Free HermeticRansom Ransomware Decryptor Released
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C
A free decryptor is out to unlock a ransomware found piggybacking on the HermeticWiper data wiper malware that ESET and Broadcom’s Symantec discovered targeting machines at financial, defense, aviation and IT services outfits in Ukraine, Lithuania and Latvia last week.
The fact that there was ransomware clinging to the data-wiping malware didn’t surprise cybersecurity experts, of course. It was predicted by Katie Nickels, director of intel at Red Canary, for one: She tweeted that there was very likely a “broader intrusion chain.”
> As you’re reading this, note this point: adversaries likely had control of the AD server already. They were already in. There’s a broader intrusion chain beyond just the wiper, it just isn’t publicly known yet. I’m watching for any details on what happens BEFORE wiper deployment. <https://t.co/59SZTpTlXA>
>
> — Katie Nickels (@likethecoins) February 23, 2022
What might have been a bit more surprising was the welcome discovery, made by CrowdStrike’s Intelligence Team earlier this week, that HermeticRansom had a lame encryption process that let the ransomware’s tentacles be untangled.
Avast Threat Labs had spotted the new ransomware strain last Thursday, Feb. 24. Avast, which named the new strain HermeticRansom, on Thursday released a free decryptor that incorporated a decryption script CrowdStrike released to GitHub, a user-friendly GUI and a set of instructions on its use.
The decryptor can be downloaded here.
Crypto Likely Weakened by Coding Errors
HermeticRansom, aka PartyTicket, was identified at several victimized organizations, among other malware families that included what CrowdStrike called the “sophisticated” HermeticWiper, aka DriveSlayer.
Regardless of how sophisticated the wiper malware was, the ransomware that hopped a ride on it had less-than-stellar encryption, with a logic flaw in the encryption process that enabled researchers to break through, CrowdStrike said: “Analysis of the [PartyTicket/HermeticRansom] ransomware indicates it superficially encrypts files and does not properly initialize the encryption key, making the encrypted file with the associated .encryptedJB extension recoverable.”
At the time it published its report, CrowdStrike hadn’t traced the ransomware to a known threat actor. It didn’t quite seem like a serious attempt at ransomware, at any rate, researchers said, given the coding errors that made its encryption “breakable and slow.”
Either the malware author was unfamiliar with writing in Go or rushed its development without thoroughly testing it, analysts surmised.
Either way, it looked to analysts as if extortion wasn’t the primary aim: “The relative immaturity and political messaging of the ransomware, the deployment timing and the targeting of Ukrainian entities are consistent with its use as an additional payload alongside DriveSlayer activity, rather than as a legitimate ransomware extortion attempt,” they wrote.
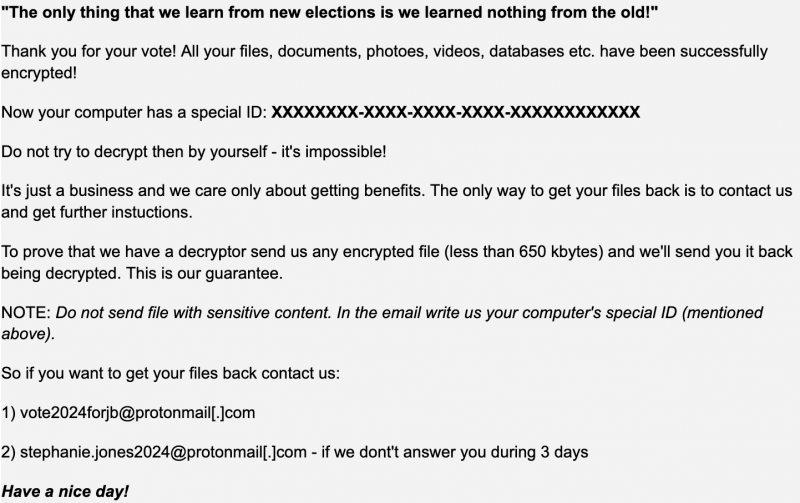
Below is a screen capture of HermeticRansom’s extortion note:
HermeticRansom ransomware demand note. Source: CrowdStrike Intelligence Team.
HermeticWiper History
HermeticWiper, discovered last week, has been used against hundreds of machines in Ukraine – attacks that followed distributed denial-of-service (DDoS) attacks launched against Ukraine websites on Feb. 23.
One of the HermeticWiper malware samples was compiled back on Dec. 28, pointing to the wiper attacks having been readied two months before Russia’s military assault.
HermeticWiper was only one of an onslaught of cyberattacks and malware that have been unleashed prior to and during the crisis, including the novel FoxBlade trojan, a wave of pre-invasion DDoS attacks in mid-February, plus another campaign of wiper attacks targeting Ukraine and aimed at eroding trust in January – just a few of an ongoing barrage of cyberattacks in the cyber warzone.
Register Today for Log4j Exploit: Lessons Learned and Risk Reduction Best Practices – a LIVEThreatpost eventsked for Thurs., March 10 at 2PM ET. Join Sonatype codeexpert Justin Young as he helps you sharpen code-hunting skills to reduce attacker dwell time. Learn why Log4j is still dangerous and how SBOMs fit into software supply-chain security. Register Now for this one-time FREE event, Sponsored by Sonatype.

References
bit.ly/3BXPL6S
bit.ly/3BXPL6S
decoded.avast.io/threatresearch/help-for-ukraine-free-decryptor-for-hermeticransom-ransomware/
decoded.avast.io/threatresearch/help-for-ukraine-free-decryptor-for-hermeticransom-ransomware/#howto
github.com/CrowdStrike/PartyTicketDecryptor
media.threatpost.com/wp-content/uploads/sites/103/2022/03/04105632/HermeticRansom-Ransom-note-e1646409408416.png
symantec-enterprise-blogs.security.com/blogs/threat-intelligence/ukraine-wiper-malware-russia
symantec-enterprise-blogs.security.com/blogs/threat-intelligence/ukraine-wiper-malware-russia
t.co/59SZTpTlXA
threatpost.com/destructive-wiper-ukraine/177768/
threatpost.com/microsoft-ukraine-foxblade-trojan-hours-before-russian-invasion/178702/
threatpost.com/microsoft-ukraine-foxblade-trojan-hours-before-russian-invasion/178702/
threatpost.com/ukraine-russia-cyber-warzone-splits-cyber-underground/178693/
threatpost.com/ukrainian-ddos-attacks-should-put-us-on-notice-researchers/178498/
twitter.com/AvastThreatLabs/status/1496663206634344449
twitter.com/ESETresearch/status/1496581903205511181
twitter.com/juanandres_gs/status/1496581710368358400
twitter.com/likethecoins/status/1496590297228357634?cxt=HBwWhMC9ica8-sQpAAAA&cn=ZmxleGlibGVfcmVjcw%3D%3D&refsrc=email
twitter.com/likethecoins/status/1496590297228357634?ref_src=twsrc%5Etfw
twitter.com/threatintel/status/1496578746014437376
www.crowdstrike.com/blog/how-to-decrypt-the-partyticket-ransomware-targeting-ukraine/
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C