Critical Flaw Discovered in Cisco APIC for Switches — Patch Released
9.1 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
NONE
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N
6.4 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
NONE
AV:N/AC:L/Au:N/C:P/I:P/A:N
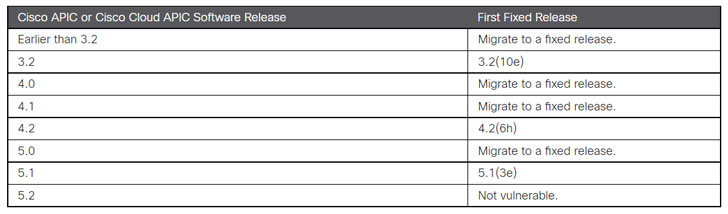
Cisco Systems on Wednesday issued patches to address a critical security vulnerability affecting the Application Policy Infrastructure Controller (APIC) interface used in its Nexus 9000 Series Switches that could be potentially abused to read or write arbitrary files on a vulnerable system.
Tracked as CVE-2021-1577 (CVSS score: 9.1), the issue — which is due to improper access control — could enable an unauthenticated, remote attacker to upload a file to the appliances. " A successful exploit could allow the attacker to read or write arbitrary files on an affected device," the company said in an advisory.
The APIC appliance is a centralized, clustered controller that programmatically automates network provisioning and control based on the application requirements and policies across physical and virtual environments.
Cisco said it discovered the vulnerability during internal security testing by the Cisco Advanced Security Initiatives Group (ASIG).
Additionally, the network equipment major said it concluded its investigation into a new BadAlloc flaw in BlackBerry’s QNX real-time operating system, reported on August 17 by the Canadian company. “Cisco has completed its investigation into its product line to determine which products may be affected by this vulnerability. No products are known to be affected,” it noted.
Cisco products that run QNX are listed below -
- Channelized shared port adapters (SPAs) (CSCvz34866)
- Circuit Emulation over Packet (CEoP) SPAs (CSCvz34865)
- IOS XR 32-bit Software (CSCvz34871)
- RF Gateway 10 (CSCvz34869)
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
9.1 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
NONE
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N
6.4 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
NONE
AV:N/AC:L/Au:N/C:P/I:P/A:N