Bug in Popular WinRAR Software Could Let Attackers Hack Your Computer
7.8 High
CVSS3
Attack Vector
LOCAL
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
4.6 Medium
CVSS2
Access Vector
LOCAL
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:L/AC:L/Au:N/C:P/I:P/A:P
A new security weakness has been disclosed in the WinRAR trialware file archiver utility for Windows that could be abused by a remote attacker to execute arbitrary code on targeted systems, underscoring how vulnerabilities in such software could beсome a gateway for a roster of attacks.
Tracked as CVE-2021-35052, the bug impacts the trial version of the software running version 5.70. “This vulnerability allows an attacker to intercept and modify requests sent to the user of the application,” Positive Technologies’ Igor Sak-Sakovskiy said in a technical write-up. “This can be used to achieve remote code execution (RCE) on a victim’s computer.”
The issue has since been addressed in WinRAR version 6.02 released on June 14, 2021.
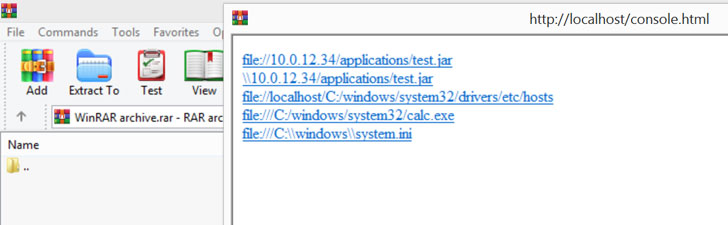
Sak-Sakovskiy noted that an investigation into WinRAR began after observing a JavaScript error rendered by MSHTML (aka Trident), a proprietary browser engine for the now-discontinued Internet Explorer and which is used in Office to render web content inside Word, Excel, and PowerPoint documents, leading to the discovery that the error window is displayed once every three times when the application is launched post the expiry of the trial.
By intercepting the response code sent when WinRAR alerts the user about the end of the free trial period via “notifier.rarlab[.]com” and modifying it to a “301 Moved Permanently” redirect message, Positive Technologies found that it could be abused to cache the redirection to an attacker-controlled malicious domain for all subsequent requests.
On top of that, an attacker already having access to the same network domain can stage ARP spoofing attacks to remotely launch applications, retrieve local host information, and even run arbitrary code.
“One of the biggest challenges an organization faces is the management of third-party software. Once installed, third-party software has access to read, write, and modify data on devices which access corporate networks,” Sak-Sakovskiy noted.
“It’s impossible to audit every application that could be installed by a user and so policy is critical to managing the risk associated with external applications and balancing this risk against the business need for a variety of applications. Improper management can have wide reaching consequences.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
7.8 High
CVSS3
Attack Vector
LOCAL
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
4.6 Medium
CVSS2
Access Vector
LOCAL
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:L/AC:L/Au:N/C:P/I:P/A:P