
Critical WordPress Plugin Bug Afflicts 700K Sites
A popular WordPress plugin, which helps make websites compliant with the General Data Protection Regulation (GDPR), has issued fixes for a critical flaw. If exploited, the vulnerability could enable attackers to modify content or inject malicious JavaScript code into victim websites.
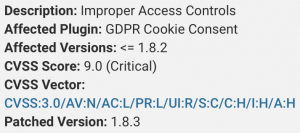
The plugin, GDPR Cookie Consent, which helps businesses display cookie banners to show that they are compliant with EU’s privacy regulation, has more than 700,000 active installations – making it a ripe target for attackers. The vulnerability, which does not yet have a CVE number, affects GDPR Cookie Consent version 1.8.2 and below. Earlier this week, after the developer was notified of the critical flaw, the GDPR Cookie Consent plugin was removed from the WordPress.org plugin directory “pending a full review” according to the plugin’s directory page. The new version, 1.8.3, was released by Cookie Law Info, the developer behind the plugin, on Feb. 10.
“There were a number of code changes, but those relevant to security include a capabilities check added to an AJAX endpoint used in the plugin’s administration pages,” according to researchers with Wordfence this week. While Wordfence disclosed details of the vulnerability, it was discovered by Jerome Bruandet, a security researcher with NinTechNet, who also detailed his findings in a Wednesday post.
The vulnerability stems from improper access controls in an endpoint used by the WordPress plugin’s AJAX API, a web development technique used to create web applications. That endpoint is the “_construct” method within the plugin, used for initializing code for newly created objects. Once actions are created they are sent via AJAX to the “_construct” method; however, this process fails to implement checks.
 Because of this, the AJAX endpoint, intended to only be accessible to administrators, actually also allowed subscriber-level users to perform a number of actions that can compromise the site’s security, researchers said. A subscriber is a user role in WordPress, usually the with very limited capabilities, including logging into the website and leaving comments.
Because of this, the AJAX endpoint, intended to only be accessible to administrators, actually also allowed subscriber-level users to perform a number of actions that can compromise the site’s security, researchers said. A subscriber is a user role in WordPress, usually the with very limited capabilities, including logging into the website and leaving comments.
The “_construct” method accepts three different values from the AJAX API. Two of them, save_contentdata and autosave_contant_data, can be leveraged for exploitation by an attacker.
The save_contentdata method is used to allow administrators to save the GDPR cookie notices to the database as a page post type. However, since this method is not checked, an authenticated user or a subscriber can modify any existing page or post (or the entire website), and take them offline by changing their status from “published” to “draft.”
“Additionally, it is possible to delete or change their content. Injected content can include formatted text, local or remote images as well as hyperlinks and shortcodes,” Bruandet said.
The other method, autosave_contant_data, is used to save GDPR cookie info page in the background while the admin is editing it, by saving the data into the cli_pg_content_data database field without validating it. However, the lack of checks for this method could allow an authenticated user to inject JavaScript code into the webpage. This code would then be loaded and executed each time someone visits the “http://example.com/cli-policy-preview/” page.
Researchers who discovered it urge WordPress plugin users to update as soon as possible: “This vulnerability has been fixed in version 1.8.3. We recommend that users immediately update to the latest version available,” according to Wordfence.
Learn how Operational Technology and Information Technology systems are merging and changing security playbooks in this free Threatpost Webinar. Join usWednesday, Feb. 19 at 2 p.m. ET** when a panel of OT and IT security experts will discuss how this growing trend is shaping security approaches for IoT and 5G rollouts. This webinar is for security and DevOps engineers, IoT edge developers and security executives.**
References
wordpress.org/
attendee.gotowebinar.com/register/2652328115100076035?source=art
blog.nintechnet.com/wordpress-gdpr-cookie-consent-plugin-fixed-vulnerability/
media.threatpost.com/wp-content/uploads/sites/103/2020/02/13152933/Wordfence-Critical-Bug-Rating.png
threatpost.com/ahead-of-gdpr-information-governance-comes-into-its-own/132209/
threatpost.com/newsletter-sign/
wordpress.org/plugins/cookie-law-info/
www.wordfence.com/blog/2020/02/improper-access-controls-in-gdpr-cookie-consent-plugin/
