Google Details iOS, Chrome, IE Zero-Day Flaws Exploited Recently in the Wild
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
6.8 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:P/I:P/A:P
Threat intelligence researchers from Google on Wednesday shed more light on four in-the-wild zero-days in Chrome, Safari, and Internet Explorer browsers that were exploited by malicious actors in different campaigns since the start of the year.
What’s more, three of the four zero-days were engineered by commercial providers and sold to and used by government-backed actors, contributing to an uptick in real-world attacks. The list of now-patched vulnerabilities is as follows -
- CVE-2021-1879: Use-After-Free in QuickTimePluginReplacement (Apple WebKit)
- CVE-2021-21166: Chrome Object Lifecycle Issue in Audio
- CVE-2021-30551: Chrome Type Confusion in V8
- CVE-2021-33742: Internet Explorer out-of-bounds write in MSHTML
Both Chrome zero-days — CVE-2021-21166 and CVE-2021-30551 — are believed to have been used by the same actor, and were delivered as one-time links sent via email to targets located in Armenia, with the links redirecting unsuspecting users to attacker-controlled domains that masqueraded as legitimate websites of interest to the recipients.
The malicious websites took charge of fingerprinting the devices, including collecting system information about the clients, before delivering a second-stage payload.
When Google rolled out a patch for CVE-2021-30551, Shane Huntley, Director of Google’s Threat Analysis Group (TAG), revealed that the vulnerability was leveraged by the same actor that abused CVE-2021-33742, an actively exploited remote code execution flaw in Windows MSHTML platform that was addressed by Microsoft as part of its Patch Tuesday update on June 8.
The two zero-days were provided by a commercial exploit broker to a nation-state adversary, which used them in limited attacks against targets in Eastern Europe and the Middle East, Huntley previously added.
Now according to a technical report published by the team, all the three zero-days were “developed by the same commercial surveillance company that sold these capabilities to two different government-backed actors,” adding the Internet Explorer flaw was used in a campaign targeting Armenian users with malicious Office documents that loaded web content within the web browser.
Google did not disclose the identities of the exploit broker or the two threat actors that used the vulnerabilities as part of their attacks.
SolarWinds Hackers Exploited iOS Zero-Day
The Safari zero-day, in contrast, concerned a WebKit flaw that could enable adversaries to process maliciously crafted web content that may result in universal cross-site scripting attacks. The issue was rectified by Apple on March 26, 2021.
Attacks leveraging CVE-2021-1879, which Google attributed to a “likely Russian government-backed actor,” were executed by means of sending malicious links to government officials over LinkedIn that, when clicked from an iOS device, redirected the user to a rogue domain that served the next-stage payloads.
It’s worth noting that the offensive also mirrors a wave of targeted attacks unleashed by Russian hackers tracked as Nobelium, which was found abusing the vulnerability to strike government agencies, think tanks, consultants, and non-governmental organizations as part of an email phishing campaign.
Nobelium, a threat actor linked to the Russian Foreign Intelligence Service (SVR), is also suspected of orchestrating the SolarWinds supply chain attack late last year. It’s known by other aliases such as APT29, UNC2452 (FireEye), SolarStorm (Unit 42), StellarParticle (Crowdstrike), Dark Halo (Volexity), and Iron Ritual (Secureworks).
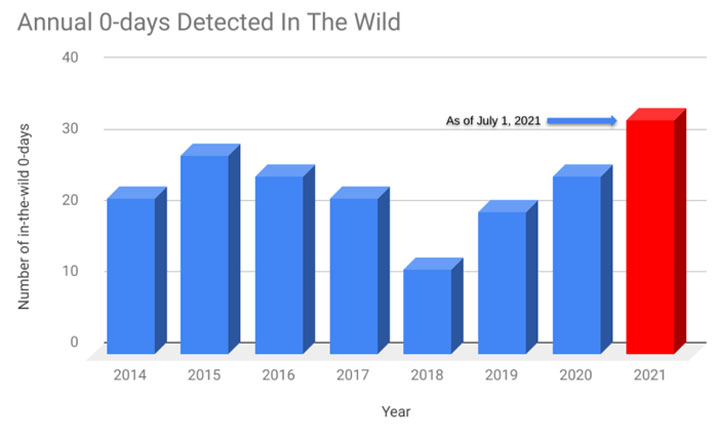
“Halfway into 2021, there have been 33 zero-day exploits used in attacks that have been publicly disclosed this year — 11 more than the total number from 2020,” TAG researchers Maddie Stone and Clement Lecigne noted. “While there is an increase in the number of zero-day exploits being used, we believe greater detection and disclosure efforts are also contributing to the upward trend.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
6.8 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:P/I:P/A:P