TrickBot Malware Abusing MikroTik Routers as Proxies for Command-and-Control
9.1 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
NONE
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N
6.4 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
NONE
AV:N/AC:L/Au:N/C:P/I:P/A:N
Microsoft on Wednesday detailed a previously undiscovered technique put to use by the TrickBot malware that involves using compromised Internet of Things (IoT) devices as a go-between for establishing communications with the command-and-control (C2) servers.
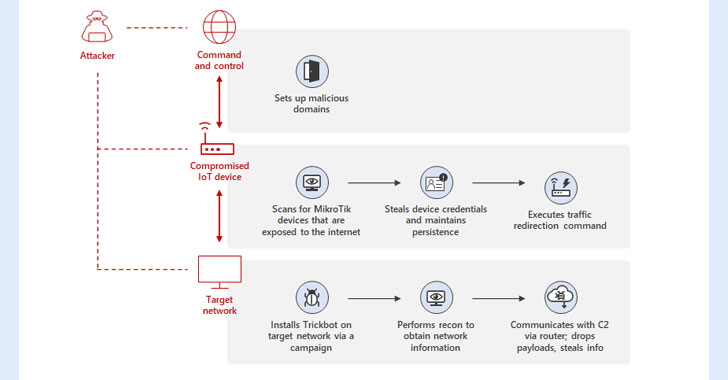
“By using MikroTik routers as proxy servers for its C2 servers and redirecting the traffic through non-standard ports, TrickBot adds another persistence layer that helps malicious IPs evade detection by standard security systems,” Microsoft’s Defender for IoT Research Team and Threat Intelligence Center (MSTIC) said.
TrickBot, which emerged as a banking trojan in 2016, has evolved into a sophisticated and persistent threat, with its modular architecture enabling it to adapt its tactics to suit different networks, environments, and devices as well as offer access-as-a-service for next-stage payloads like Conti ransomware.
The expansion to TrickBot’s capabilities comes amid reports of its infrastructure going offline, even as the botnet has continually refined its features to make its attack framework durable, evade reverse engineering, and maintain the stability of its C2 servers.
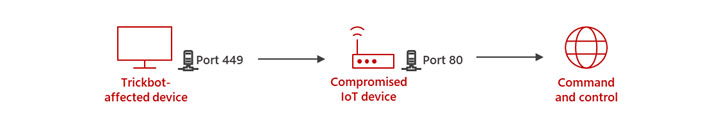
Specifically, the new method identified by MSTIC involves leveraging hacked IoT devices such as routers from MikroTik to “create a line of communication between the TrickBot-affected device and the C2 server.”
This also entails breaking into the routers by using a combination of methods, namely default passwords, brute-force attacks, or exploiting a now-patched flaw in MikroTik RouterOS (CVE-2018-14847), followed by changing the router’s password to maintain access.
In the next step, the attackers then issue a network address translation (NAT) command that’s designed to redirect traffic between ports 449 and 80 in the router, establishing a path for the TrickBot-infected hosts to communicate with the C2 server.
While potential connections between TrickBot and compromised MikroTik hosts were hinted before in November 2018, this is the first time the exact modus operandi has been laid bare open. With the malware reaching its limits last month and no new C2 servers registered since December 2021, it remains to be seen how the malware authors intend to take the operation forward.
“As security solutions for conventional computing devices continue to evolve and improve, attackers will explore alternative ways to compromise target networks,” the researchers said. “Attack attempts against routers and other IoT devices are not new, and being unmanaged, they can easily be the weakest links in the network.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
9.1 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
NONE
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N
6.4 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
NONE
AV:N/AC:L/Au:N/C:P/I:P/A:N