, one can discern its susceptibility to causing remote code execution.
The vulnerability initiates when a user receives a seemingly harmless file that contains both a file and a directory with identical names within the same archive. When the application endeavours to access the file, it triggers an exception, leading to the extraction of the file into a temporary directory within the Windows operating system. Prior to the extraction process, the application transmits the absolute path of the file to the Windows API, while concurrently purging it of spaces and special characters. Once the file has been sanitized, the application endeavours to open what is believed to be the intended file. However, when this fails, it embarks on a path without spaces, unwittingly executing a potentially malicious file. This sequence of events culminates in the attacker achieving remote code execution.
Let us first see how the innocuous file looks like:
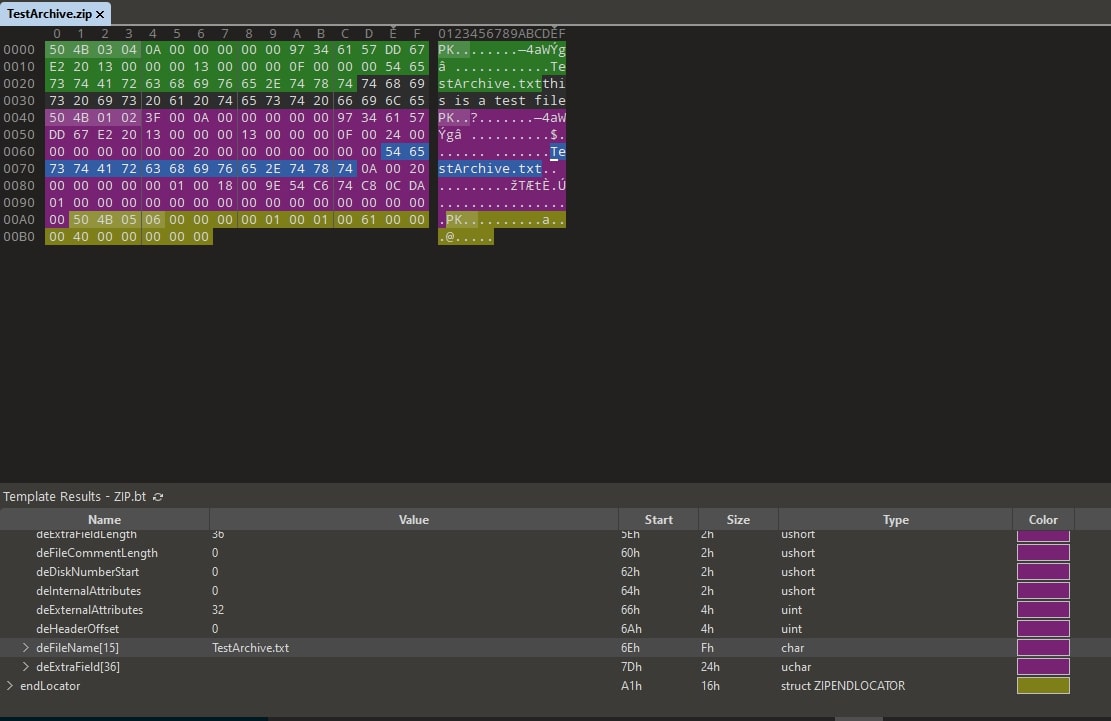 Figure 3: Innocuous ZIP file
Figure 3: Innocuous ZIP file
As can be observed, the central directory header’s filename field is “TestArchive.txt.” This is the test file we created to showcase a normal structure in the ZIP archive here we can observe that there is no extra space in the dirFileName field.
Next, we will examine a POC file.
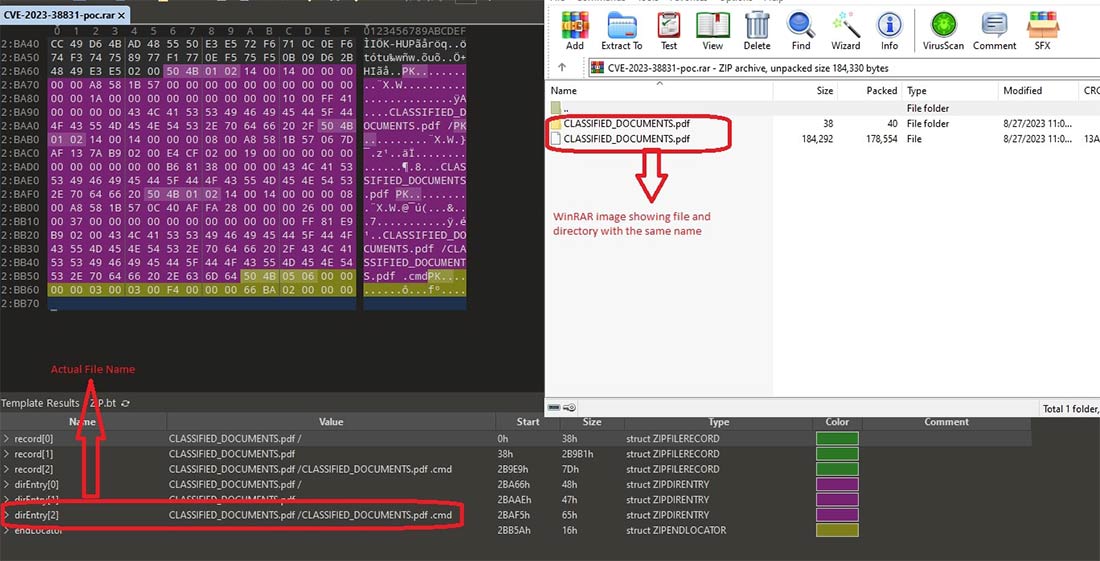 Figure 4: Malicious ZIP file
Figure 4: Malicious ZIP file
As can be observed from Figure 4, that malicious archive has 1 directory and 1 file, both with the same name, i.e., “CLASSFIED_DOCUMENTS.pdf”, visible in the WinRAR GUI. But the malicious filename, “CLASSFIED_DOCUMENTS.pdf .cmd”, and this file is present inside the directory. If you find this kind of structure where there is a file present having double extension or space that could be a malicious file. For demonstration purpose we have shown cmd there could be any other file like lnk, bat, ps1 and many more.
When a user double-clicks on the “CLASSFIED_DOCUMENTS.pdf” file in WinRAR, an internal function WinRAR.exe+sub_C91C40 is called to match the clickedFileName with dirEntryName.
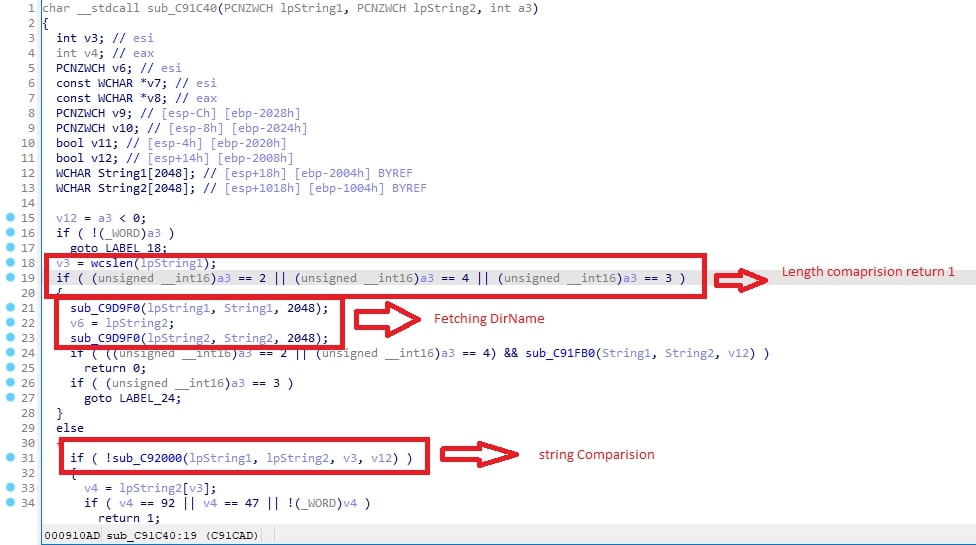 Figure 5: Disassembled view of sub_C91C40
Figure 5: Disassembled view of sub_C91C40
Once that matching is done, the filename is checked for the presence of \x2f and \x5C and null at loc_7F2F80.
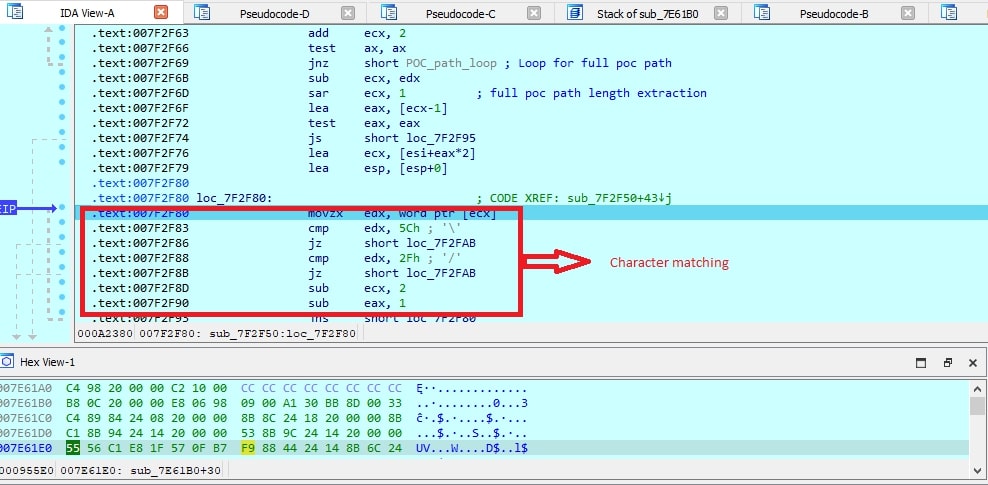 Figure 6: Character matching
Figure 6: Character matching
The same can be observed with decompiled code.
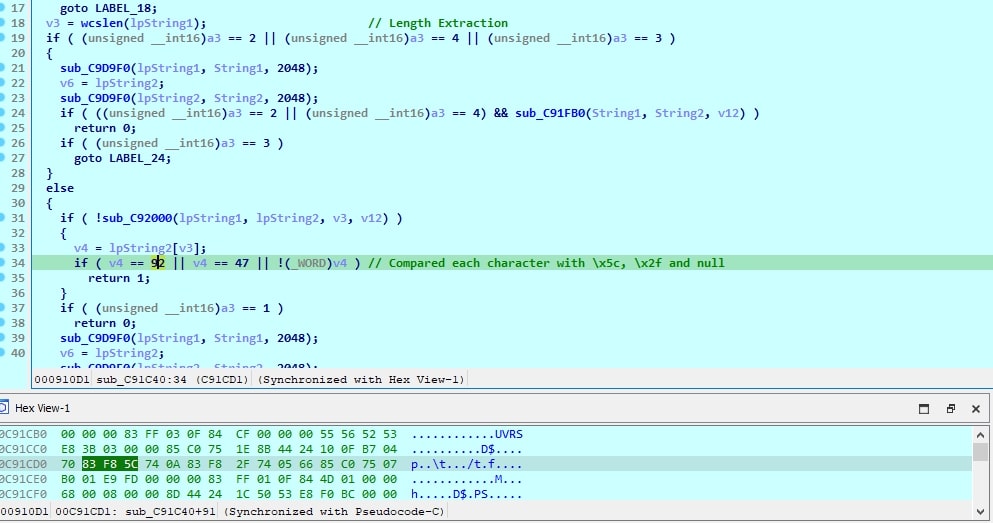 Figure 7: Hex value character check
Figure 7: Hex value character check
Below is the image showing characterwise matching in the filename.
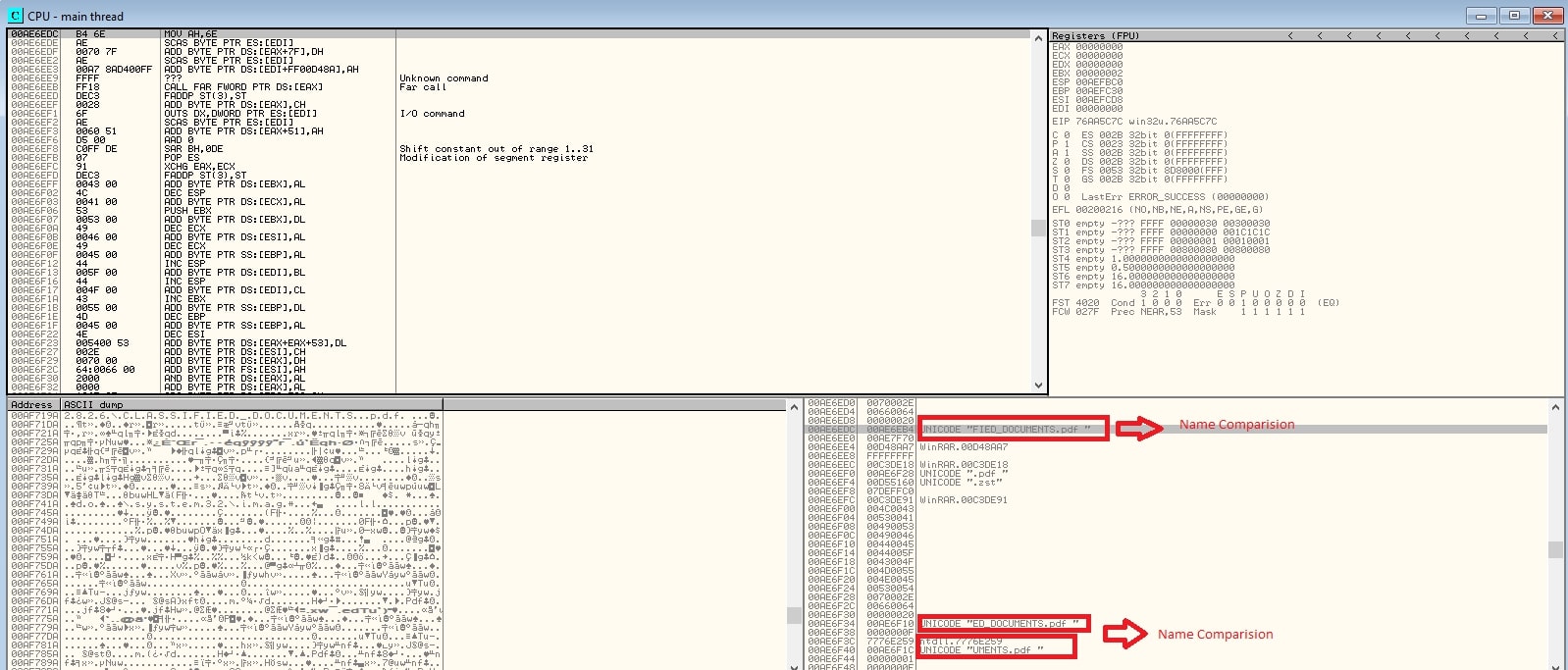 Figure 8: Name comparison
Figure 8: Name comparison
Later the file is extracted from the ZIP archive, and since there is a spoofed PDF file with the same name in the directory, it is also extracted to a temporary location within the “Rar$DIa2204.2826” folder.
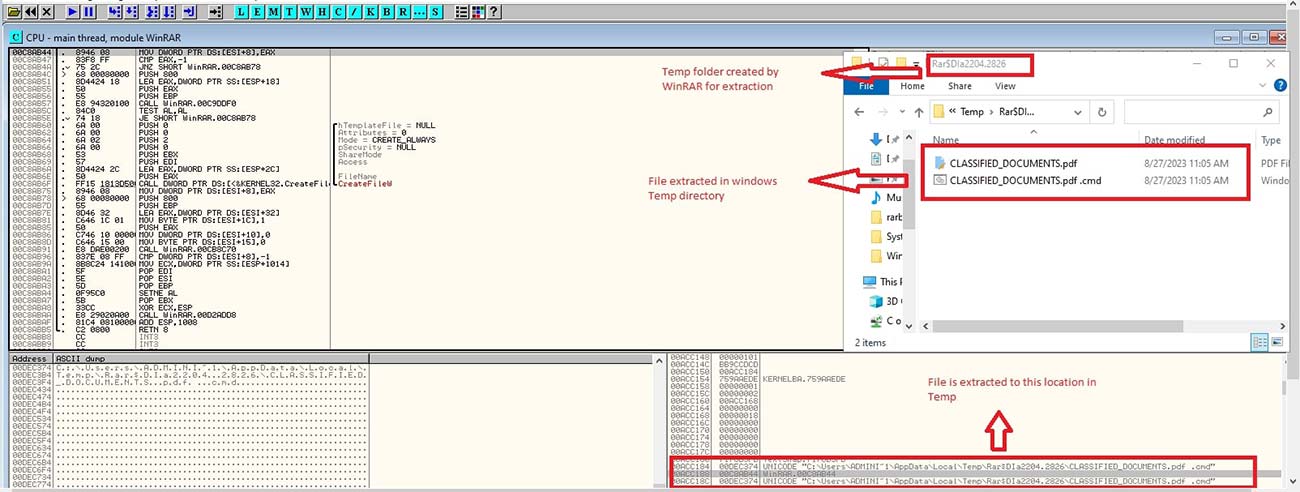 Figure 9: File extraction in temp folder
Figure 9: File extraction in temp folder
Later a Windows API (Application Programming Interface) ShellExecuteExW() is invoked, using the absolute path “C:\Users\ADMINI~1\AppData\Local\Temp\Rar$DIa2204.2826\CLASSIFIED_DOCUMENTS.pdf“ as the input for the file name, accounting for spaces.
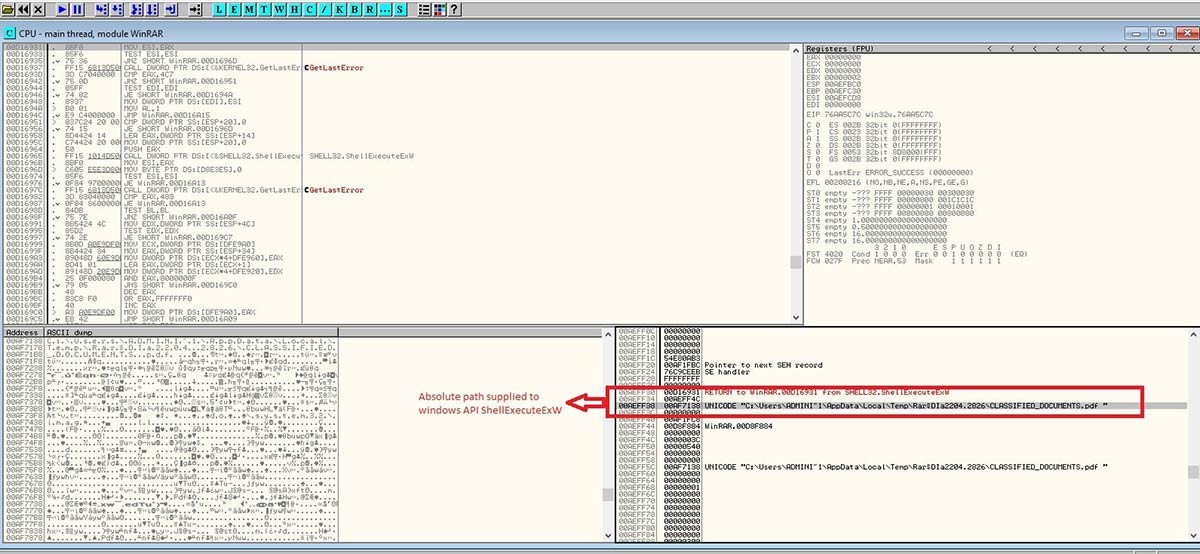 Figure 10: API execution with absolute file path
Figure 10: API execution with absolute file path
Later when we decompiled the function WinRAR.exe+sub_C0FC30, we observed the usage of registry and API. Finally, in line 110 file execution happens.
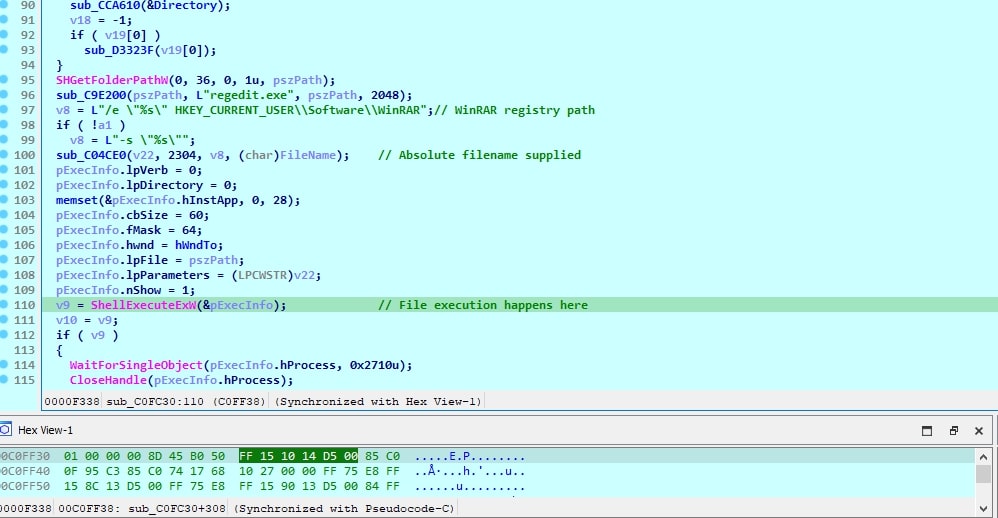 Figure 11: File execution
Figure 11: File execution
Prior to providing the absolute path to the ShellExecuteExW() API, both paths are submitted to the WinRAR.exe+sub_C9E2E0 function. This function examines the paths for the presence of blank spaces and various other characters. If it encounters a space in the filename, it eliminates it and then forwards the modified file path to the Windows API ShellExecuteExW().
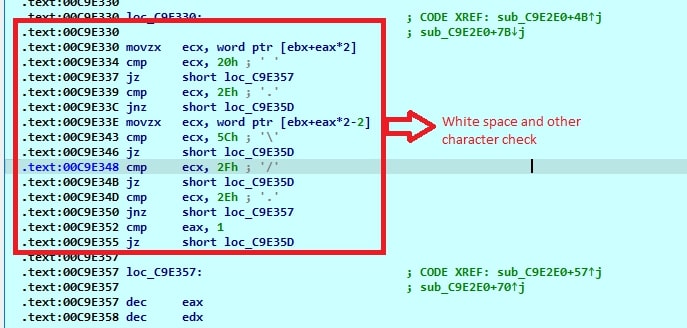 Fig 12: Disassembled WinRAR.exe+sub_C9E2E0
Fig 12: Disassembled WinRAR.exe+sub_C9E2E0
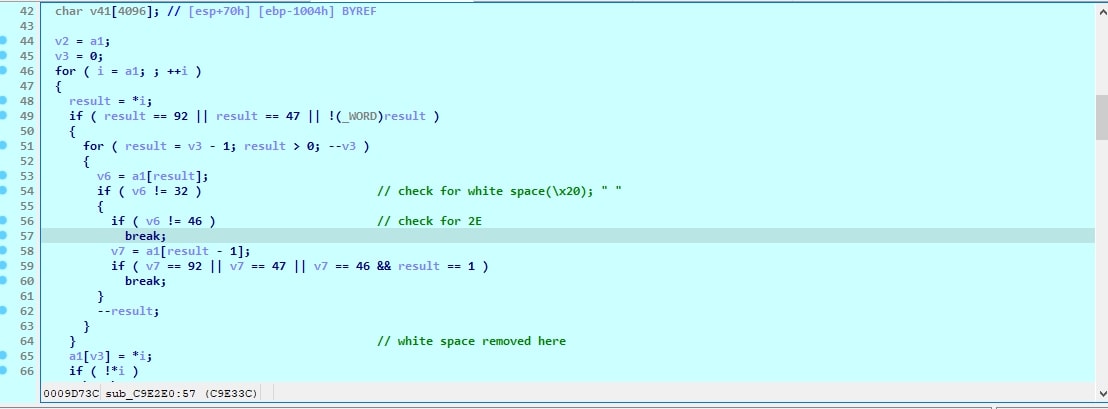 Fig 13: Decompiled WinRAR.exe+sub_C9E2E0
Fig 13: Decompiled WinRAR.exe+sub_C9E2E0
As both files reside within the same Temp directory, when a user double-clicks on the PDF file, WinRAR attempts to open the PDF. However, this attempt fails and results in an exception. Since the other file is also located in the same directory, the path
“C:\Users\ADMINI~1\AppData\Local\Temp\Rar$DIa2204.2826\CLASSIFIED_DOCUMENTS.pdf.cmd” which lacks spaces, is provided to the API, leading to the unintended execution of the malicious file in the directory.
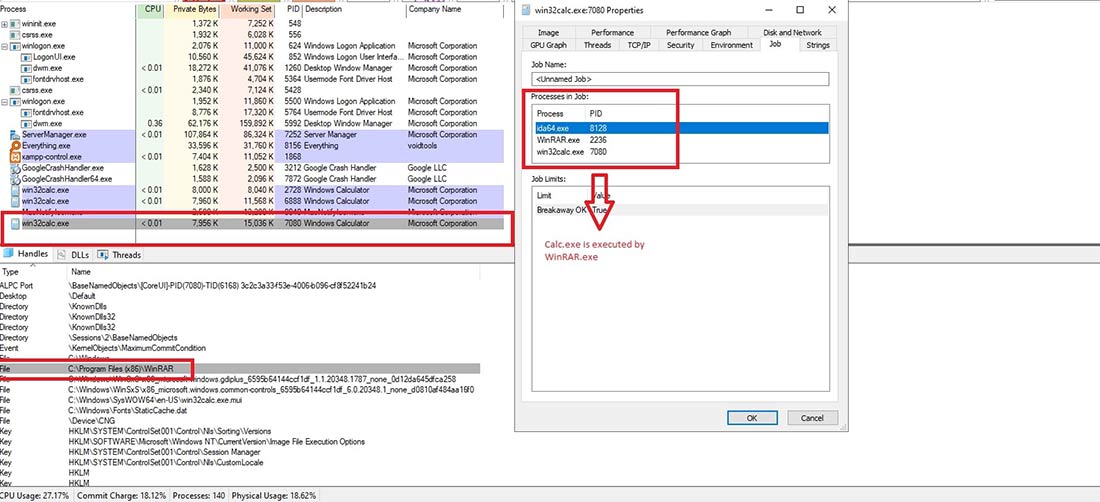 Figure 14: Remote code execution
Figure 14: Remote code execution
Patch Analysis:
We installed the patched version of “winRAR.exe” 6.23beta1. When we checked the diff between the function WinRAR.exe+sub_00CFFD30 and WinRAR.exe+sub_008544A0, we observed that WinRAR is setting flag.
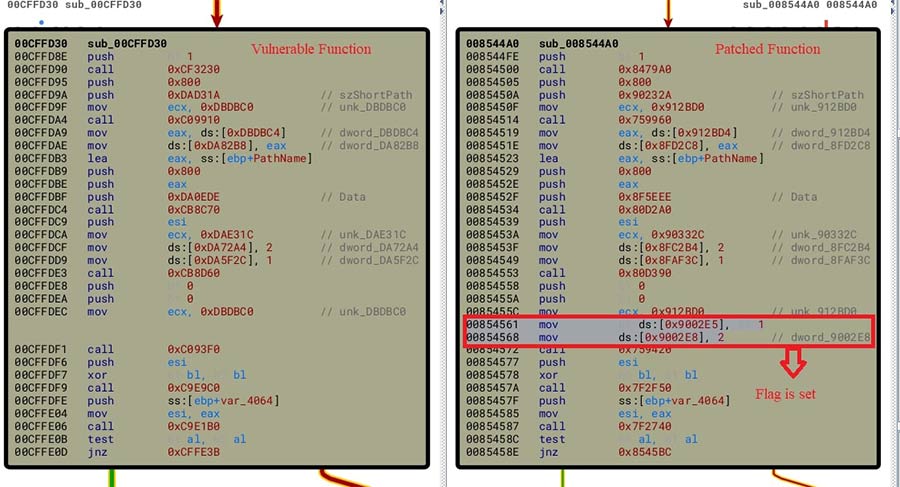 Figure 15: Patch diff between vulnerable and fixed version
Figure 15: Patch diff between vulnerable and fixed version
Later we decompiled the function WinRAR.exe+sub_008544a0. It shows the change in the code which handles how the “Temp” directory is used by the application.
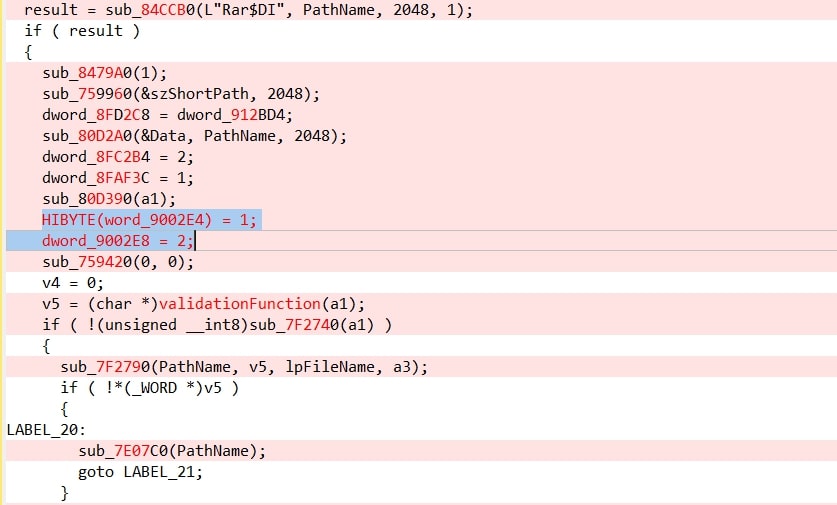 Figure 16: Decompiled code of fixed version
Figure 16: Decompiled code of fixed version
Later we looked for the application of dword_9002E4 and observed that this value is passed to a function WinRAR.exe+sub_831760.
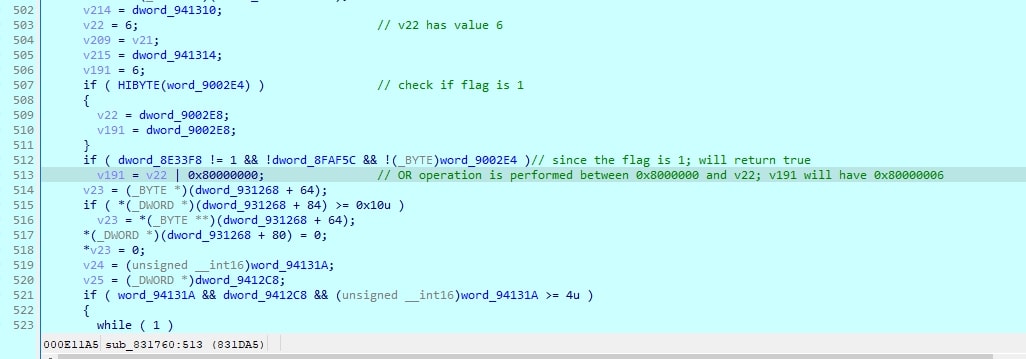 Figure 17: Usage of patched values
Figure 17: Usage of patched values
In this code, the application initially verifies whether the flag is set to 1. If it determines that the flag is indeed set, it proceeds dword_9002E4. This inspection prompts the application to perform a bitwise OR operation, causing V191 to assume the value 0x80000006. As this modified value is subsequently fed into the extraction function, it results in the failure of the vulnerable condition, triggering an exception and ultimately halting code execution.
Until now we have seen the impact and root cause of the vulnerability. To fix it, the most straightforward and effective way to mitigate this issue is to apply the RARLabs patches.
For the systems where applying a patch is not an option, Trellix provides coverage that can be used to detect and prevent the exploitation attempts of this vulnerability.
Product
Signature
Trellix IPS
0x452e4500: HTTP: WinRAR Remote Code Execution Vulnerability (CVE-2023-38831)
Endpoint Security (ENS)
413: Suspicious Double File Extension Execution
Endpoint Security (HX)
WINRAR-CVE-2023-38831 EXPLOITATION (EXPLOIT)
SUSPICIOUS PROCESS LAUNCHED BY WINRAR (METHODOLOGY)
ENS-AV
BAT/Agent.en BAT/Launcher.a
BAT/Agent.do
Trojan-FVVE
Trojan-FIGN
Generic backdoor.agx
Generic backdoor.agy
MVX
FEC_Trojan_ZIP_Generic_3
FE_Exploit_ZIP_CVE202338831_1
Conclusion:
In this blog post, we have delved into the details of CVE-2023-38831, a remote code execution vulnerability that is used to deliver malware and used in campaigns like APT28. We have explored the root cause of the vulnerability and discussed the exploitation method, as well as the security patch released by RARLabs to address the issue. Furthermore, using a vulnerable WinRAR version as an example, we have showcased the extent of this vulnerability through a malevolent PDF file. It’s important to note that any file type, be it JPG, DOC, TXT, and so on, can serve as bait. Furthermore, it’s possible to replace EXE with other executables like CMD, BAT, PS1, and more. To achieve a real remote code execution.
There are 500+ million users worldwide that are affected by this critical CVE, and it has also raised the importance of being continuously vigilant and remaining alert to emerging threats. Considering the exploitability and impact of CVE-2023-38831, the Trellix Advanced Research Center strongly urges all users to take necessary measures to protect themselves, including following best security practices, promptly applying security patches, and deploying the intrusion prevention products.
_ This document and the information contained herein describes computer security research for educational purposes only and the convenience of Trellix customers. _