US Agencies and FireEye Were Hacked Using SolarWinds Software Backdoor
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C
State-sponsored actors allegedly working for Russia have targeted the US Treasury, the Commerce Department’s National Telecommunications and Information Administration (NTIA), and other government agencies to monitor internal email traffic as part of a widespread cyberespionage campaign.
The Washington Post, citing unnamed sources, said the latest attacks were the work of APT29 or Cozy Bear, the same hacking group that’s believed to have orchestrated a breach of US-based cybersecurity firm FireEye a few days ago leading to the theft of its Red Team penetration testing tools.
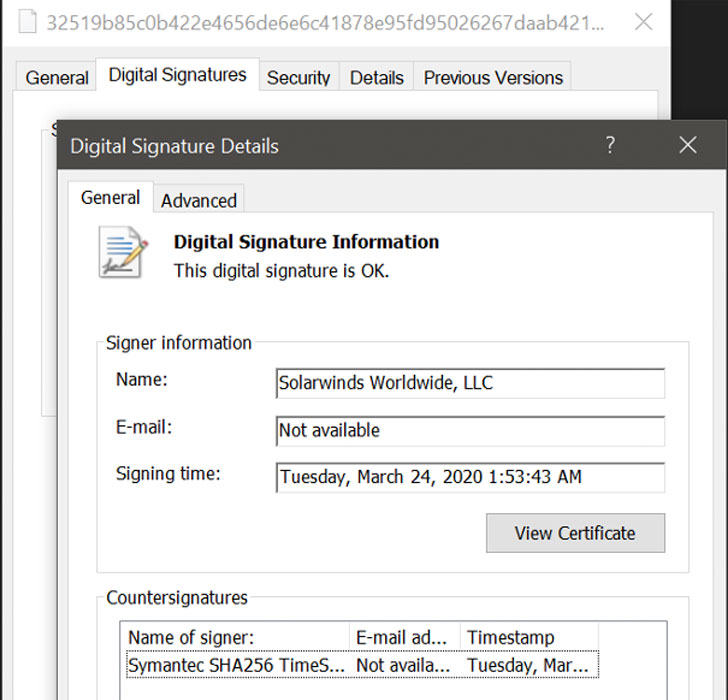
The motive and the full scope of what intelligence was compromised remains unclear, but signs are that adversaries tampered with a software update released by Texas-based IT infrastructure provider SolarWinds earlier this year to infiltrate the systems of government agencies as well as FireEye and mount a highly-sophisticated supply chain attack.
“The compromise of SolarWinds’ Orion Network Management Products poses unacceptable risks to the security of federal networks,” said Brandon Wales, acting director of the US Cybersecurity and Infrastructure Security Agency (CISA), which has released an emergency directive, urging federal civilian agencies to review their networks for suspicious activity and disconnect or power down SolarWinds Orion products immediately.
SolarWinds’ networking and security products are used by more than 300,000 customers worldwide, including Fortune 500 companies, government agencies, and education institutions.
It also serves several major US telecommunications companies, all five branches of the US Military, and other prominent government organizations such as the Pentagon, State Department, NASA, National Security Agency (NSA), Postal Service, NOAA, Department of Justice, and the Office of the President of the United States.
An Evasive Campaign to Distribute SUNBURST Backdoor
FireEye, which is tracking the ongoing intrusion campaign under the moniker “UNC2452,” said the supply chain attack takes advantage of trojanized SolarWinds Orion business software updates in order to distribute a backdoor called SUNBURST.
“This campaign may have begun as early as Spring 2020 and is currently ongoing,” FireEye said in a Sunday analysis. “Post compromise activity following this supply chain compromise has included lateral movement and data theft. The campaign is the work of a highly skilled actor and the operation was conducted with significant operational security.”
This rogue version of SolarWinds Orion plug-in, besides masquerading its network traffic as the Orion Improvement Program (OIP) protocol, is said to communicate via HTTP to remote servers so as to retrieve and execute malicious commands (“Jobs”) that cover the spyware gamut, including those for transferring files, executing files, profiling and rebooting the target system, and disabling system services.
Orion Improvement Program or OIP is chiefly used to collect performance and usage statistics data from SolarWinds users for product improvement purposes.
What’s more, the IP addresses used for the campaign were obfuscated by VPN servers located in the same country as the victim to evade detection.
Microsoft also corroborated the findings in a separate analysis, stating the attack (which it calls “Solorigate”) leveraged the trust associated with SolarWinds software to insert malicious code as part of a larger campaign.
“A malicious software class was included among many other legitimate classes and then signed with a legitimate certificate,” the Windows maker said. The resulting binary included a backdoor and was then discreetly distributed into targeted organizations."
SolarWinds Releases Security Advisory
In a security advisory published by SolarWinds, the company said the attack targets versions 2019.4 through 2020.2.1 of the SolarWinds Orion Platform software that was released between March and June 2020, while recommending users to upgrade to Orion Platform release 2020.2.1 HF 1 immediately.
The firm, which is currently investigating the attack in coordination with FireEye and the US Federal Bureau of Investigation, is also expected to release an additional hotfix, 2020.2.1 HF 2, on December 15, which replaces the compromised component and provides several extra security enhancements.
FireEye last week disclosed that it fell victim to a highly sophisticated foreign-government attack that compromised its software tools used to test the defenses of its customers.
Totaling as many as 60 in number, the stolen Red Team tools are a mix of publicly available tools (43%), modified versions of publicly available tools (17%), and those that were developed in-house (40%).
Furthermore, the theft also includes exploit payloads that leverage critical vulnerabilities in Pulse Secure SSL VPN (CVE-2019-11510), Microsoft Active Directory (CVE-2020-1472), Zoho ManageEngine Desktop Central (CVE-2020-10189), and Windows Remote Desktop Services (CVE-2019-0708).
The campaign, ultimately, appears to be a supply chain attack on a global scale, for FireEye said it detected this activity across several entities worldwide, spanning government, consulting, technology, telecom, and extractive firms in North America, Europe, Asia, and the Middle East.
The indicators of compromise (IoCs) and other relevant attack signatures designed to counter SUNBURST can be accessed here.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C