Cisco ASA Flaw Under Active Attack After PoC Exploit Posted Online
7.5 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
NONE
Availability Impact
NONE
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
5 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
NONE
Availability Impact
NONE
AV:N/AC:L/Au:N/C:P/I:N/A:N
A security vulnerability in Cisco Adaptive Security Appliance (ASA) that was addressed by the company last October, and again earlier this April, has been subjected to active in-the-wild attacks following the release of proof-of-concept (PoC) exploit code.
The PoC was published by researchers from cybersecurity firm Positive Technologies on June 24, following which reports emerged that attackers are chasing after an exploit for the bug.
“Tenable has also received a report that attackers are exploiting CVE-2020-3580 in the wild,” the cyber exposure company said.
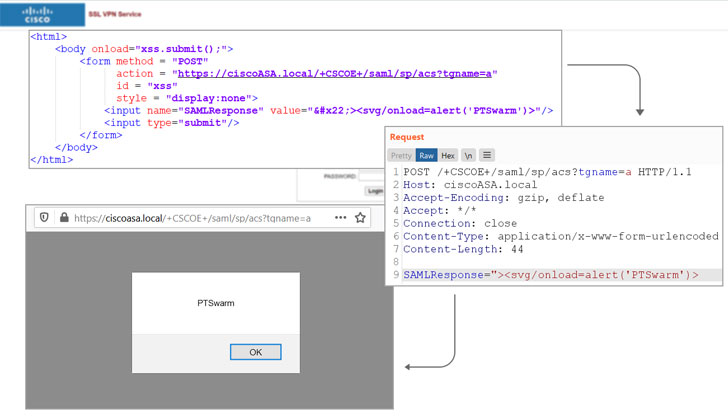
Tracked as CVE-2020-3580 (CVSS score: 6.1), the issue concerns multiple vulnerabilities in the web services interface of Cisco ASA software and Cisco Firepower Threat Defense (FTD) software that could allow an unauthenticated, remote attacker to conduct cross-site scripting (XSS) attacks on an affected device.
As of July 2020, there were a little over 85,000 ASA/FTD devices, 398 of which are spread across 17% of the Fortune 500 companies, according to cybersecurity company Rapid7.
Successful exploitation, such as scenarios where a user of the interface is convinced to click a specially-crafted link, could permit the adversary to execute arbitrary JavaScript code in the context of the interface or access sensitive, browser-based information.
Although Cisco remediated the flaw in October 2020, the network equipment company subsequently determined the fix to be “incomplete,” thereby requiring a second round of patches that were released on April 28, 2021.
In light of public PoC availability, it’s recommended that organizations prioritize patching CVE-2020-3580 to mitigate the risk associated with the flaw.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
7.5 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
NONE
Availability Impact
NONE
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
5 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
NONE
Availability Impact
NONE
AV:N/AC:L/Au:N/C:P/I:N/A:N