Phony Instagram ‘Support Staff’ Emails Hit Insurance Company
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C
A phishing campaign used the guise of Instagram technical support to steal login credentials from employees of a prominent U.S. life insurance company headquartered in New York, researchers have revealed.
According to a report published by Armorblox on Wednesday, the attack combined brand impersonation with social engineering and managed to bypass Google’s email security by using a valid domain name, eventually reaching the mailboxes of hundreds of employees.
Scam Looked Identical to Instagram
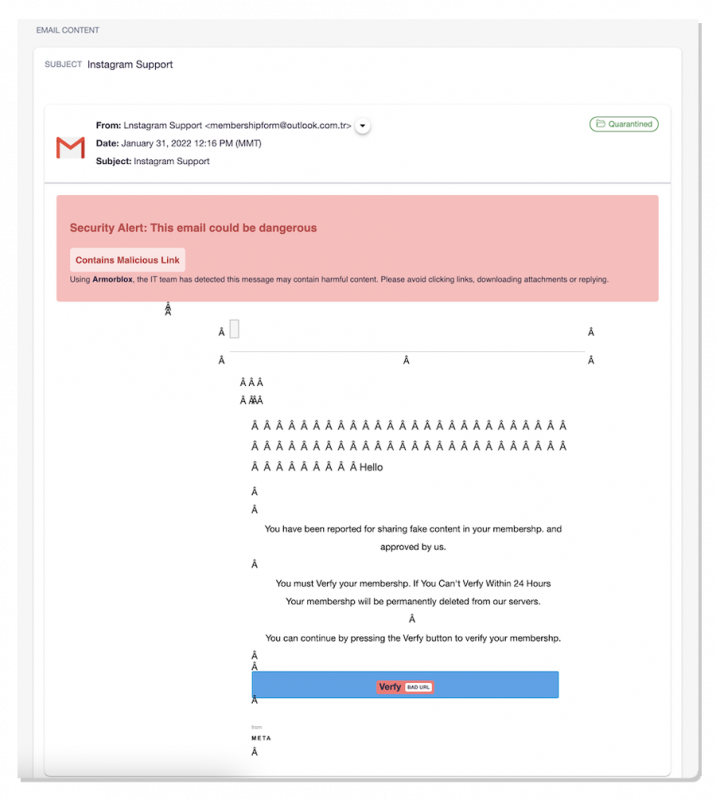
The attack began with a simple email. Disguised as an alert from Instagram’s technical support team, it indicated that the recipient’s account was under threat of deactivation. The intention, according to the report, was “to create a sense of urgency while instilling trust in the sender.”
“You have been reported for sharing fake content in your membership,” read the body of the email. “You must verify your membership. If you can’t verify within 24 hours your membership will be permanently deleted from our servers.” This message fostered a sense of urgency, to goad the unsuspecting into clicking on a malicious “account verify” link. Targets who did so ended up on a landing page, where they were asked to submit their Instagram account login information. That information would go straight to the malicious actor, of course, unbeknownst to the target themselves.
Instagram phishing email. Source: Armorblox.
At no point did any of these steps “look to be malicious to the common end user, and every touch point, from the email to the account verification form, include Meta and Instagram branding and logos,” the researchers noted.
The attackers certainly left clues along the way. They made grammar, spelling and capitalization errors in the body of the phishing email. In the sender field, the “I” in “Instagram Support” was, in fact, an “L.” And the email domain itself – [email protected] – clearly didn’t come from Instagram.
Still, the domain itself was perfectly legitimate – allowing it to bypass traditional spam filters – and, the researchers explained, “the sender crafted a long email address, meaning that many mobile users would only see the characters before the ‘@’ sign, which in this case is ‘membershipform’ – one that would not raise suspicion.”
How to Defend Yourself
Just a few weeks ago, cyberattackers impersonated the DocuSign e-signature software to steal Microsoft account credentials from a U.S. payment solutions company. In that case, too, hundreds of employees were exposed as a result of dutiful brand impersonation, clever social engineering and a valid email domain that bypassed traditional security measures.
Perhaps these two campaigns were identified and stopped, but what about the next one? Or the one after that? Or other campaigns we haven’t heard about, because they weren’t successfully identified by a security team?
Armorblox’s report suggested four main areas where employees can focus to protect themselves against phishing.****
- Avoid opening emails that you are not expecting *Augment native email security to stop socially engineered attacks *Watch out for targeted attacks *Follow multi-factor authentication and password management best practices
“To protect against these attacks, employees should be educated on the value of their email accounts,” wrote Erich Kron of KnowBe4, via email. “In addition, employees need to understand the danger of reusing passwords and using simple passwords to secure accounts both personally and within the organization.”
Even one employee’s slip-up can cause major problems across an organization, followed by other organizations along a supply chain. “Take caution when using business credentials to login across multiple apps,” wrote Armorblox researchers, “especially social apps that cross over into personal use. The convenience may be tempting; however, it only takes one time for both your sensitive personal and business data to risk exposure.”
_Moving to the cloud? Discover emerging cloud-security threats along with solid advice for how to defend your assets with our _FREE downloadable eBook, “Cloud Security: The Forecast for 2022.”****We explore organizations’ top risks and challenges, best practices for defense, and advice for security success in such a dynamic computing environment, including handy checklists.
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C