Linphone SIP Stack Bug Could Let Attackers Remotely Crash Client Devices
7.5 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H
5 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:N/I:N/A:P
Cybersecurity researchers on Tuesday disclosed details about a zero-click security vulnerability in the Linphone Session Initiation Protocol (SIP) stack that could be remotely exploited without any action from a victim to crash the SIP client and cause a denial-of-service (DoS) condition.
Tracked as CVE-2021-33056 (CVSS score: 7.5), the issue concerns a NULL pointer dereference vulnerability in the “belle-sip” component, a C-language library used to implement SIP transport, transaction, and dialog layers, with all versions prior to 4.5.20 affected by the flaw. The weakness was discovered and reported by industrial cybersecurity company Claroty.
Linphone is an open-source and cross-platform SIP client with support for voice and video calls, end-to-end encrypted messaging, and audio conference calls, among others. SIP, on the other hand, is a signaling protocol used for initiating, maintaining, and terminating real-time multimedia communication sessions for voice, video, and messaging applications over the internet.
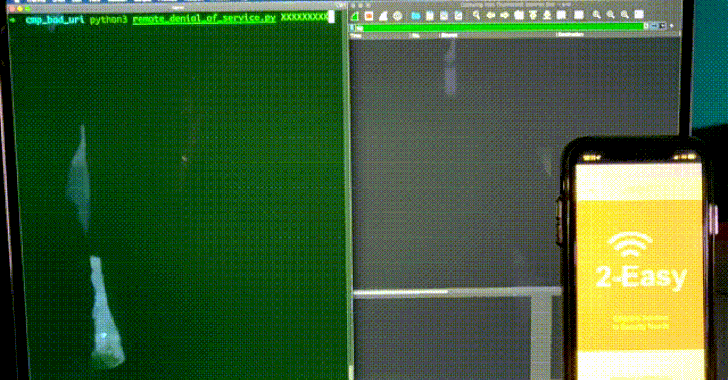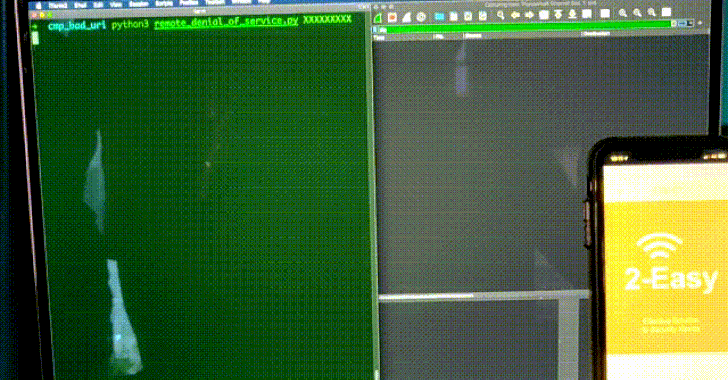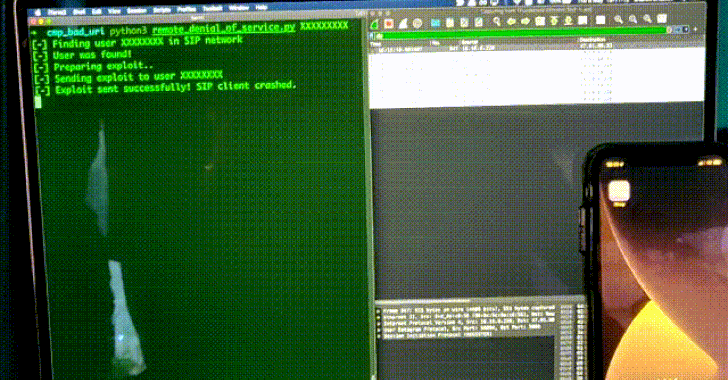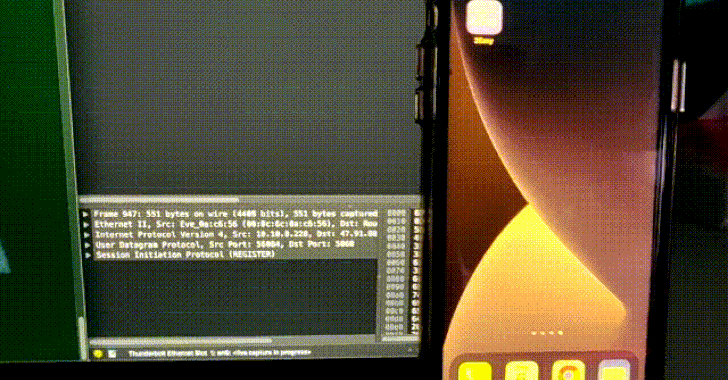
To that end, the remotely exploitable vulnerability can be activated by adding a malicious forward slash (“</”) to a SIP message header such as To (the call recipient), From (initiator of the call), or Diversion (redirect the destination endpoint), resulting in a crash of the SIP client application that uses the belle-sip library to handle and parse SIP messages.
“The underlying bug here is that non-SIP URIs are accepted as valid SIP header values,” Claroty researcher Sharon Brizinov said in a write-up. “Therefore, a generic URI such as a simple single forward slash will be considered a SIP URI. This means that the given URI will not contain a valid SIP scheme (scheme will be NULL), and so when the [string] compare function is called with the non-existent scheme (NULL), a null pointer dereference will be triggered and crash the SIP client.”
It’s worth noting that the flaw is also a zero-click vulnerability as it’s possible to cause the SIP client to crash simply by sending an INVITE SIP request with a specially-crafted From/To/Diversion header. As a consequence, any application that uses belle-sip to analyze SIP messages will be rendered unavailable upon receiving a malicious SIP “call.”
Although the patches are available for the core protocol stack, it’s essential that the updates are applied downstream by vendors that rely on the affected SIP stack in their products.
“Successful exploits targeting IoT vulnerabilities have demonstrated they can provide an effective foothold onto enterprise networks,” Brizinov said. “A flaw in a foundational protocol such as the SIP stack in VoIP phones and applications can be especially troublesome given the scale and reach shown by attacks against numerous other third-party components used by developers in software projects.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
7.5 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H
5 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:N/I:N/A:P