Google Releases Urgent Chrome Update to Patch Actively Exploited Zero-Day Flaw
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
6.8 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:P/I:P/A:P
Google on Thursday shipped emergency patches to address two security issues in its Chrome web browser, one of which it says is being actively exploited in the wild.
Tracked as CVE-2022-1364, the tech giant described the high-severity bug as a case of type confusion in the V8 JavaScript engine. Clément Lecigne of Google’s Threat Analysis Group has been credited with reporting the flaw on April 13, 2022.
As is typically the case with actively exploited zero-day flaws, the company acknowledged it’s “aware that an exploit for CVE-2022-1364 exists in the wild.” Additional details about the flaw and the identity of the threat actors have been withheld to prevent further abuse.
With the latest fix, Google has patched a total of three zero-day vulnerabilities in Chrome since the start of the year. It’s also the second type confusion-related bug in V8 to be squashed in less than a month -
- CVE-2022-0609 - Use-after-free in Animation
- CVE-2022-1096 - Type confusion in V8
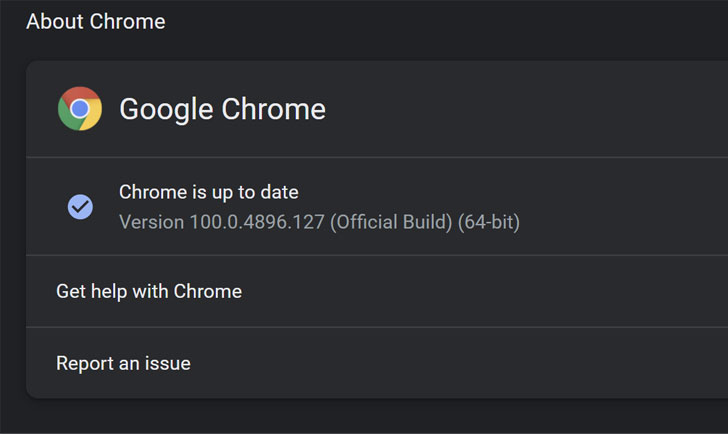
Users are recommended to update to version 100.0.4896.127 for Windows, macOS, and Linux to thwart potential threats. Users of Chromium-based browsers such as Microsoft Edge, Brave, Opera, and Vivaldi are also advised to apply the fixes as and when they become available.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
6.8 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:P/I:P/A:P